
Regulation enforcement has detained a suspect believed to be a key member of the OPERA1ER cybercrime group, which has focused cellular banking companies and monetary establishments in malware, phishing, and Enterprise E-mail Compromise (BEC) campaigns.
The gang, also called NX$M$, DESKTOP Group, and Frequent Raven, is suspected of getting stolen between $11 million and $30 million during the last 4 years in additional than 30 assaults spanning 15 international locations throughout Africa, Asia, and Latin America.
The suspect was arrested by authorities in Côte d’Ivoire in early June following a joint regulation enforcement motion dubbed Operation Nervone with the assistance of AFRIPOL, Interpol’s Cybercrime Directorate, cybersecurity firm Group-IB, and telecom service Orange.
Additional info that helped with the investigation was shared by the Felony Investigative Division of america Secret Service and cybersecurity researchers from Booz Allen Hamilton DarkLabs.
“In accordance with the INTERPOL’s 2022 African Cyberthreat Evaluation Report, cybercrime is a rising risk within the West Africa area, with victims situated worldwide. Operation NERVONE underscores INTERPOL’s dedication to proactively fight the specter of cybercrime within the area,” Interpol stated immediately.
“Operation Nervone was backed by two key INTERPOL initiatives: the African Joint Operation towards Cybercrime and the INTERPOL Help Programme for the African Union in relation to AFRIPOL, funded by the UK’s Overseas, Commonwealth & Improvement Workplace and Germany’s Federal Overseas Workplace, respectively.”
Group-IB analysts and the CERT-CC division at Orange, monitoring the OPERA1ER group since 2019, have linked the risk actors to over 35 profitable assaults between 2018 and 2022, roughly one-third of them carried out in 2020.
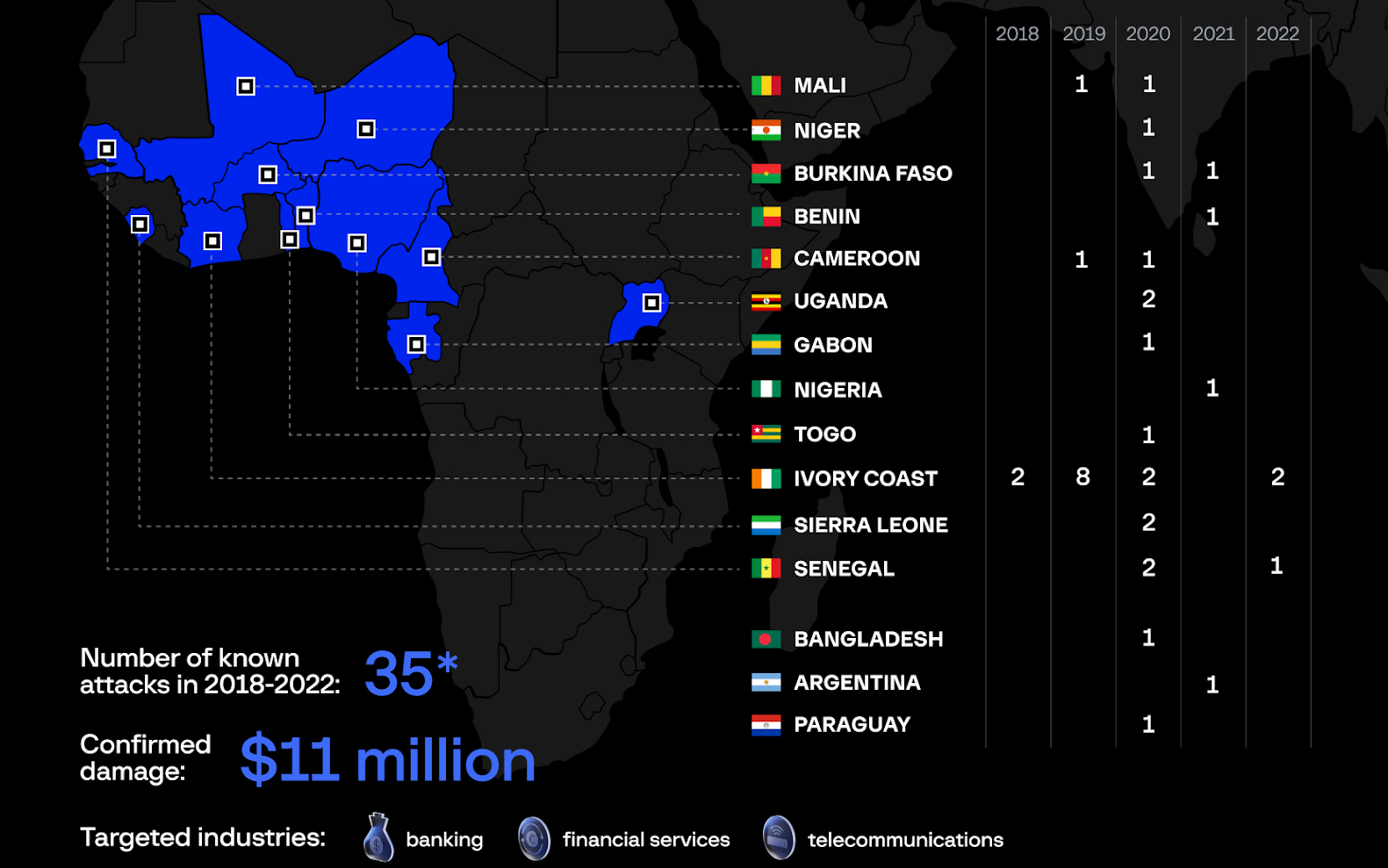
OPERA1ER members predominantly converse French and are believed to function from Africa, and so they depend on varied instruments of their assaults, together with open-source options, frequent malware, and frameworks like Metasploit and Cobalt Strike.
Nevertheless, preliminary entry to targets’ networks is gained by means of spear-phishing emails that exploit widespread topics similar to invoices or postal supply notifications and push a variety of first-stage malware, together with Netwire, BitRAT, venomRAT, AgentTesla, Remcos, Neutrino, BlackNET, and Venom RAT, in addition to password sniffers and dumpers.
OPERA1ER has been noticed sustaining entry to compromised networks for a interval starting from three to 12 months, often concentrating on the identical firm a number of instances.
Additionally they sometimes concentrate on operator accounts that management important sums of cash, utilizing stolen credentials to switch funds into Channel Consumer accounts earlier than in the end redirecting them to subscriber accounts underneath their management. The group withdraws the stolen cash as money by means of an intensive community of ATMs over holidays or weekends to keep away from detection.
Researchers at Symantec additionally discovered hyperlinks between OPERA1ER and a cybercriminals group they monitor as Bluebottle that used a signed Home windows driver in assaults towards not less than three banks in French-speaking African international locations.
“Any try to research a classy risk actor similar to OPERA1ER, which stole hundreds of thousands from monetary service firms and telecom suppliers internationally, requires a extremely coordinated effort between private and non-private sector our bodies,” stated Group-IB CEO Dmitry Volkov.
“The success of Operation Nervone exemplifies the significance of risk information alternate, and due to our collaboration with INTERPOL, Orange-CERT-CC and personal and public sector companions, we have been collectively in a position to piece collectively the entire puzzle.”
