
Microsoft’s new Azure Lively Listing Cross-Tenant Synchronization (CTS) function, launched in June 2023, has created a brand new potential assault floor which may permit risk actors to extra simply unfold laterally to different Azure tenants.
Microsoft tenants are consumer organizations or sub-organizations in Azure Lively Listing which can be configured with their very own insurance policies, customers, and settings.
Nonetheless, as giant organizations could also be cut up up into a number of tenants for organizational functions, it might generally be simpler to permit customers to synchronize between approved tenants managed by the identical entity.
In June, Microsoft launched a brand new Cross-Tenant Synchronization (CTS) function that permits an administrator to synchronize customers and teams throughout a number of tenants and tenant assets, providing seamless collaboration, automating lifecycle administration of B2B initiatives, and so on.
When configuring CTS, an Azure ‘supply’ tenant will probably be synchronized with a ‘goal’ tenant, the place customers from the supply can robotically be synchronized to the goal tenant. When synchronizing customers, the person is simply pushed from the supply and never pulled from the goal, making this a one-sided synchronization.
Nonetheless, if improperly configured, attackers who’ve already compromised a tenant and gained elevated privileges could exploit the brand new function to maneuver laterally to different linked tenants after which deploy rogue CTS configurations to ascertain persistence on these networks.
This assault floor was beforehand described by Invictus, whose report primarily focuses on detecting risk actors abusing this function.
CTS configuration gaps
In a report revealed yesterday, cybersecurity agency Vectra elaborates on how risk actors can abuse this function to unfold laterally to linked tenants and even use this function for persistence.
Nonetheless, additionally they warn that abusing this function requires a risk actor to first compromise a privileged account or acquire privilege escalation in a breached Microsoft cloud setting.
“We’ve got not noticed using this method within the wild, however given the historic abuse of comparable performance — we current particulars for defenders to grasp how the assault would current and learn how to monitor for its execution,” Vectra clarify in their report.
The primary method described in Vectra’s report includes reviewing the CTS configurations to determine goal tenants linked via these insurance policies and, particularly, search for tenants with ‘Outbound Sync’ enabled, which permits syncing to different tenants.
Upon discovering a tenant that meets these standards, the attacker locates the app used for CTS syncing and modifies its configuration so as to add the compromised person into its sync scope, having access to the opposite tenant’s community. This permits the risk actor to attain lateral motion with out requiring new person credentials.
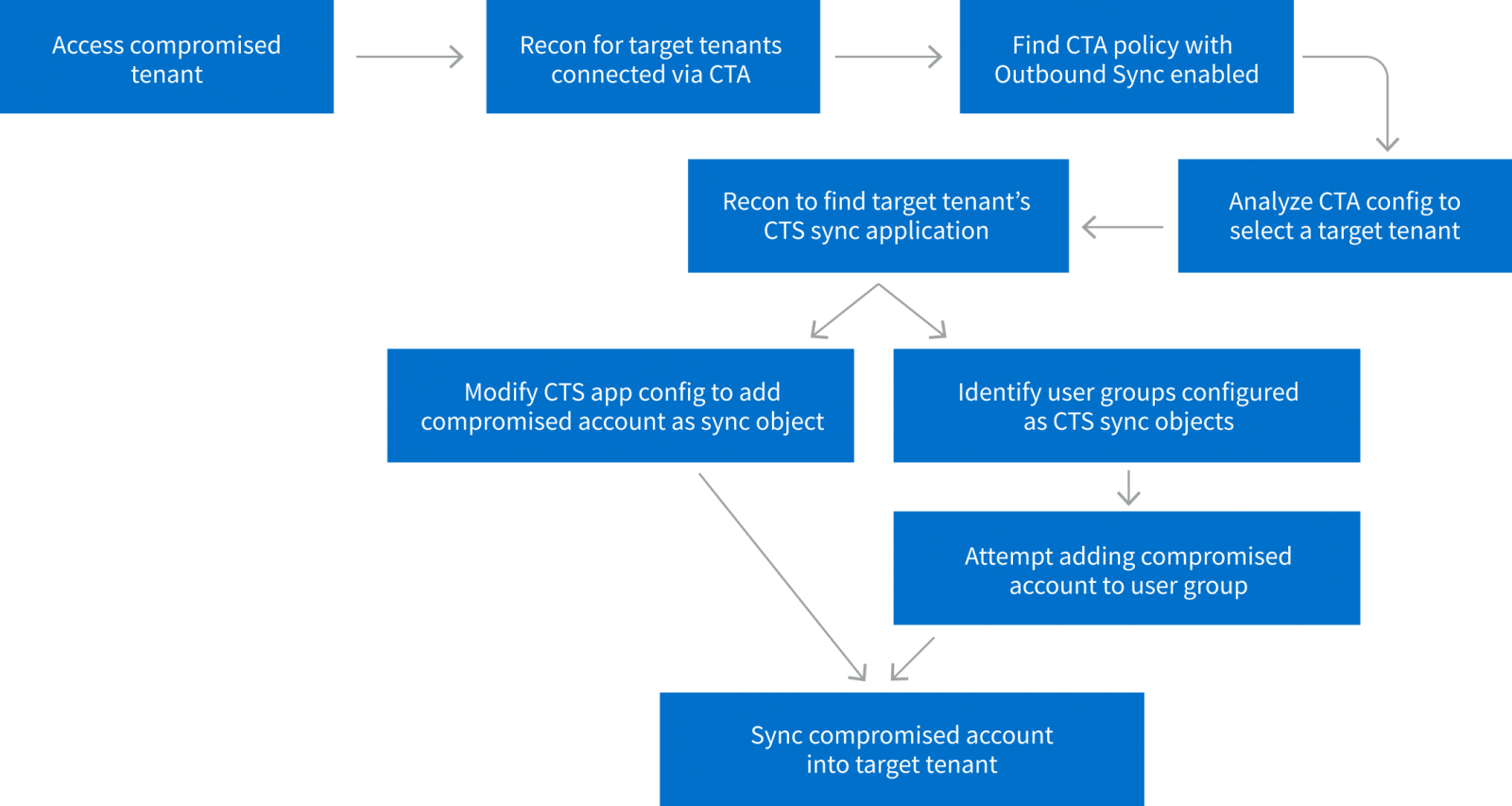
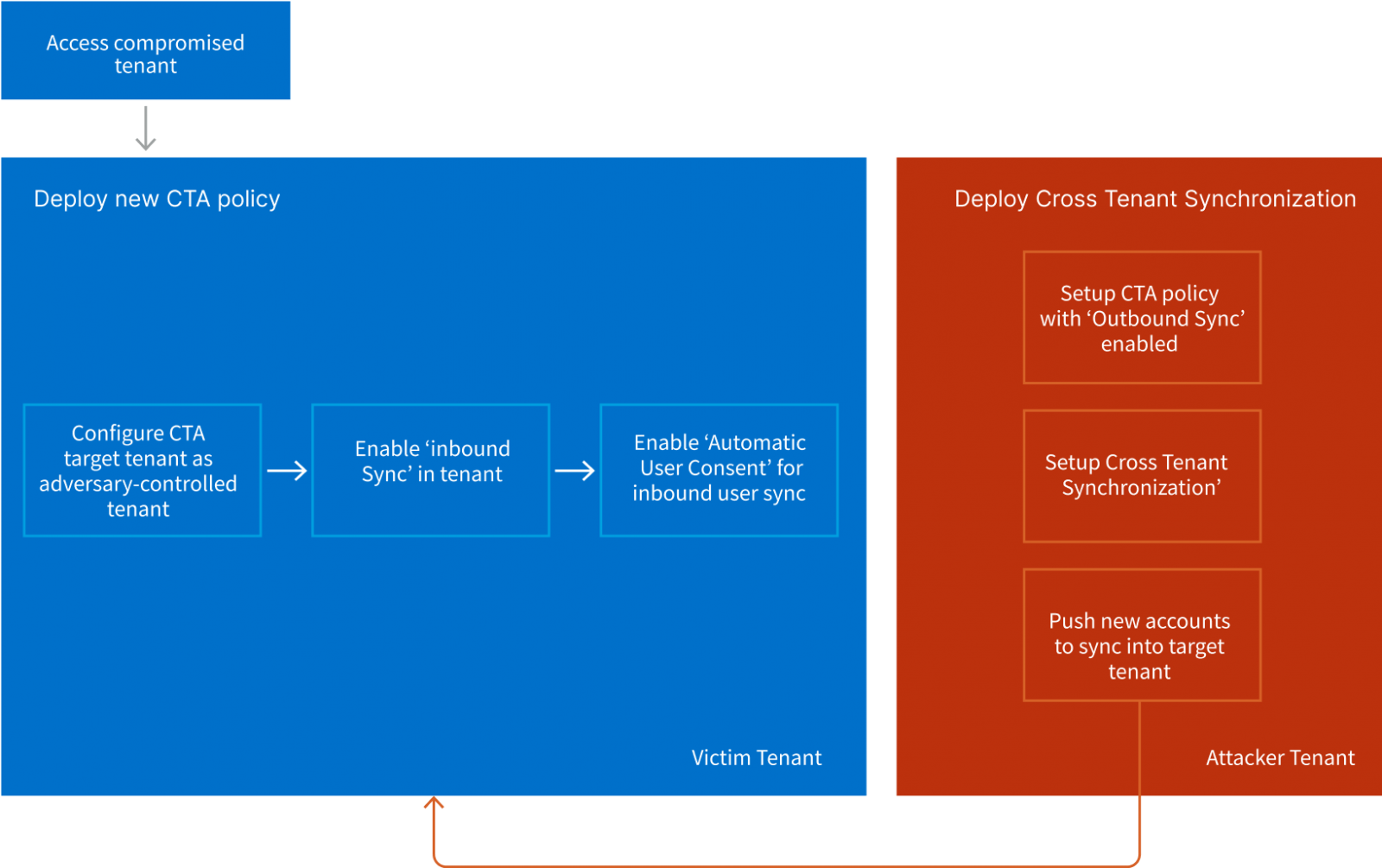
The second method introduced by Vectra includes deploying a rogue CTS configuration to keep up persistent entry to the goal tenants. As soon as once more, it must be famous that this methodology requires a risk actor to already compromise a privileged account within the tenant.
Particularly, the attacker deploys a brand new CTS coverage and permits ‘Inbound Sync’ and ‘Automated Person Consent,’ permitting them to push new customers from their exterior tenant to the goal anytime.
This setup grants the attacker entry to the goal tenant anytime through the exterior account.
Even when the rogue accounts are eliminated, the attacker can create and “push” new customers at will, gaining instant entry to the assets of the goal tenant, therefore why Vectra calls this a “backdoor.”
Defending in opposition to these assaults
Whereas no recognized assaults have abused this function, Vectra has provided steering on hardening your configuration to forestall the function from being abused.
Vectra proposes that CTS goal tenants should keep away from implementing a default or overly inclusive inbound CTA configuration and, if doable, set limits on which customers and teams can entry their cloud environments.
CTS supply tenants that act because the preliminary breach factors should monitor all privileged customers for suspicious exercise.
Invictus’ report supplies detailed info on how CTS exercise is logged, permitting admins to detect malicious conduct.
BleepingComputer contacted Microsoft with questions on the report, however they declined to remark.
