
Getty Photographs
For 3 days, system directors have been troubleshooting errors which have prevented Home windows customers from working functions equivalent to QuickBooks and Avatax. We now know the trigger: an unannounced transfer or glitch by Microsoft that eliminated a once-widely used digital certificates in Home windows.
The eliminated credential is called a root certificates, that means it anchors the belief of tons of or 1000’s of intermediate and particular person certificates downstream. The foundation certificates—with the serial quantity 18dad19e267de8bb4a2158cdcc6b3b4a and the SHA1 fingerprint 4EB6D578499B1CCF5F581EAD56BE3D9B6744A5E5—was not trusted in Home windows. As a result of that root was tied to certificates that certify their authenticity and belief, folks making an attempt to make use of or set up the app acquired the error.
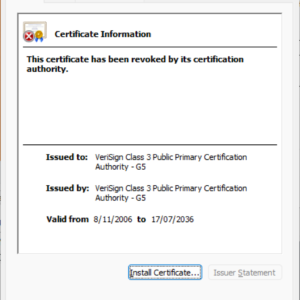
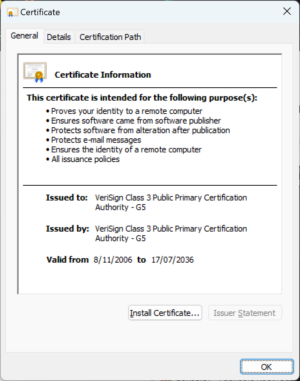
Simply minutes earlier than this submit was scheduled to go stay, researchers discovered that the certificates had been restored in Home windows. It’s unclear how or why that occurred. The certificates instantly beneath this paragraph exhibits the certificates’s standing on Thursday. The one beneath that exhibits the standing as of Friday.
That point Symantec certs had been banished from the Web
Microsoft has but to reply to a request to elucidate the errors. It might be {that a} glitch induced Home windows to take away the basis certificates. It’s additionally potential the removing was intentional, on condition that it’s certainly one of a number of that confronted an industry-wide blockade following the invention in 2015 that its mother or father issuer on the time, Symantec, had improperly issued certificates for google.com, www.google.com, and one different area. (Symantec bought its certificates authority (CA) companies to DigiCert in 2017.)
After Google researchers asserted a couple of weeks later that the variety of mis-issued certificates was a lot larger, Symantec revised the quantity to 164 certificates for 76 domains and a pair of,458 certificates for domains that had by no means been registered. In gentle of the brand new info, Google gave Symantec an ultimatim: give a radical accounting of its ailing certificates authority course of or danger having the world’s hottest browser—Chrome—challenge scary warnings about Symantec certificates each time finish customers visited HTTPS-protected web sites that used them.
Some 17 months later, Google made good on the risk after its investigation concluded that for years, Symantec-owned CAs had improperly issued greater than 30,000 certificates. The corporate started preparations to progressively nullify Chrome’s belief in all certificates issued by these CAs, which had been bought below manufacturers together with Verisign, Thawte, and GeoTrust. Efficient instantly at the moment, Chrome stopped recognizing any prolonged validation standing of such certificates, and as time went on, the browser revoked an increasing number of of its belief.
Mis-issued certificates signify a essential risk to nearly your entire Web inhabitants; they make it potential for the holders to cryptographically impersonate the affected websites and monitor or tamper with communications despatched between guests and the official servers. Specifically, certificates for non-existent domains or domains belonging to events aside from the holder are main violations of the so-called baseline necessities that main browser makers impose on CAs as a situation of being trusted by their software program.
Symantec’s transgressions had been severe. However given Symantec’s standing on the time as one of many largest issuers of certificates, Google and different stakeholders had been in a bind. If Google or different browser makers had been to nullify the entire Symantec-issued certificates in a single day, it could trigger widespread outages. The chaos that will consequence made the issuer too large to fail. The penalties outlined by Google aimed to attenuate such disruptions whereas exacting a significant punishment.
Over the following two years, browser makers and different firms that depend on digital certificates to safe Web communications progressively phased out belief within the certificates. Most timetables referred to as for a deadline someday in 2019. For causes Microsoft has but to elucidate, Home windows continued to belief the basis certificates to signal software program.
That belief was lastly revoked—or no less than suspended—on Tuesday, as soon as once more with no rationalization or discover. The transfer despatched sys admins scrambling to find out why customers had been receiving certificates errors when making an attempt to run software program equivalent to QuickBooks and AvaTax. Ultimately, the CEO of safety agency Airlock Digital traced the trigger to the unannounced change in Home windows.
A Microsoft consultant supplied to supply remark for this story on the situation the data not be attributed to Microsoft in any manner. Ars declined.
It’s probably that Microsoft delayed the revocation of the certificates for app-signing functions as a result of certificates in apps can’t be up to date as simply as they’ll for web sites. With no steering from the corporate, folks troubleshooting error messages are on their very own.
One possibility for resolving issues is to replace affected apps. By now, most apps have probably been up to date to make use of certificates not associated to those which were blocked. By default, Home windows has a function often called automated root updates turned on. Some customers have it turned off for numerous causes, a lot of them official. The above-linked Reddit thread additionally supplies a number of scripts folks can run to rotate out the basis certificates.

