Learn the technical particulars a few new AiTM phishing assault mixed with a BEC marketing campaign as revealed by Microsoft, and discover ways to mitigate this risk.

A report from the Microsoft Defender Consultants reveals a brand new multi-staged adversary within the center phishing assault mixed with a enterprise electronic mail compromise assault focusing on banking and monetary establishments. The advanced assault abuses trusted relationships between distributors, suppliers and extra organizations concerned in monetary transactions.
Bounce to:
Stage one: Launching an AiTM phishing assault
AiTM assaults are operations during which a foul actor intercepts and modifies communications between two events, sometimes a person and a respectable authentication service, to steal delicate or monetary data, similar to log-in credentials and bank card knowledge. It may additionally be used to bypass multifactor authentication by stealing customers’ session cookies.
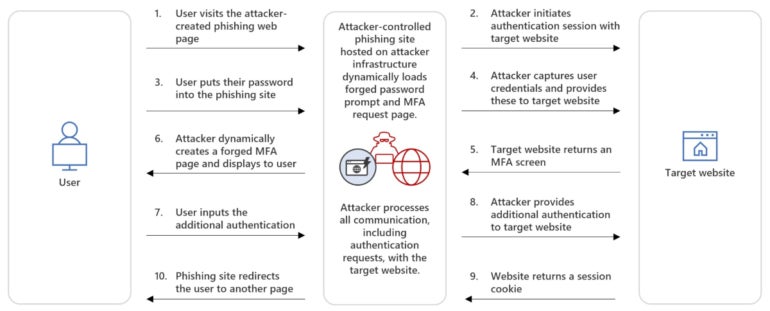
Whereas earlier AiTM assaults usually used reverse proxy strategies to deal with the site visitors between the person and the authentication service, this time the attackers used an oblique proxy methodology. This system is barely totally different because the attacker controls all the things instantly from a phishing web site that mimics the sign-in web page of the focused service. The web site processes all communication, together with authentication requests, with the goal.
The person is enticed to go to the phishing web page, enters their credentials and fills within the extra MFA authentication, which is a pretend MFA request coming instantly from the attackers. Within the background and straight from the phishing server, the attacker initiates communication with the focused service and enters the legitimate customers’ credentials after which the MFA data. The person is being redirected to a different web page at that second, whereas the attacker receives a sound session cookie impersonating the person (Determine A).
Determine A
Within the assault reported by Microsoft and run by a risk actor dubbed Storm-1167, the AiTM hyperlink is shipped to the sufferer by way of electronic mail. The phishing electronic mail impersonates one of many goal’s trusted distributors to look extra respectable and mix with respectable electronic mail site visitors and bypass detections, particularly when a corporation has insurance policies to mechanically enable emails from trusted distributors.
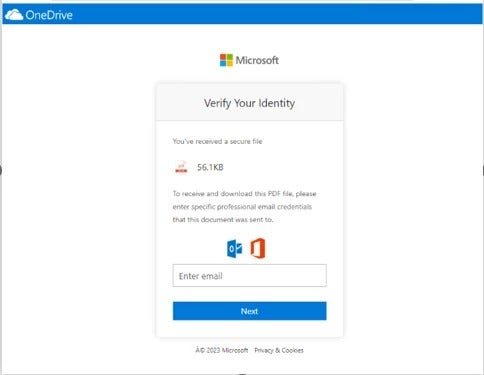
In Microsoft’s instance, the risk actor abused Canva’s respectable graphic design platform to host a web page exhibiting a pretend OneDrive doc resulting in the phishing URL (Determine B).
Determine B
Stage two: Modifying the person’s account
As soon as the attacker was in possession of a sound session cookie, they began accessing electronic mail conversations and paperwork hosted within the cloud and generated a brand new entry token in an effort to use the stolen session for longer.
Then, the Storm-1167 group added a brand new MFA methodology to the stolen person’s account for future use — as soon as once more exhibiting its issues for staying longer within the setting. Since including a brand new MFA methodology doesn’t require re-authentication, the attackers quietly added OneWaySMS, an SMS-based one-time password authentication service.
The ultimate step for the attacker at this stage was to create new inbox guidelines to maneuver all incoming emails on the person’s mailbox to its archive folder and mark all of the emails as learn.
Stage three: BEC marketing campaign begins
Subsequent, the attacker — in full management of the goal’s mailbox — initiated a large phishing marketing campaign of greater than 16,000 emails, specializing in the person’s contacts and distribution lists, all of which had been recognized in earlier electronic mail threads from the person’s mailbox.
After the phishing emails had been despatched, the attacker monitored the mailbox and responded to the recipients, who answered with doubts concerning the phishing electronic mail, to falsely verify that the e-mail was respectable. Undelivered and out-of-office replies had been deleted.
This whole exercise enabled the attacker to gather extra legitimate electronic mail accounts in several organizations and likewise provoke the BEC fraud (Determine C).
Determine C
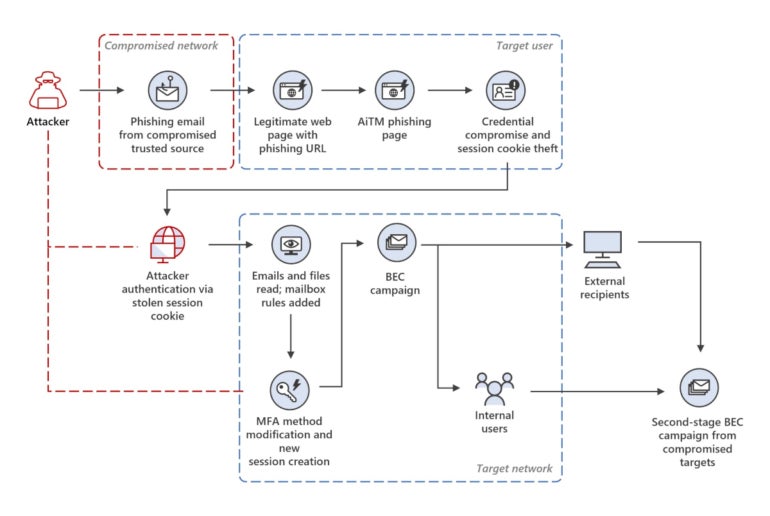
Whereas Microsoft doesn’t go additional in explaining the BEC fraud from the risk actor, it’s anticipated at this level that the actor would impersonate one of many individuals concerned in common cash switch operations to have the sufferer ship the cash to a cybercriminal-owned banking account.
Methods to keep protected from this cybersecurity risk
For the reason that preliminary assault vector is a phishing electronic mail, it’s essential to deploy mailbox safety options that may detect phishing makes an attempt and lift alerts on emails coming from outdoors of the corporate once they observe suspicious behavioral patterns.
E mail field configuration adjustments must also be rigorously monitored. E mail bins immediately beginning to ship a large variety of emails or immediately forwarding lots of emails to a different electronic mail handle ought to increase alerts and be analyzed rigorously.
When potential, electronic mail entry needs to be restricted to trusted IP addresses through company digital non-public networks, for instance; MFA needs to be deployed on these providers. In case such restrictions can’t be deployed, cautious monitoring of each sign-in operation needs to be executed to detect any makes an attempt that present anomalies.
SEE: Finest VPNs for small companies in 2023 (TechRepublic)
Deploying safety options that allow the profiling of customers can be beneficial. Any uncommon attribute of a sign-in operation from a person will increase alerts and may be analyzed with such options.
As for the BEC fraud, any change relating to cash transactions needs to be rigorously investigated. If a trusted associate immediately asks to vary a wire switch vacation spot, the request needs to be investigated with that associate by way of a communication channel aside from electronic mail, and ideally not utilizing computer systems — maybe telephones as an alternative — in case the attacker planted malware on the goal’s laptop and will intercept all communications.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.

