
A brand new ‘Nitrogen’ preliminary entry malware marketing campaign makes use of Google and Bing search adverts to advertise faux software program websites that infect unsuspecting customers with Cobalt Strike and ransomware payloads.
The objective of the Nitrogen malware is to supply the risk actors preliminary entry to company networks, permitting them to conduct data-theft, cyberespionage, and in the end deploying the BlackCat/ALPHV ransomware.
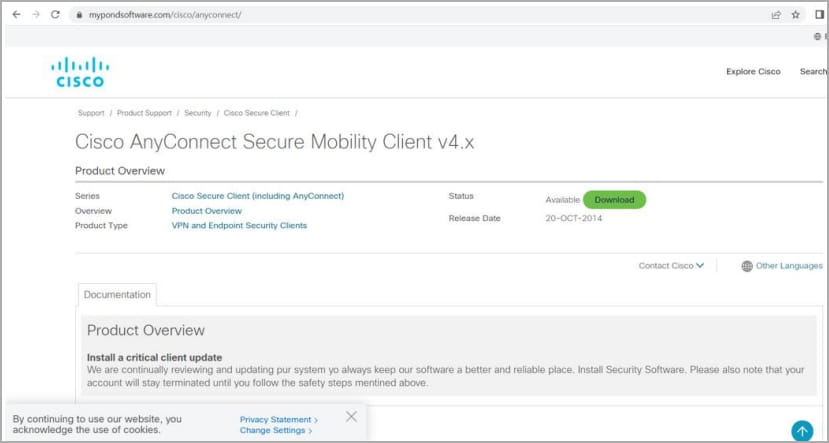
Right this moment, Sophos launched a report on the Nitrogen marketing campaign, detailing the way it primarily targets expertise and non-profit organizations in North America, impersonating in style software program like AnyDesk, Cisco AnyConnect VPN, TreeSize Free, and WinSCP.
Development Micro was the first to doc this exercise at the beginning of the month, seeing WinSCP adverts resulting in BlackCat/ALPHV ransomware infections on a sufferer’s community.
Nevertheless, that report targeted on the post-infection stage and lacked intensive IoCs (Indicators of Compromise) as a result of being based mostly on a single response incident.
The Nitrogen malware marketing campaign
The Nitrogen malware marketing campaign begins with an individual performing a Google or Bing seek for numerous in style software program functions.
The software program seen as lures for the Nitrogen malware marketing campaign consists of:
- AnyDesk (distant desktop software)
- WinSCP (SFTP/FTP consumer for Home windows)
- Cisco AnyConnect (VPN suite)
- TreeSize Free (disk-space calculator and supervisor)
Relying on the focusing on standards, the search engine will show an commercial that promotes the searched-for software program.
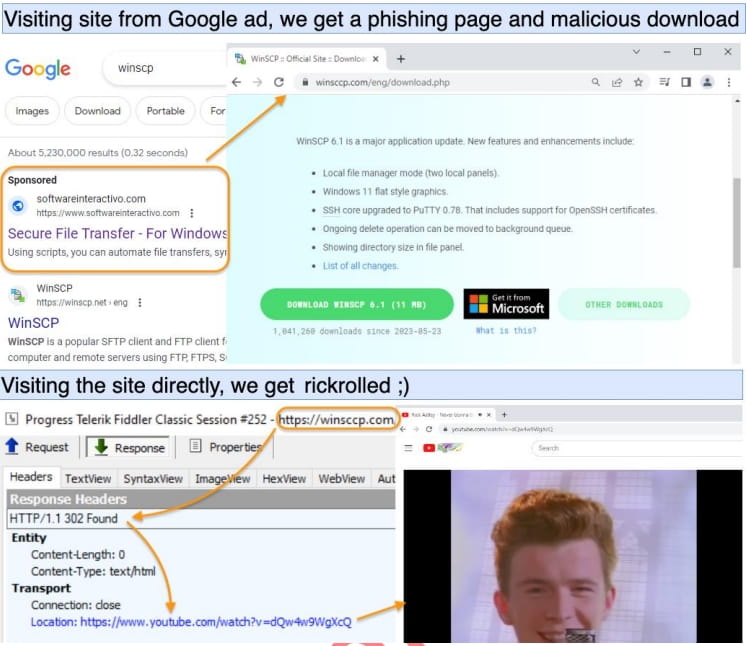
Clicking the hyperlink brings the customer to compromised WordPress internet hosting pages that imitate the respectable software program obtain websites for the actual software.
Solely guests of particular geographic areas are redirected to the phishing websites, whereas direct hits onto the malicious URLs set off a rick-rolling redirection to YouTube movies as an alternative.
Supply: Sophos
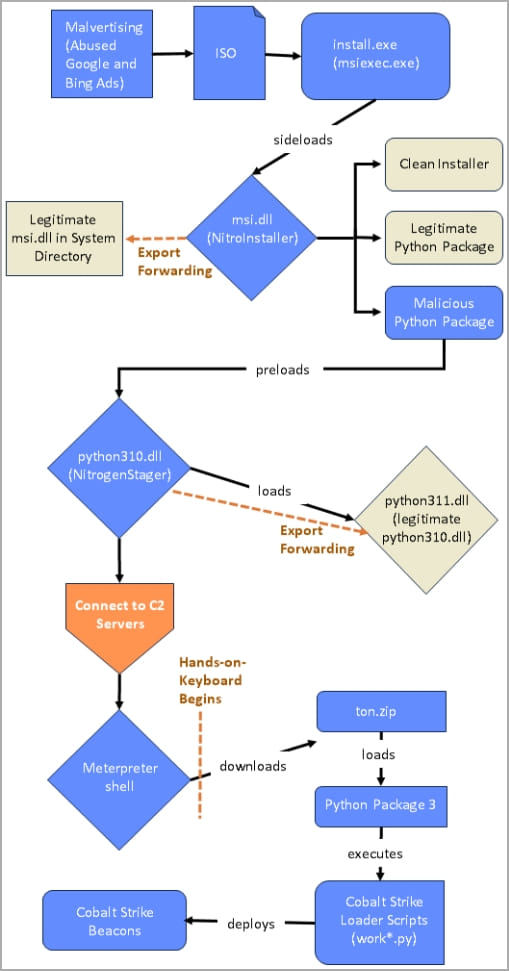
From these faux websites, customers obtain trojanized ISO installers (“set up.exe”), which comprise and sideload a malicious DLL file (“msi.dll”).
The msi.dll is the installer for the Nitrogen preliminary entry malware known as internally “NitrogenInstaller,” which additional installs the promised app to keep away from suspicion and a malicious Python package deal.
Supply: Sophos
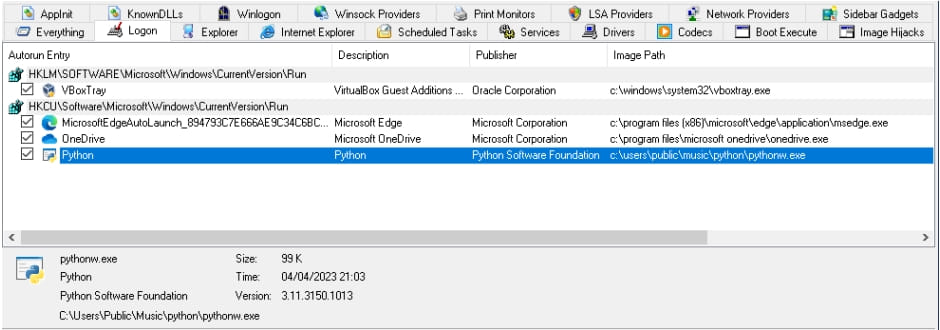
The NitrogenInstaller additionally creates a registry run key named “Python” for persistence, pointing to a malicious binary (“pythonw.exe”) that runs each 5 minutes.
Supply: Sophos
The Python part will execute “NitrogenStager” (“python.311.dll”), which is liable for establishing communication with the risk actor’s C2 and launching a Meterpreter shell and Cobalt Strike Beacons onto the sufferer’s system.
In some circumstances noticed by Sophos analysts, the attackers moved to hands-on exercise as soon as the Meterpreter script was executed on the goal system, executing handbook instructions to retrieve further ZIP information and Python 3 environments.
The latter is required for executing Cobalt Strike in reminiscence, because the NitrogenStager can not run Python scripts.
Supply: Sophos
Sophos says as a result of efficiently detecting and stopping the noticed Nitrogen assaults, it has not decided the risk actor’s objective, however the an infection chain level to staging the compromised techniques for ransomware deployment.
Nevertheless, Development Micro had beforehand reported that this assault chain led to the deployment of the BlackCat ransomware in a minimum of one case.
This marketing campaign will not be the primary time ransomware gangs abused search engine ads to realize preliminary entry to company networks, with each the Royal and Clop ransomware operations utilizing this tactic prior to now.
Customers are really useful to keep away from clicking on “promoted” leads to search engines like google and yahoo when downloading software program and as an alternative solely downloading from the developer’s official website.
Additionally, be cautious of any downloads using ISO information for software program, as that’s an unusual technique to distribute respectable Home windows software program, which normally comes as an .exe or .zip archive.
