
A beforehand unknown marketing campaign involving the Hotabot botnet malware has focused Spanish-speaking customers in Latin America since no less than November 2020, infecting them with a banking trojan and spam software.
The malware permits the operators to take management of the sufferer’s Gmail, Outlook, Hotmail, or Yahoo electronic mail accounts, steal electronic mail information and 2FA codes arriving within the inbox, and ship phishing emails from the compromised accounts.
The brand new Horabot operation was found by analysts at Cisco Talos, who report that the menace actor behind it’s possible primarily based in Brazil.
Begins with phishing
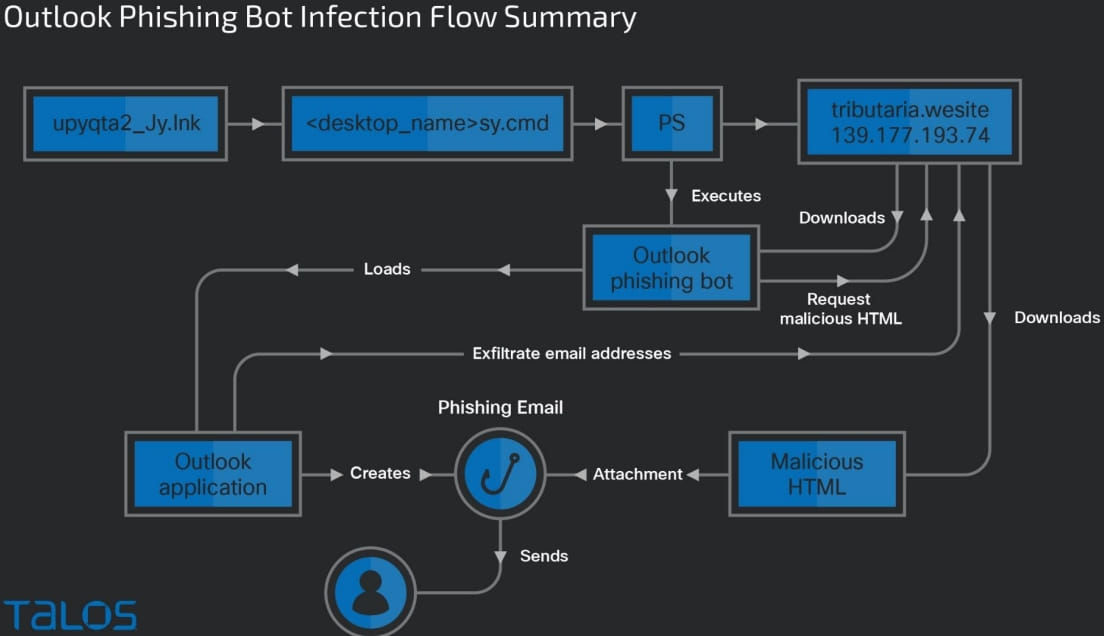
The multi-stage an infection chain begins with a tax-themed phishing electronic mail despatched to the goal, with an HTML attachment that’s supposedly a fee receipt.
Opening the HTML launches a URL redirection chain that lands the sufferer on an HTML web page hosted on an attacker-controlled AWS occasion.
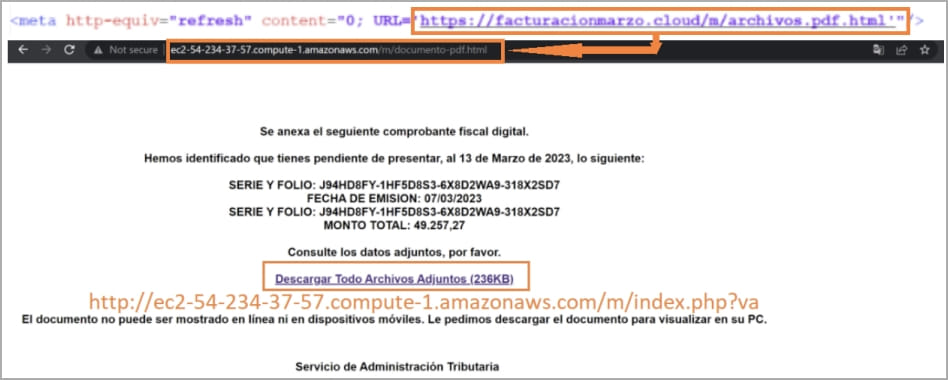
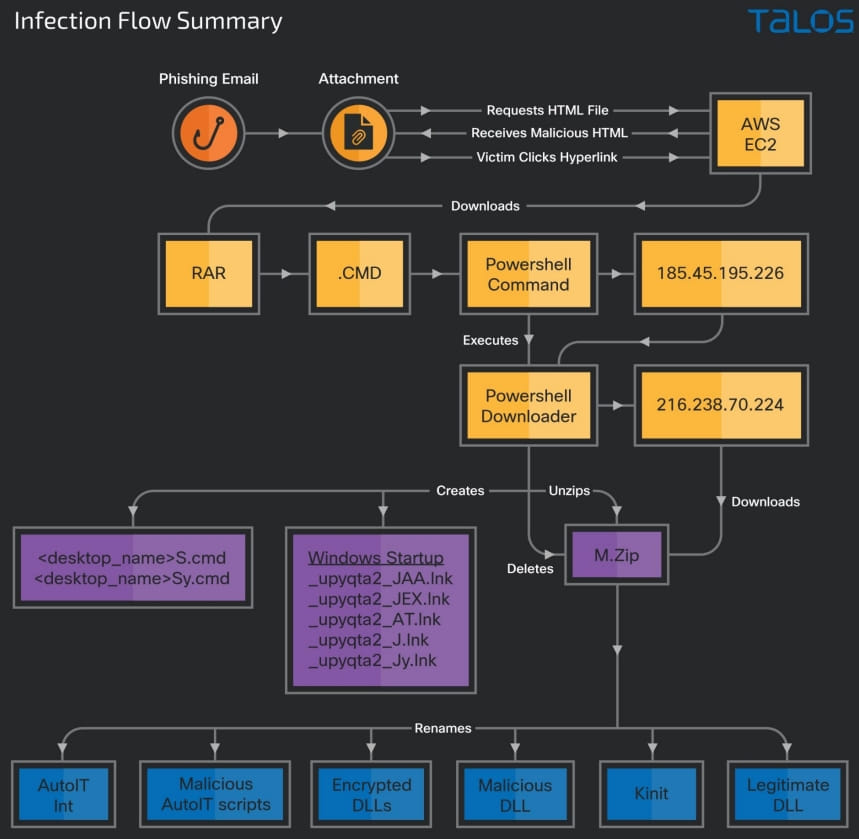
The sufferer clicks on the hyperlink on the web page and downloads a RAR archive that comprises a batch file with a CMD extension, which downloads a PowerShell script that fetches trojan DLLs and a set of reputable executables from the C2 server.
These trojans execute to fetch the ultimate two payloads from a unique C2 server. One is a PowerShell downloader script, and the opposite is the Horabot binary.
Banking trojan
One of many DLL recordsdata within the downloaded ZIP, “jli.dll,” which is sideloaded by the “kinit.exe” executable, is a banking trojan written in Delphi.
It targets system information (language, disk dimension, antivirus software program, hostname, OS model, IP handle), consumer credentials, and exercise information.
Furthermore, the trojan additionally gives its operators distant entry capabilities like performing file actions and may also conduct keylogging, screenshot snapping, and mouse occasion monitoring.
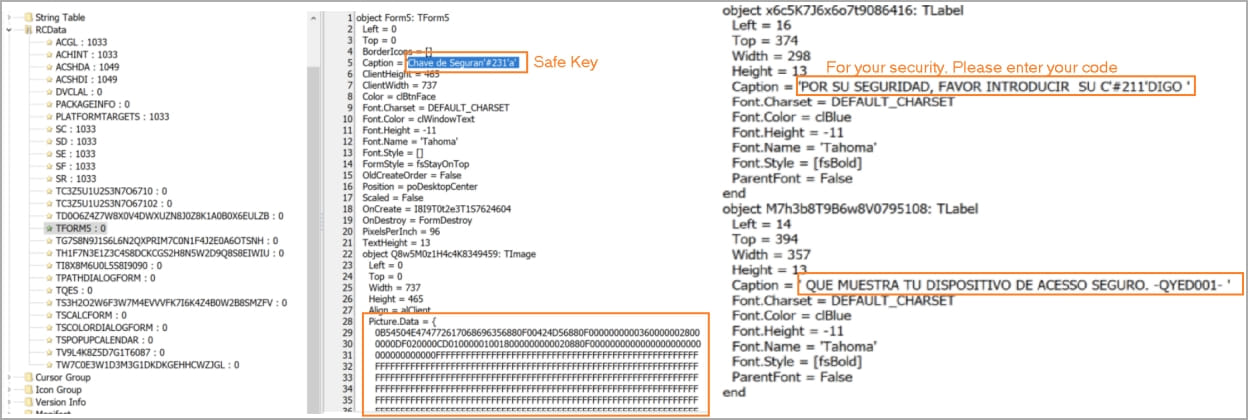
When the sufferer opens an software, the trojan overlays a pretend window on prime of it to trick victims into getting into delicate information like on-line banking account credentials or one-time codes.
All data collected from the sufferer’s laptop is shipped to the attacker’s command and management server by way of HTTP POST requests.
Cisco explains that the trojan has a number of built-in anti-analysis mechanisms to forestall it from operating in sandboxes or alongside debuggers.
The ZIP archive additionally comprises an encrypted spam software DLL named “_upyqta2_J.mdat,” designed to steal credentials for fashionable webmail companies like Gmail, Hotmail, and Yahoo.
As soon as the credentials are compromised, the software takes over the sufferer’s electronic mail account, generates spam emails, and sends them to the contacts discovered within the sufferer’s mailbox, furthering the an infection considerably randomly.
This software additionally options keylogging, screenshot snapping, and mouse occasion interception or monitoring capabilities, functionally overlapping with the banking trojan, presumably for redundancy.
Horabot
The first payload dropped onto the sufferer’s system is Horabot, a documented PowerShell-based botnet that targets the sufferer’s Outlook mailboxes to steal contacts and disseminate phishing emails containing malicious HTML attachments.
The malware launches the sufferer’s desktop Outlook software to scrutinize the handle e-book and contacts from the mailbox contents.
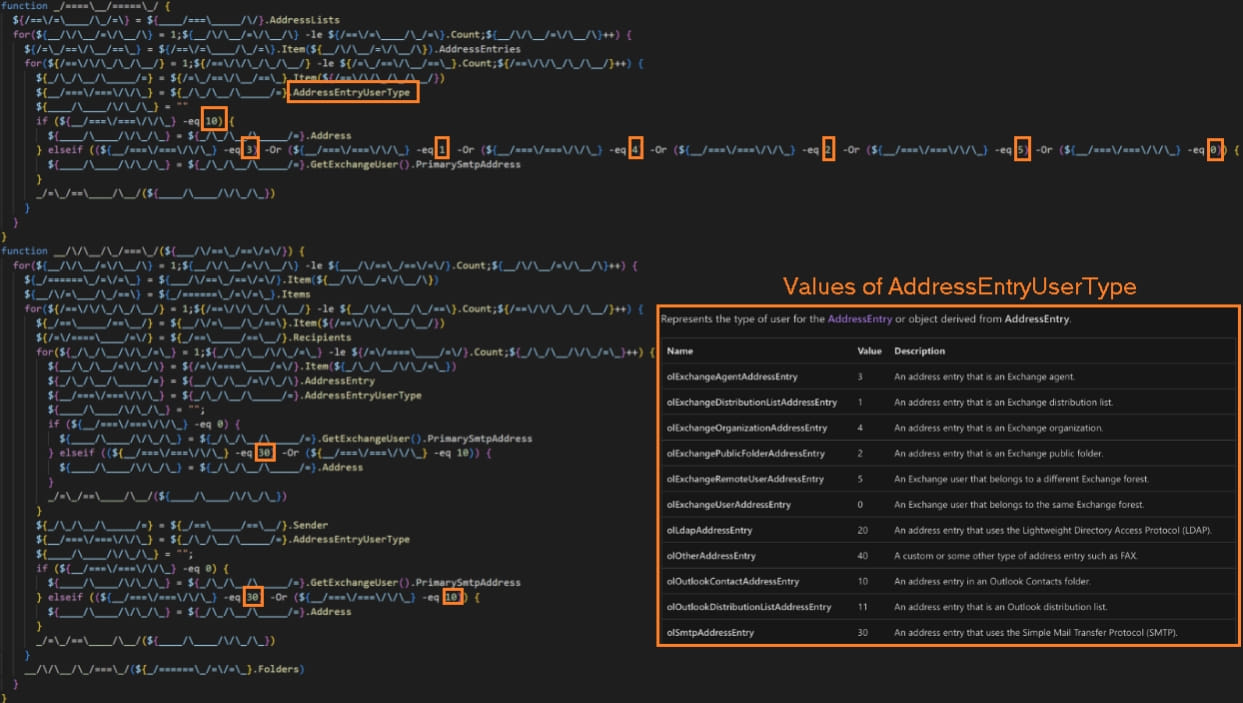
“After initialization, the [Horabot] script seems to be for the Outlook information recordsdata from the sufferer profile’s Outlook software information folder,” explains Cisco within the report.
“It enumerates all folders and emails within the sufferer’s Outlook information file and extracts electronic mail addresses from the emails’ sender, recipients, CC, and BCC fields.”
All extracted electronic mail addresses are written into an “.Outlook” file after which encoded and exfiltrated to the C2 server.
Lastly, the malware creates an HTML file domestically, fills it with content material copied from an exterior useful resource, and sends phishing emails to all extracted electronic mail addresses individually.
When the phishing electronic mail distribution course of is completed, the domestically created recordsdata and folders are deleted to wipe any traces.
Though this Horabot marketing campaign primarily targets customers in Mexico, Uruguay, Brazil, Venezuela, Argentina, Guatemala, and Panama, the identical or collaborating menace actors may broaden its attain to different markets anytime, utilizing phishing themes written in English.
