
The Norwegian Nationwide Safety Authority (NSM) has confirmed that attackers used a zero-day vulnerability in Ivanti’s Endpoint Supervisor Cellular (EPMM) answer to breach a software program platform utilized by 12 ministries within the nation.
The Norwegian Safety and Service Group (DSS) mentioned on Monday that the cyberattack didn’t have an effect on Norway’s Prime Minister’s Workplace, the Ministry of Protection, the Ministry of Justice, and the Ministry of Overseas Affairs.
The Norwegian Information Safety Authority (DPA) was additionally notified in regards to the incident, indicating that the hackers may need gained entry to and/or exfiltrated delicate knowledge from compromised techniques, main to an information breach.
“This vulnerability was distinctive, and was found for the very first time right here in Norway. If we had launched the details about the vulnerability too early, it may have contributed to it being misused elsewhere in Norway and in the remainder of the world,” the NSM mentioned.
“The replace is now typically out there and it’s prudent to announce what sort of vulnerability it’s, says Sofie Nystrøm, director of the Nationwide Safety Company.
The Norwegian Nationwide Cyber Safety Middle (NCSC) additionally notified all recognized MobileIron Core clients in Norway in regards to the existence of a safety replace to handle this actively exploited zero-day bug (tracked as CVE-2023-35078).
As a advice, the NCSC urged these system house owners to put in safety updates to dam incoming assaults as quickly as doable.
Actively exploited authentication bypass vulnerability
The CVE-2023-35078 safety bug is an authentication bypass vulnerability that impacts all supported variations of Ivanti’s Endpoint Supervisor Cellular (EPMM) cell machine administration software program (previously MobileIron Core), in addition to unsupported and end-of-life releases.
Profitable exploitation permits distant menace actors to entry particular API paths with out requiring authentication.
“An attacker with entry to those API paths can entry personally identifiable data (PII) reminiscent of names, cellphone numbers, and different cell machine particulars for customers on a susceptible system,” the U.S. Cybersecurity and Infrastructure Safety Company (CISA) warned in an advisory printed on Monday.
“An attacker may also make different configuration adjustments, together with creating an EPMM administrative account that may make additional adjustments to a susceptible system.”
The corporate has confirmed that the zero-day is being exploited in assaults and in addition warned clients that it is important to “instantly take motion to make sure you are totally protected.
In line with Shodan’s Web publicity scanning platform, greater than 2,900 MobileIron consumer portals are presently uncovered on-line, out of which round three dozen are linked with U.S. native and state authorities companies.
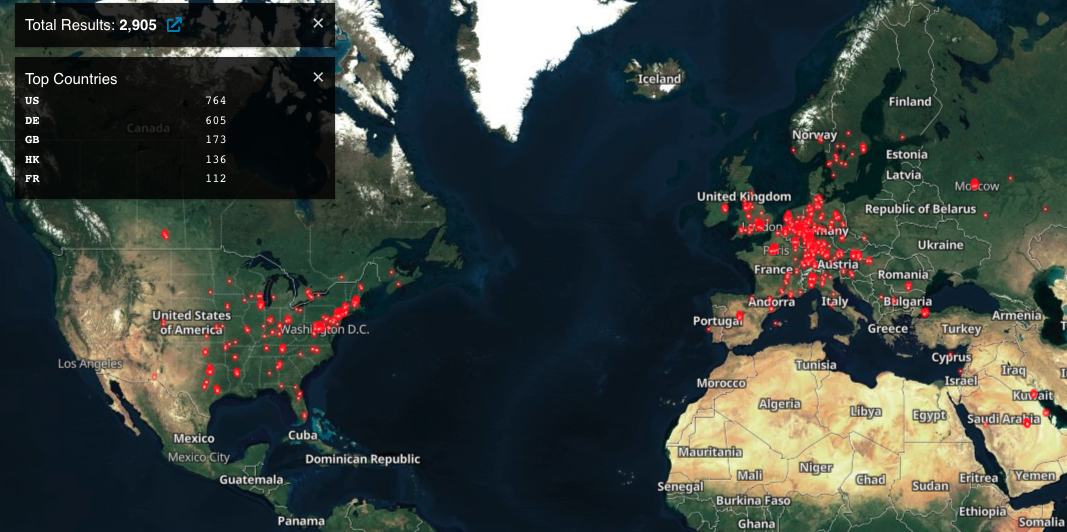
Most of those uncovered servers are in the USA, with different notable areas together with Germany, the UK, and Hong Kong.
In mild of this, it’s essential for all community directors to promptly set up the most recent Ivanti Endpoint Supervisor Cellular (MobileIron) patches to guard their techniques from assaults.
Norway has disclosed different cyberattacks wherein Chinese language and Russian state hackers focused its authorities web sites and the nation’s parliament.
Final yr, in June, the NSM mentioned that Russian hacktivists took down a number of Norwegian authorities web sites in DDoS assaults.
In March 2021, the Chinese language state-sponsored Hafnium hacking group was linked to a different incident wherein they breached the techniques of Norway’s parliament and stole knowledge by exploiting ProxyLogon Microsoft Change vulnerabilities.
In one other assault from August 2020, a number of Norwegian Parliament electronic mail accounts on August have been brute-forced. This incident was linked by Norway’s Minister of Overseas Affairs in December 2020 to the Russian APT 28 state-sponsored hacking group.
