Safety researchers have warned about an “simply exploitable” flaw within the Microsoft Visible Studio installer that may very well be abused by a malicious actor to impersonate a official writer and distribute malicious extensions.
“A menace actor might impersonate a well-liked writer and problem a malicious extension to compromise a focused system,” Varonis researcher Dolev Taler mentioned. “Malicious extensions have been used to steal delicate data, silently entry and alter code, or take full management of a system.”
The vulnerability, which is tracked as CVE-2023-28299 (CVSS rating: 5.5), was addressed by Microsoft as a part of its Patch Tuesday updates for April 2023, describing it as a spoofing flaw.
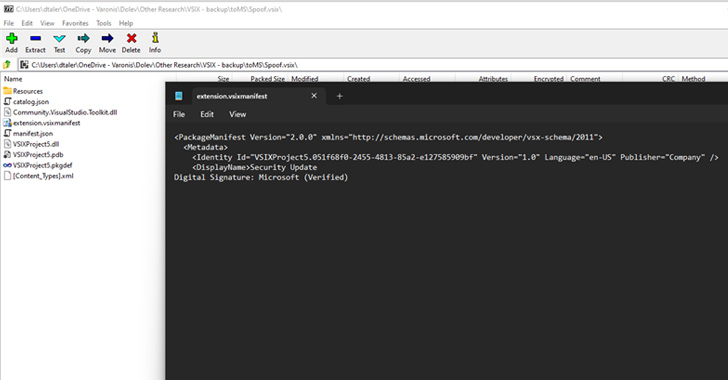
The bug found by Varonis has to do with the Visible Studio consumer interface, which permits for spoofed writer digital signatures.
Particularly, it trivially bypasses a restriction that forestalls customers from getting into data within the “product title” extension property by opening a Visible Studio Extension (VSIX) bundle as a .ZIP file after which manually including newline characters to the “DisplayName” tag within the “extension.vsixmanifest” file.
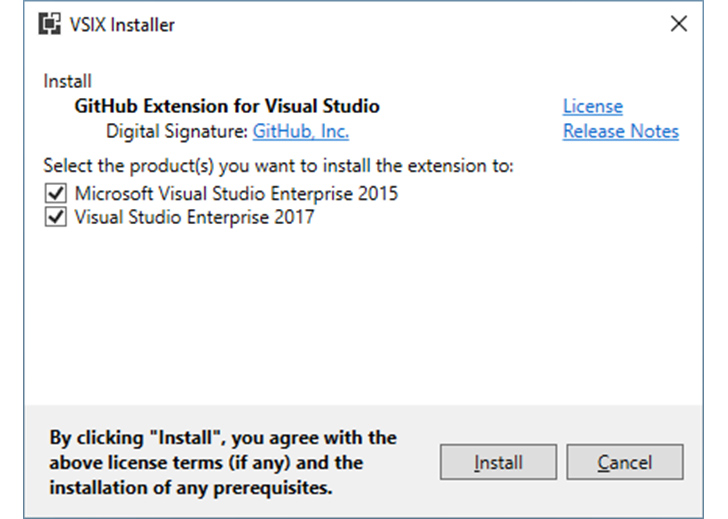
By introducing sufficient newline characters within the vsixmanifest file and including faux “Digital Signature” textual content, it was discovered that warnings in regards to the extension not being digitally signed may very well be simply suppressed, thereby tricking a developer into putting in it.
🔐 Mastering API Safety: Understanding Your True Assault Floor
Uncover the untapped vulnerabilities in your API ecosystem and take proactive steps in direction of ironclad safety. Be a part of our insightful webinar!
In a hypothetical assault situation, a nasty actor might ship a phishing electronic mail bearing the spoofed VSIX extension by camouflaging it as a official software program replace and, post-installation, acquire a foothold into the focused machine.
The unauthorized entry might then be used as a launchpad to realize deeper management of the community and facilitate the theft of delicate data.
“The low complexity and privileges required make this exploit simple to weaponize,” Taler mentioned. “Menace actors might use this vulnerability to problem spoofed malicious extensions with the intention of compromising programs.”