Dependency confusion is changing into a severe cybersecurity menace. Study which organizations are in danger and learn how to shield programs towards these assaults.

Software growth usually requires the combination of third-party or open-source dependencies for environment friendly performance and help of different options. Nonetheless, there’s now a purpose for safety professionals to be involved about dependencies, as attackers can introduce malicious codes into functions by them.
Dependency confusion assaults are comparatively new, although these cybersecurity threats have already proven they will trigger an excessive amount of havoc to organizations. We share specifics from new safety analysis about dependency confusion assaults, in addition to clarify how these assaults work, who’s most in danger and learn how to mitigate them.
Leap to:
The state of dependency confusion assaults
New analysis from OX Safety, a DevOps software program provide chain safety firm, revealed that the majority functions with a couple of billion customers and greater than 50% of functions with 30 million customers are utilizing dependencies which are susceptible to dependency confusion assaults. The analysis additionally confirmed that organizations in danger usually tend to have 73% of their property uncovered to dependency confusion assaults.
The OX Safety report’s findings are much like a report earlier this 12 months from Orca Safety that discovered about 49% of organizations are susceptible to a dependency confusion assault.
Examples of dependency confusion assaults
One notable instance of a dependency confusion assault is the PyTorch malicious dependency bundle reported by PyTorch in December 2022. The group warned customers of a attainable compromise of their Python Package deal Index code repository. On this incident, attackers put in a malicious dependency on their PyPI code repository and ran a malicious binary to allow them to launch a provide chain assault.
One other associated incident occurred in 2022 when an attacker injected malicious code into the favored open-source bundle node-ipc. Throughout the interval of this incident, hundreds of thousands of information had been wiped from computer systems situated in Russia and Belarus.
What’s a dependency confusion assault?
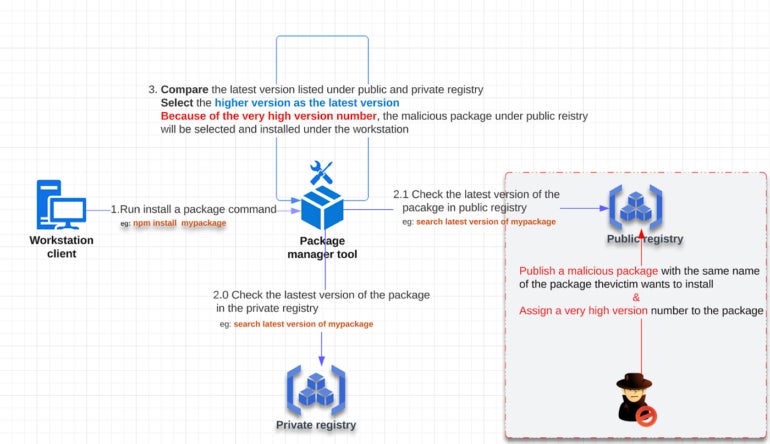
In a dependency confusion assault, the attacker uploads a software program bundle with the identical identify as an genuine one in your personal repository to a public bundle repository. Having a software program bundle with the identical identify in each personal and public repositories can trick builders into utilizing a malicious model of the bundle. When builders mistakenly fall for this or their bundle managers search the general public repositories for dependency packages, their reputable app may set up malicious code that the hacker can exploit to launch an assault.
Dependency confusion is a type of provide chain situation. This matter attracted consideration in 2021 when safety researcher Alex Birsan disclosed in a Medium submit that he breached greater than 35 main firms, together with Apple, Microsoft, Yelp and PayPal, utilizing dependency confusion methods.
Technical particulars of how dependency confusion assaults work
For dependency confusion to work, the hacker first identifies a bundle identify within the personal repository and registers the identical bundle identify within the public repository in order that when a brand new replace to the appliance is put in, it hooks with the malicious model on the general public registry as a substitute of the secure one within the personal registry.
Chatting with TechRepublic, OX Safety CEO and Co-Founder Neatsun Ziv defined that as a result of hackers perceive that the majority software bundle managers, equivalent to npm, pip and RubyGems, examine for dependencies on the general public code repository earlier than the personal registry, they attempt to register the identical bundle names in your personal registry on the general public registry. As an example, if a developer desires to put in a bundle hosted on their personal or inside repository however can’t attain the personal repository the place it’s saved, the developer’s dependency supervisor will try to discover a equally named bundle on a public registry and use that as a substitute.
Determine A
Who may be impacted by dependency confusion assaults?
OX Safety’s research, which examined greater than 54,000 repositories in over 1,000 organizations throughout a variety of sectors, together with fintech, media and SaaS firms, discovered that organizations of all sizes are uncovered to dependency confusion assaults. Ziv defined that the majority organizations are in danger as a result of they use susceptible packages or free-to-register public registries, that are susceptible to dependency confusion assaults.
“These findings of our newest analysis are deeply disturbing, as a majority of these assaults not solely compromise the integrity and safety of organizational property, however they probably impression these organizations’ workers and customers globally. Furthermore, the truth that when a corporation is in danger, a staggering 73% of their property are susceptible actually sheds gentle on simply how uncovered many organizations, no matter measurement or trade, actually are,” stated Ziv.
Learn how to forestall dependency confusion assaults
Based on Ziv, the best means to stop dependency confusion is to order personal bundle names within the public registry so no one can register them within the public registry. Software program builders can do that by going to bundle supervisor websites equivalent to npm, in the event that they’re utilizing JavaScript, after which creating their account and registering the bundle identify. By doing this, builders can forestall the assault on the supply (i.e., the general public repository) whereas additionally limiting the variety of human error dangers that expose their initiatives to dependency confusion assaults. A few of these human error dangers embody the shortage of enough code assessment, misconfigured construct programs, lack of safety greatest practices and unvalidated exterior dependencies.
One other manner builders can take care of dependency confusion is by validating the bundle supply earlier than putting in new packages or updating to an up to date model. Fortuitously, many bundle managers will let you view a bundle earlier than putting in it.
Software program builders also can forestall dependency confusion by utilizing bundle managers that permit using prefixes, IDs or namespaces when naming their packages. This observe ensures that inside dependencies are fetched from personal repositories.
