Researchers have issued a warning about an rising and superior type of voice phishing (vishing) generally known as “Letscall.” This method is at present focusing on people in South Korea.
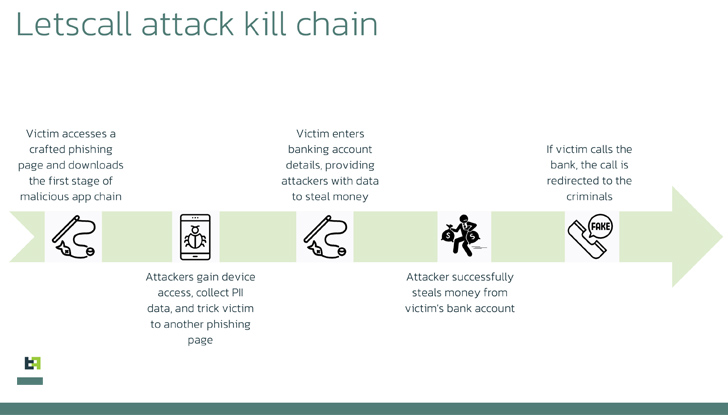
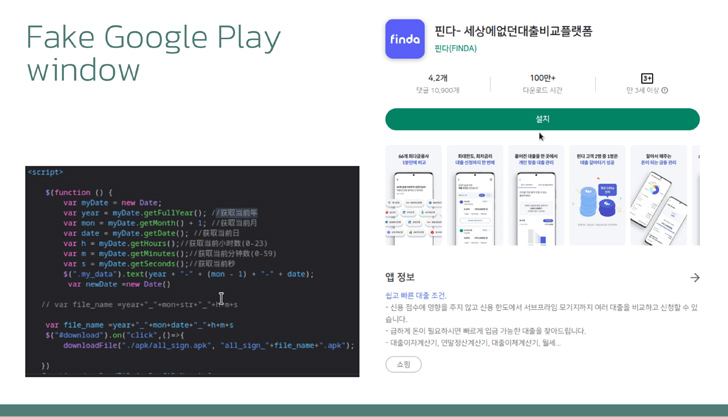
The criminals behind “Letscall” make use of a multi-step assault to deceive victims into downloading malicious apps from a counterfeit Google Play Retailer web site.
As soon as the malicious software program is put in, it redirects incoming calls to a name middle below the management of the criminals. Skilled operators posing as financial institution workers then extract delicate data from unsuspecting victims.
To facilitate the routing of voice site visitors, “Letscall” makes use of cutting-edge applied sciences similar to voice over IP (VOIP) and WebRTC. It additionally makes use of Session Traversal Utilities for NAT (STUN) and Traversal Utilizing Relays round NAT (TURN) protocols, together with Google STUN servers, to make sure high-quality telephone or video calls and bypass NAT and firewall restrictions.
The “Letscall” group consists of Android builders, designers, frontend and backend builders, in addition to name operators specializing in voice social engineering assaults.
The malware operates in three levels: first, a downloader app prepares the sufferer’s gadget, paving the way in which for the set up of highly effective spy ware. This spy ware then triggers the ultimate stage, which permits the rerouting of incoming calls to the attackers’ name middle.
“The third stage has its personal set of instructions, which additionally consists of Net socket instructions. A few of these instructions relate to the manipulation of the deal with e-book, similar to creating and eradicating contacts. Different instructions relate to creating, modifying, and eradicating the filters that decide which calls ought to be intercepted and which ought to be ignored,” Dutch cell safety agency ThreatFabric stated in its report.
What units “Letscall” aside is its utilization of superior evasion strategies. The malware incorporates Tencent Legu and Bangcle (SecShell) obfuscation through the preliminary obtain. In later levels, it employs advanced naming buildings in ZIP file directories and deliberately corrupts the manifest to confuse and bypass safety techniques.
Criminals have developed techniques that robotically name victims and play pre-recorded messages to additional deceive them. By combining cell phone infections with vishing strategies, these fraudsters can request micro-loans within the victims’ names whereas assuring them of suspicious actions and redirecting calls to their facilities.
🔐 Privileged Entry Administration: Study Methods to Conquer Key Challenges
Uncover totally different approaches to beat Privileged Account Administration (PAM) challenges and degree up your privileged entry safety technique.
The implications of such assaults will be vital, leaving victims burdened with substantial loans to repay. Monetary establishments typically underestimate the severity of those invasions and fail to analyze potential fraud.
Though this menace is at present restricted to South Korea, researchers warning that there aren’t any technical obstacles stopping these attackers from increasing to different areas, together with the European Union.
This new type of vishing assault underscores the fixed evolution of felony ways and their capability to take advantage of know-how for malicious functions. The group answerable for the “Letscall” malware demonstrates intricate data of Android safety and voice routing applied sciences.