Within the newest model of VMware Cloud Director – 10.5, there’s now help for NSX Federation. This new functionality permits service suppliers to ship a standard community and safety throughout completely different places, every managed by separate, regional NSX Supervisor situations inside a single VMware Cloud Director setting.
Suppliers can register an NSX International Supervisor in VMware Cloud Director (VCD) and make the most of NSX Federation (international) constructs. In VCD, the function is consumed by a brand new sort of Knowledge Heart Group – Common – that may embrace Group Digital Knowledge Facilities (VDCs) from a number of community fault domains or, in different phrases, varied NSX Native Managers.
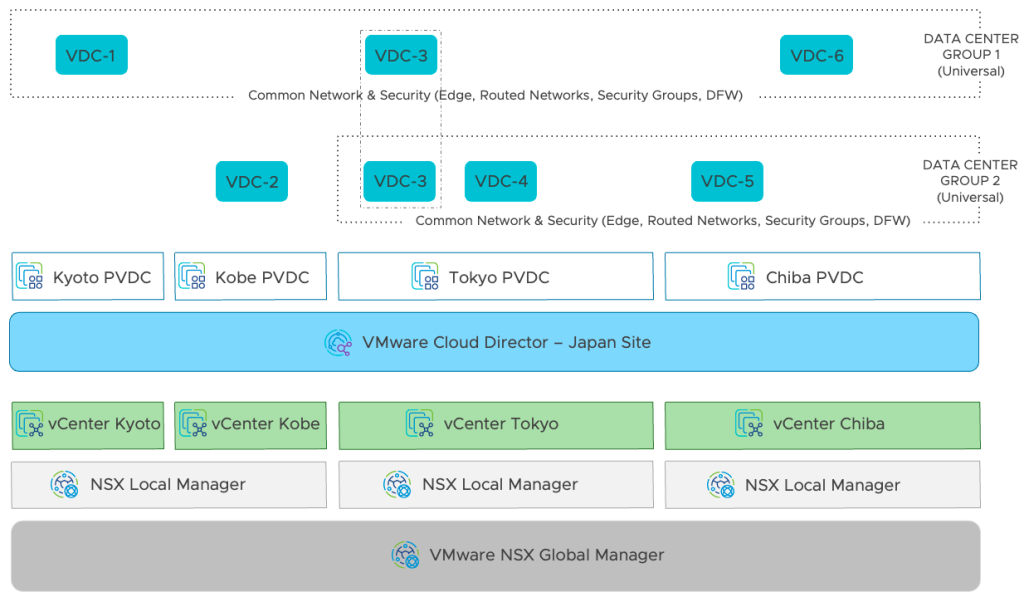
With the power to incorporate as much as 16 VDCs, backed by as much as 4 NSX Supervisor situations in a single Common DC Group, organizations acquire enhanced, scalable and versatile VCD infrastructure. The VCD Supplier Gateway, which might now be backed by an NSX Federation, multi-location, stretched Tier-0 Gateway, defines the boundaries of that Common DC Group.
Solely Have Few Minutes?
Watch this 7-minute demo for a fast preview of how suppliers and tenants can eat and profit from the VMware Cloud Director integration with NSX Federation.
Integration Deep Dive
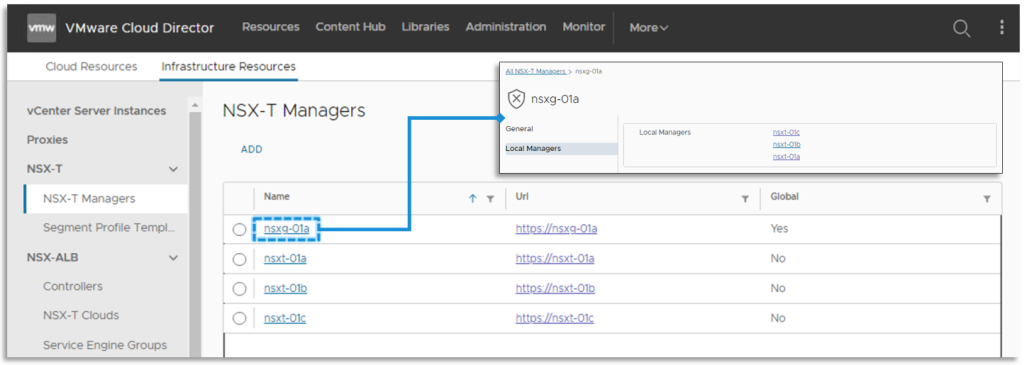
The NSX Federation infrastructure must be arrange upfront with a International NSX Supervisor cluster, and the respective Native NSX Supervisor clusters need to be added to the International as Places. The supplier has to register all Native NSX Managers and their International NSX Supervisor occasion as Infrastructure Sources in VCD. The mixing additionally gives help for international Section Profile Templates configuration.
If the supplier needs to make the most of NSX Federation to ship unified networking and safety throughout places, a International Tier-0 Gateway/s should be created to stretch the completely different places relying on the specified community topology. The stretched Tier-0 Gateways may be deployed in varied fashions:
- Stretched Lively-Lively Tier-0 Gateway with Major and Secondary Places
- Stretched Lively-Lively Tier-0 Gateway with All Major Places
- Stretched Lively-Standby Tier-0 Gateway with Major and Secondary Places

It is very important notice that integrating NSX Federation with VCD doesn’t alter how the supplier digital information facilities (PVDC) are outlined. Every PVDC is backed by its separate Native NSX Supervisor and respective GENEVE community pool.
Supplier Gateway, backed by a International Tier-0
Suppliers have the power to pick a International NSX Supervisor when making a Supplier Gateway. This permits them to decide on a backing International Tier-0 Gateway, which might stretch throughout completely different Places. One fundamental distinction is that IP Areas is the one IP tackle administration technique supported for “International” Supplier Gateways.

The next guidelines apply to “International” Supplier Gateways:
- Any Edge Gateway may be linked to a “International” Supplier Gateway.
- An Edge Gateway created in a Common DC Group context should be linked to a “International” Supplier Gateway.
- The “International” Supplier Gateway VDCs span should be a superset of the Common DC Group VDCs span.
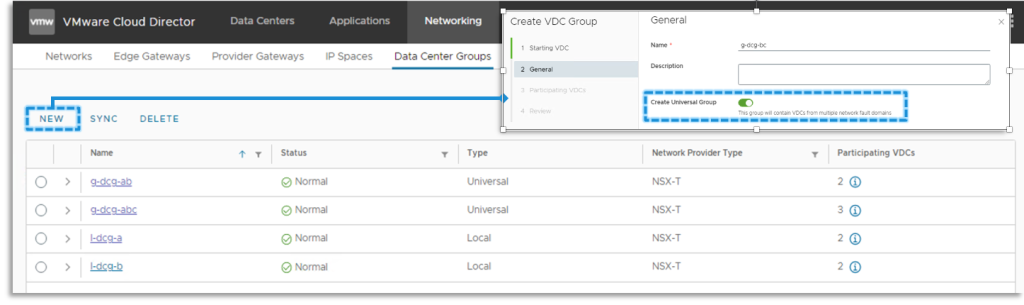
Knowledge Heart Group of sort Common
Historically VCD tenants can eat Knowledge Heart Teams as logical objects containing a set of Group VDCs the place the safety and networking are unified. In different phrases, the PVDCs (backing these Org VDCs) needed to be supported by the identical Community Pool (NSX Transport Zone).
VCD 10.5 introduces the idea of a Common DC Group. The VDCs a part of such a gaggle may be backed by PVDCs from completely different vCenters, Datacenters, and Native NSX Managers within the idea of NSX Federation. The Native NSX Managers outline the scope of the Common DC Group.
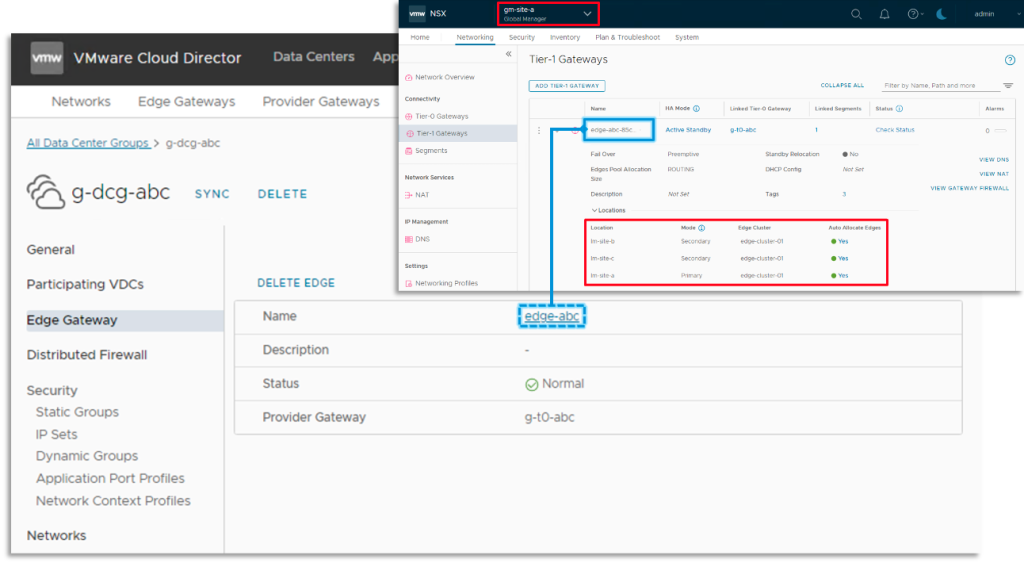
Common DC Group Networking
Tenants can create and handle Edge Gateway and linked routed community parts inside a particular Common DC Group context.
An Edge Gateway outlined inside the Common DC Group context is backed by a International Tier-1 with a Location span matching the VDC to Native NSX Supervisor mapping. Subsequently such Edge should be linked to the suitable “International” Supplier Gateway. This interprets from the NSX Federation structure requirement {that a} International Tier-1 span is the same as or a subset of its upstream International Tier-0 span. In contrast to Native DC Teams, rising/reducing the scope of Common DC Group Edge shouldn’t be supported.
VCD helps solely routed networks within the context of the Common DC Group. The span of the community covers all VDCs within the Common DC Group. This once more interprets from the NSX Federation requirement {that a} International section overlay span all the time equals its connected Tier-1 or Tier-0 span.
VCD helps solely routed networks within the context of the Common DC Group. The span of the community covers all VDCs within the DC Group. This once more interprets from the NSX Federation requirement {that a} International section overlay span all the time equals its connected Tier-1 or Tier-0 span.

Common DC Group Edge Companies
The Edge Gateway default configuration on its backing Tier-1 Gateway Places mode and Edge Cluster placement is predicated on the upstream International Tier-0 Gateway Places mode and Edge Cluster configuration. Nevertheless, if there’s a want to change this default setting, it’s attainable to make the required adjustments from the VCD.
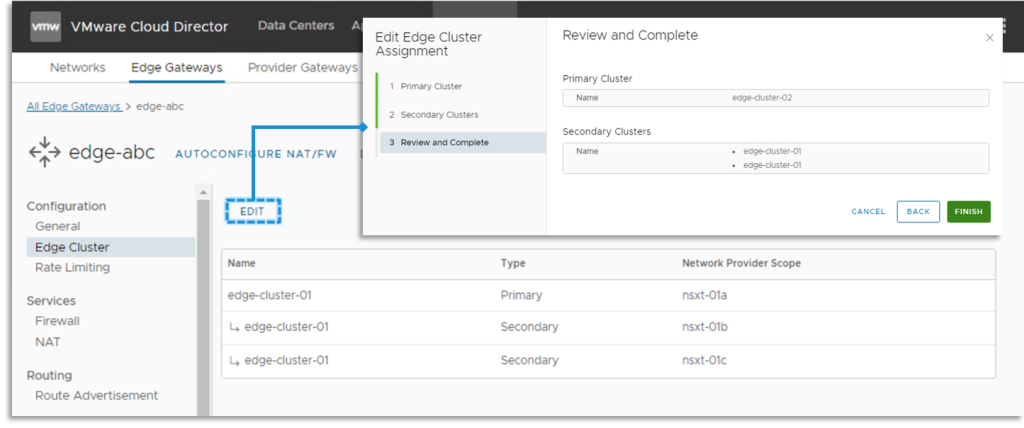
The supported Common DC Group Edge Companies are analogous to the usual Edge, excluding the next important ones:
- VPN Companies (each IPSec and L2VPN)
- BGP and Static Routes
- Load Balancer
The Non-Distributed routing is routinely activated on Common DC Group Edge and can’t be modified.
Connecting Exterior Networks to a Common DC Group Edge is not possible as a result of Service Interface can’t be established on a stretched Tier-1 Gateway. Additionally, the one supported DHCP mode is Relay.
Common DC Group Safety
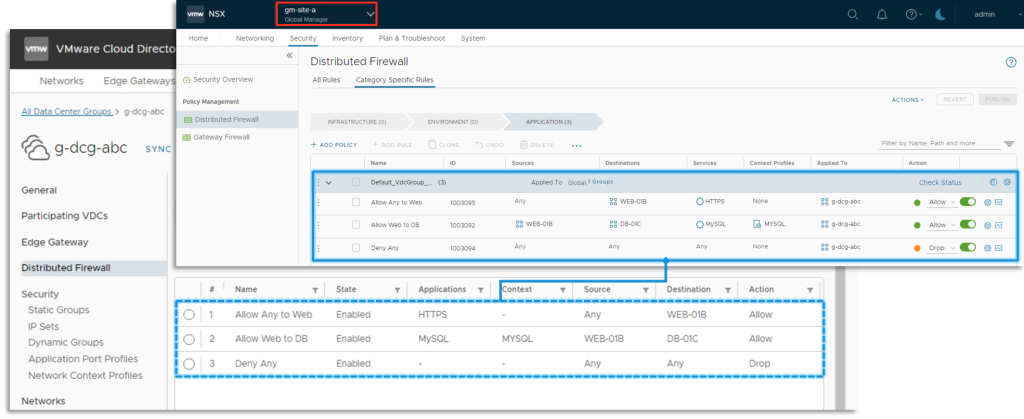
Safety for Common DC Teams may be consumed on each the Edge Gateway and Distributed Firewall (DFW) ranges.
The safety objects, equivalent to IPSet, Static and Dynamic Teams, and Functions Port Profiles, are created as International NSX managed entities and can be utilized in each safety contexts (Edge Gateway and DFW) for the given Common DC Group. All Common DC Teams safety objects are created within the NSX Federation International Area scope.
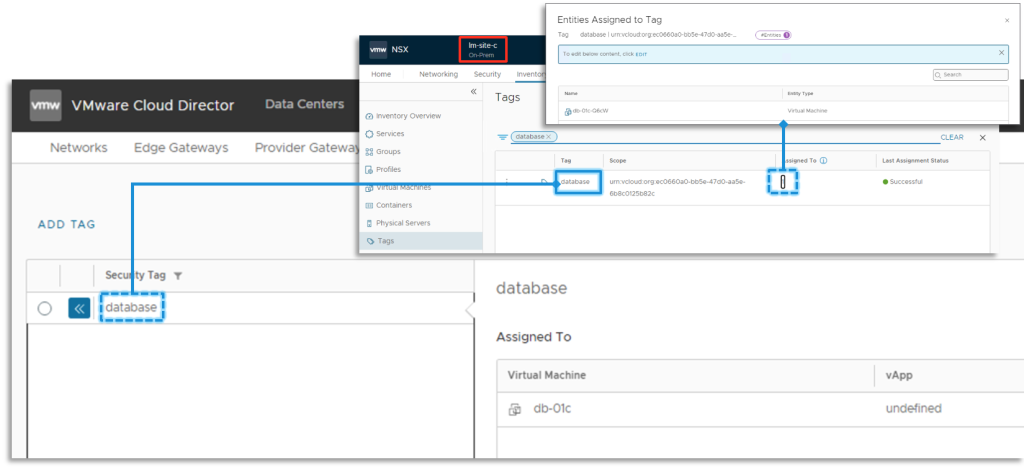
NSX Federation applies the Tags on the Native NSX Supervisor degree. From that perspective, the tags for VMs linked to networks inside a Common DC Group context are dealt with the identical manner as for Native DC Group.
On a Ultimate Observe
Including the help for NSX Federated environments in VMware Cloud Director permits suppliers and tenants to simply scale networking and safety companies throughout a number of networking availability zones. This integration aids catastrophe restoration and enterprise continuity plans by permitting workloads and purposes to be moved and replicated throughout information facilities effortlessly. It additionally streamlines the administration of multi-location environments, thus bettering each suppliers’ and tenants’ operational expertise.
In the event you haven’t already, examine my earlier blogs about VCD 10.5 IP Areas’ new options.
Stay up-to-date by frequently checking this weblog for the newest updates. You can too join with us on Slack, Fb, Twitter, and LinkedIn.
Keep tuned for brand new demo movies and enablement on YouTube, particularly our Characteristic Fridays sequence.

