Cloud environments proceed to be on the receiving finish of an ongoing superior assault marketing campaign dubbed SCARLETEEL, with the risk actors now setting their sights on Amazon Internet Providers (AWS) Fargate.
“Cloud environments are nonetheless their main goal, however the instruments and strategies used have tailored to bypass new safety measures, together with a extra resilient and stealthy command and management structure,” Sysdig safety researcher Alessandro Brucato mentioned in a brand new report shared with The Hacker Information.
SCARLETEEL was first uncovered by the cybersecurity firm in February 2023, detailing a classy assault chain that culminated within the theft of proprietary knowledge from AWS infrastructure and the deployment of cryptocurrency miners to revenue off the compromised techniques’ sources illegally.
A follow-up evaluation by Cado Safety uncovered potential hyperlinks to a prolific cryptojacking group often known as TeamTNT, though Sysdig instructed The Hacker Information that it “could possibly be somebody copying their methodology and assault patterns.”
The most recent exercise continues the risk actor’s penchant for going after AWS accounts by exploiting weak public-facing net purposes with an final intention to achieve persistence, steal mental property, and probably generate income to the tune of $4,000 per day utilizing crypto miners.
“The actor found and exploited a mistake in an AWS coverage which allowed them to escalate privileges to AdministratorAccess and acquire management over the account, enabling them to then do with it what they needed,” Brucato defined.
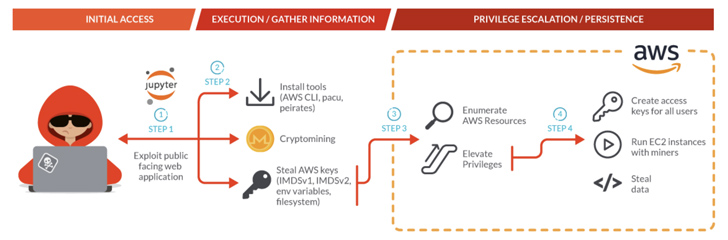
All of it begins with the adversary exploiting JupyterLab pocket book containers deployed in a Kubernetes cluster, leveraging the preliminary foothold to conduct reconnaissance of the goal community and collect AWS credentials to acquire deeper entry into the sufferer’s setting.
That is adopted by the set up of the AWS command line device and an exploitation framework referred to as Pacu for subsequent exploitation. The assault additionally stands out for its use of assorted shell scripts to retrieve AWS credentials, a few of which goal AWS Fargate compute engine cases.
“The attacker was noticed utilizing the AWS shopper to hook up with Russian techniques that are suitable with the S3 protocol,” Brucato mentioned, including the SCARLETEEL actors used stealthy strategies to make sure that knowledge exfiltration occasions should not captured in CloudTrail logs.
🔐 PAM Safety – Knowledgeable Options to Safe Your Delicate Accounts
This expert-led webinar will equip you with the information and techniques it’s worthwhile to remodel your privileged entry safety technique.
A number of the different steps taken by the attacker embrace the usage of a Kubernetes Penetration Testing device often known as Peirates to take advantage of the container orchestration system and a DDoS botnet malware referred to as Pandora, indicating additional makes an attempt on the a part of the actor to monetize the host.
“The SCARLETEEL actors proceed to function in opposition to targets within the cloud, together with AWS and Kubernetes,” Brucato mentioned. “Their most popular methodology of entry is exploitation of open compute companies and weak purposes. There’s a continued deal with financial acquire through crypto mining, however […] mental property continues to be a precedence.”