Increasingly more individuals these days desire to purchase items on-line. And why not? It’s handy, items can be delivered to the doorstep, and if you happen to select one in every of many on-line marketplaces, it’s even potential to avoid wasting cash. Sadly, scammers abuse this, focusing on these companies and their clients for the scammer’s profit. They will create an inventory for items they don’t personal or don’t intend to promote. As soon as the sufferer pays, they seemingly disappear into the ether.
Lately we discovered the supply code of a toolkit that helps scammers a lot of their endeavors that they don’t must be significantly well-versed in IT, however solely want a silver tongue to steer their victims. This toolkit is carried out as a Telegram bot that, when activated, gives a number of easy-to-navigate menus within the type of clickable buttons that may accommodate many scammers without delay. On this blogpost we’ll give attention to toolkit evaluation and options, and on the construction of the group(s) that use itWe’ve named this toolkit Telekopye.
This weblog submit is the primary of a two-part collection the place we take a better have a look at Telekopye and present among the key options which are very useful to scammers. Within the second half, we’ll focus extra on group operations.
Key factors of this blogpost
- Telekopye is a toolkit that operates as a Telegram bot and helps scammers rip-off their victims.
- Telekopye is designed to focus on on-line marketplaces; primarily (however not solely) these well-liked in Russia.
- Telekopye creates phishing net pages from predefined templates, and generates and sends phishing emails and SMS messages.
- Customers and operators of Telekopye are organized in a transparent hierarchy.
Overview
We devised the identify Telekopye as a portmanteau of Telegram and kopye (копье), the Russian phrase for spear, resulting from the usage of extremely focused (aka spear-) phishing. Victims of this rip-off operation are referred to as Mammoths by the scammers (see Determine 1) and several other leads level to Russia because the nation of origin of the toolkit’s authors and customers. For the sake of readability, and following the identical logic, we’ll discuss with the scammers utilizing Telekopye as Neanderthals.

Determine 1. One of many memes (Mammoth misplaced) from a gaggle dialog posted by Neanderthals
Telekopye was uploaded to VirusTotal a number of instances, primarily from Russia, Ukraine, and Uzbekistan, from the place Neanderthals often function based mostly on the language utilized in feedback within the code (we’ve got added machine translations to English in brackets in numerous pictures on this blogpost) and the vast majority of focused markets. Regardless that the principle targets of Neanderthals are on-line markets well-liked in Russia, like OLX and YULA, we noticed that their targets are additionally on-line markets that aren’t native to Russia, like BlaBlaCar or eBay, and even others that don’t have anything in frequent with Russia, like JOFOGAS and Sbazar. Simply as an instance how huge a few of these marketplaces are, the OLX platform had, in keeping with Fortune, 11 billion web page views and eight.5 million transactions monthly in 2014.
We have been capable of acquire a number of variations of Telekopye, suggesting steady improvement. All of those variations are used to create phishing net pages, and ship phishing e mail and SMS messages. As well as, some variations of Telekopye can retailer sufferer knowledge (often card particulars or e mail addresses) on disk the place the bot is run. Telekopye may be very versatile however doesn’t include any chatbot AI performance. Therefore, it doesn’t really carry out the scams; it solely eases the era of content material utilized in such scams. In July 2023, we detected new domains that match the modus operandi of Telekopye operators, so they’re nonetheless lively. The newest model of Telekopye we’ve got been capable of collect was from April eleventh, 2022. We assess that Telekopye has been in use since at the very least 2015 and, based mostly on snippets of dialog between Neanderthals, that completely different scammer teams are utilizing it.
Telekopye rip-off situation
Due to human nature, scamming in on-line marketplaces appears to be very simple. It often comes all the way down to a number of key elements of the rip-off, as seen in Determine 2, that Neanderthals comply with. First, Neanderthals discover their victims (Mammoths). Then they attempt to earn their belief and persuade them that they’re legit (why that is wanted we’ll focus on partially 2). When Neanderthals assume {that a} Mammoth sufficiently trusts them, they use Telekopye to create a phishing net web page from a premade template and ship the URL to the Mammoth (the URL may also be despatched by way of SMS or e mail). After the mammoth submits card particulars by way of this web page, the Neanderthals use these card particulars to steal cash from the Mammoth’s credit score/debit card, whereas hiding the cash utilizing a number of completely different methods akin to laundering it via cryptocurrency. Primarily based on a number of dialog snippets, we assess that some crypto mixers are concerned. There’s a lacking hyperlink between when cash is scammed from the Mammoth and the payout to the Neanderthals, which is often in cryptocurrency.
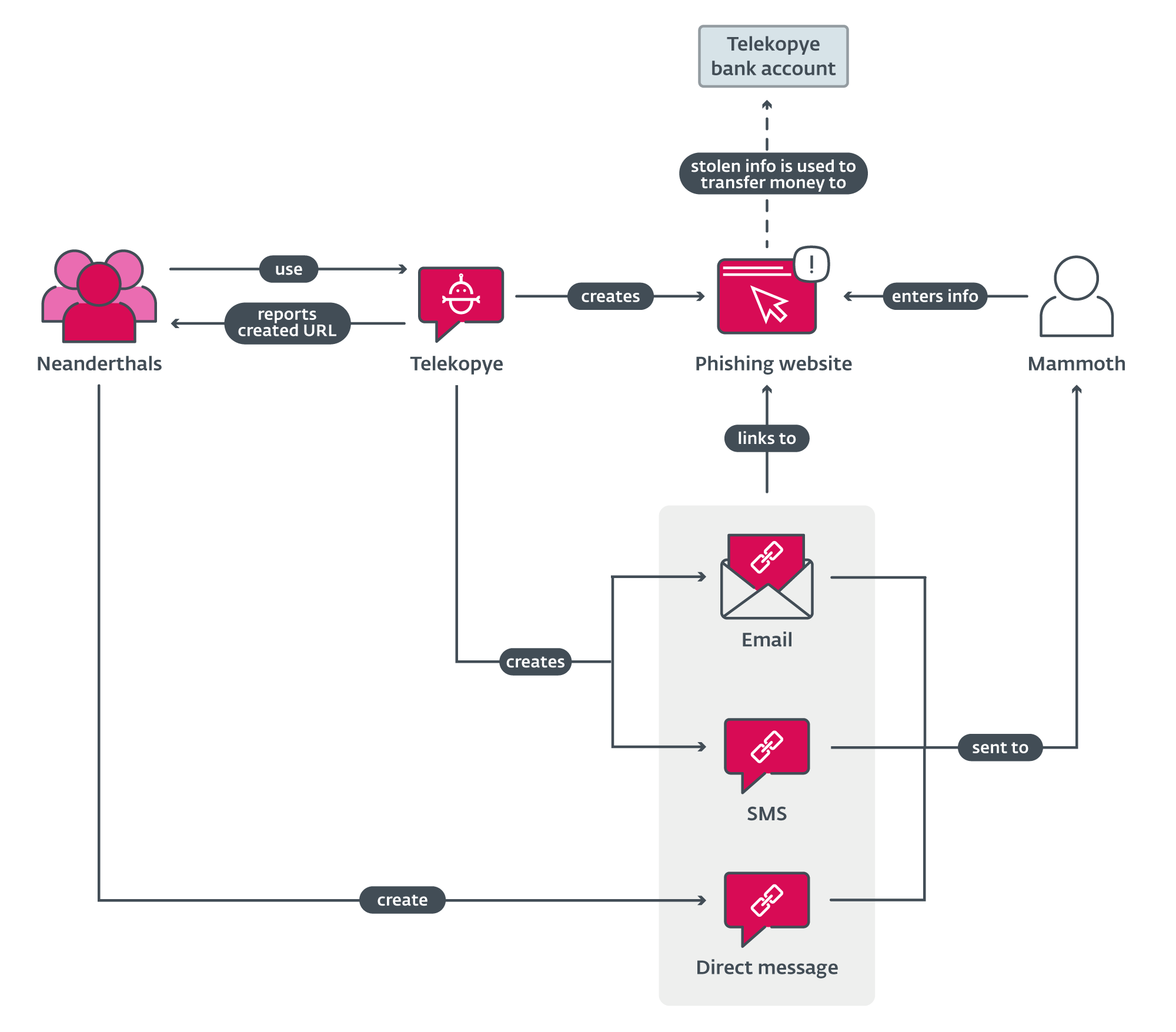
Telekopye performance
Telekopye has a number of completely different functionalities that Neanderthals can use to their full extent. These functionalities embrace sending phishing emails, producing phishing net pages, sending SMS messages, creating QR codes, and creating phishing screenshots. Within the following sections, we’ll give attention to essentially the most helpful elements of Telekopye for the typical Neanderthal.
Interface
Each Telegram group utilizing Telekopye consists of a number of Neanderthals that function concurrently and independently. Performance is obtainable via buttons, more likely to make scamming simpler for Neanderthals.
Determine 3 exhibits one of many menus of Telekopye in a working Telegram group. Significantly noteworthy are the buttons “My adverts”, exhibiting all opened listings (ongoing rip-off commercials) every Neanderthal has, and “My profile”, permitting Neanderthals to see their profile info on this platform, such because the variety of scams pulled off, sum of money prepared for subsequent payout, and many others.
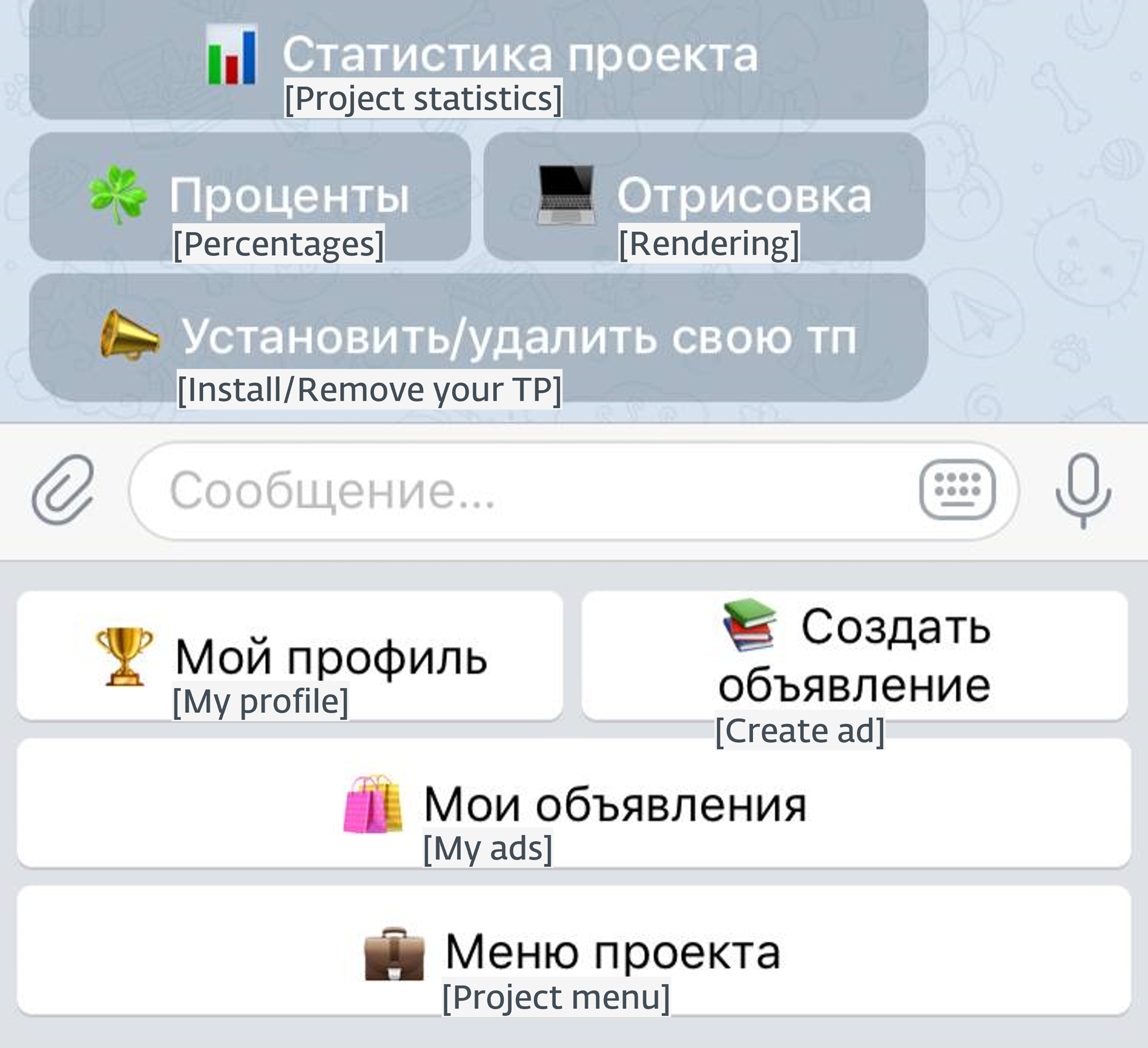
Determine 3. Instance of Telekopye operator interface in a Telegram group
Phishing web page era
The core function of Telekopye is that it creates phishing net pages from predefined HTML templates on demand. A Neanderthal must specify the sum of money, product identify and, based mostly on the template, extra info like location to which the product can be despatched, image, weight, and purchaser’s identify. Then Telekopye takes all this info and creates a phishing net web page. These phishing net pages are designed to imitate completely different cost/financial institution login websites, credit score/debit card cost gateways, or just cost pages of various web sites.
To make the phishing web site creation course of simpler, these web site templates are organized by nations they aim. Determine 4 exhibits a easy creation menu the place some templates are sorted in keeping with completely different nations. The one outlier is BlaBlaCar for country-independent car-sharing companies.
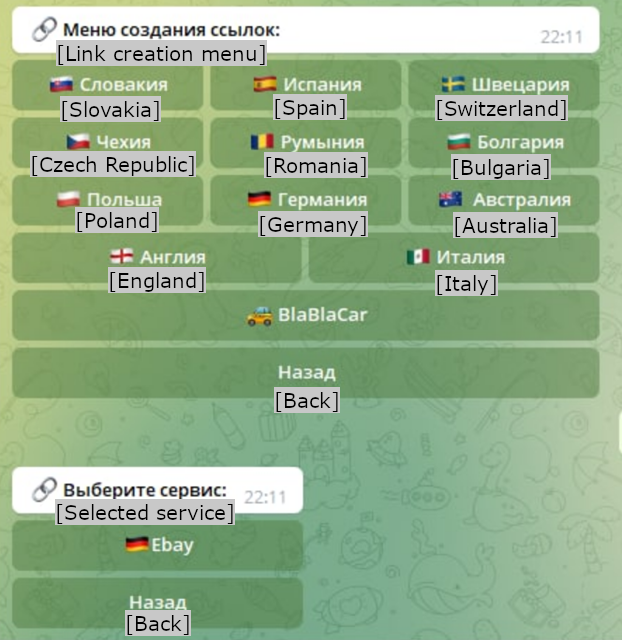
Determine 4. Creation menu for various phishing pages. Discover the Swedish flag is incorrectly related to Switzerland within the high, proper nook.
Determine 5 exhibits one such phishing net web page, probably not totally perfected but.
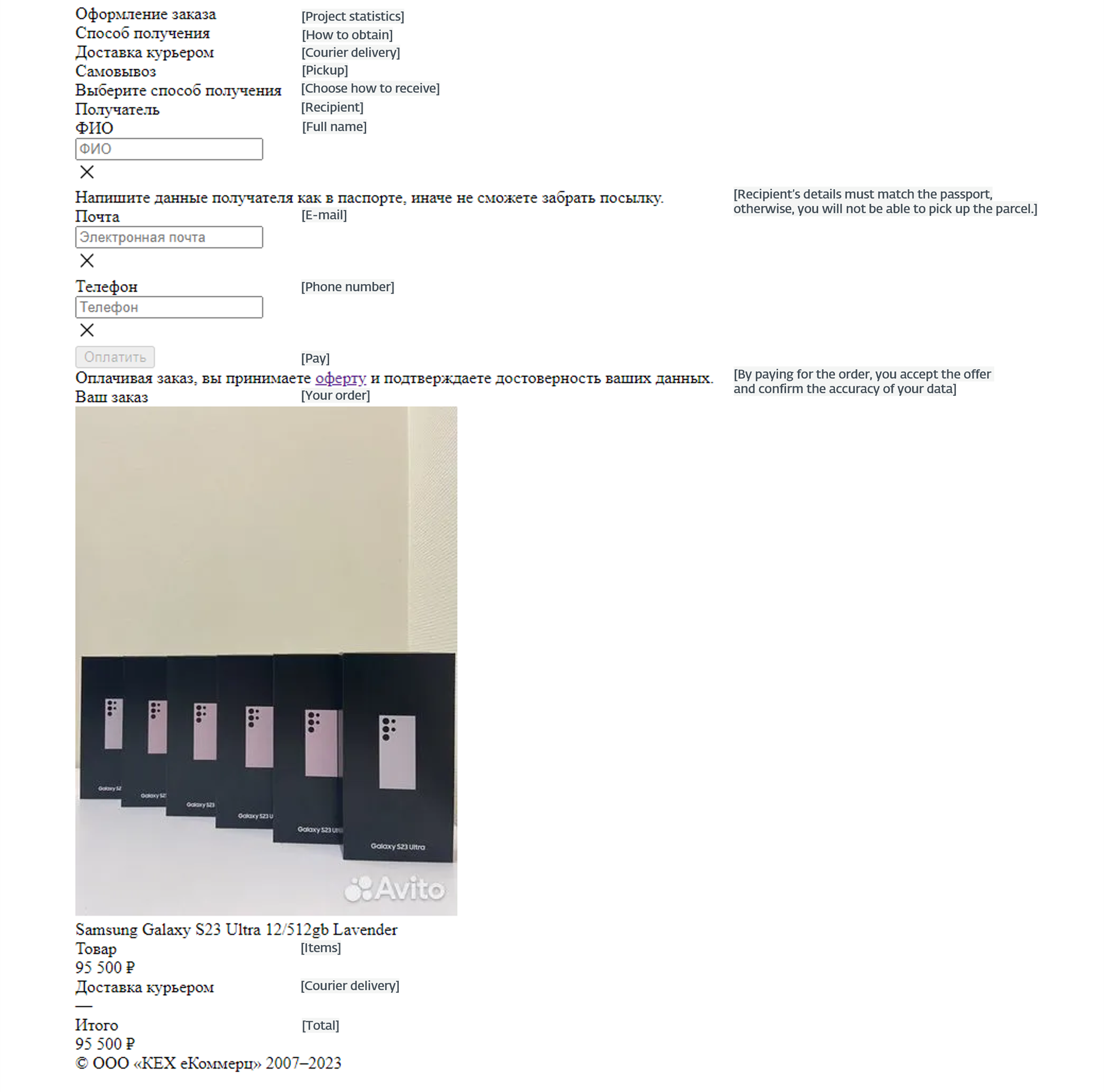
Determine 5. Crammed in uncompleted phishing web site template (machine translations in brackets)
The completed product is seen in Determine 6, an eBay net web page look-alike that’s virtually unrecognizable from the unique (or at the very least seems to be like one thing one would anticipate from the legit web site). By clicking the Obtain %amount2% EUR button, a Mammoth is proven a faux credit score/debit card gateway.
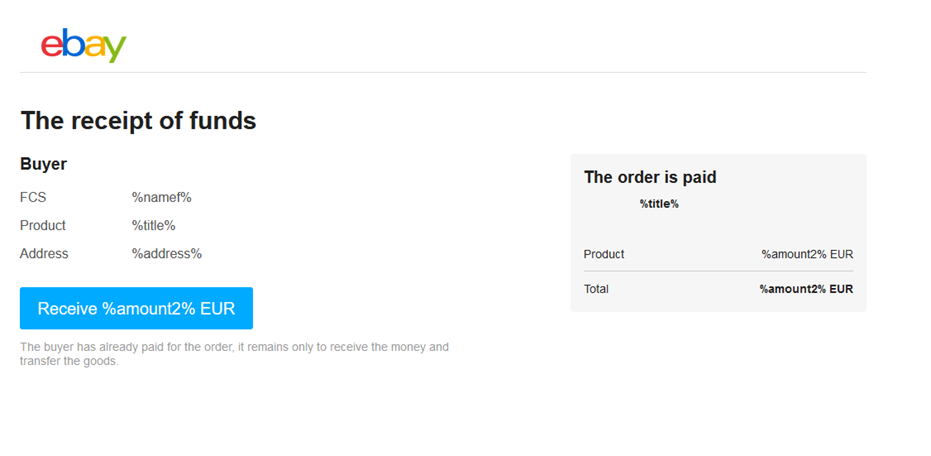
Determine 6. Completed template for phishing net web page impersonating eBay
These phishing domains will not be simple to identify. Often, Neanderthals register a website after which create subdomains for every focused market in such a approach that the ultimate URL begins with the anticipated model identify. In Desk 1 discover that just one area – olx.id7423[.]ru – is used to focus on the favored market OLX. An instance of a legit area for the OLX market is olx.ua. Briefly, they often use .ru as their top-level domains and transfer second-level domains to the third-level area’s place.
Desk 1. Examples of a number of domains used for phishing
|
Service identify (RU) |
Service identify |
Phishing area |
Reliable area |
|
Авито |
Avito |
avito.id7423[.]ru |
avito.ru |
|
Юла |
Youla |
youla.id7423[.]ru |
youla.ru |
|
Боксберри |
Boxberry |
boxberry.id7423[.]ru |
boxberry.ru |
|
Сдек |
Cdek |
cdek.id7423[.]ru |
cdek.ru |
|
Авито Аренда |
Avito-rent |
avito-rent.id7423[.]ru |
avito.ru |
|
OLX KZ |
OLX |
olx.id7423[.]ru |
olx.kz |
|
Куфар |
Kufar |
kufar.id7423[.]ru |
kufar.by |
|
OLX UZ |
OLX UZ |
olx.id7423[.]ru |
olx.uz |
|
OLX RO |
OLX RO |
olx.id7423[.]ru |
olx.ro |
|
OLX PL |
OLX PL |
olx.id7423[.]ru |
olx.pl |
|
OLX UA |
OLX UA |
olx.id7423[.]ru |
olx.ua |
|
СБАЗАР |
Sbazar |
sbazar.id7423[.]ru |
sbazar.cz |
|
IZI ua |
IZI ua |
izi.id7423[.]ru |
izi.ru |
|
OLX BG |
OLX BG |
olx.id7423[.]ru |
olx.bg |
Transactions and payout
Neanderthals don’t switch cash stolen from Mammoths to their very own accounts. As a substitute, all of the Neanderthals use a shared Telekopye account managed by the Telekopye administrator. Telekopye retains monitor of how profitable every Neanderthal is by logging related contributions to that shared account – both in a easy textual content file or a SQL database.
As a consequence, Neanderthals receives a commission by the Telekopye administrator. Cost is cut up into three elements:
1. Fee to the Telekopye administrator.
2. Fee to recommender (suggestion system is mentioned later within the weblog submit).
3. Precise payout.
The fee to the Telekopye administrator is 5–40%, relying on the Telekopye model and Neanderthal function (roles are additionally mentioned later within the weblog submit).
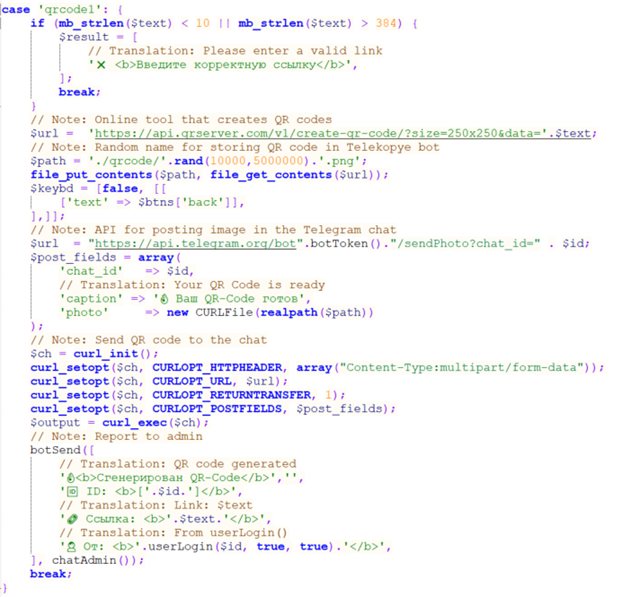
As soon as a Neanderthal turns into eligible for a payout, he asks Telekopye for one. Telekopye checks the Neanderthal’s stability, closing request is permitted by the Telekopye administrator and, lastly, funds are transferred to the Neanderthal’s cryptocurrency pockets. In some Telekopye implementations, step one, asking for a payout, is automated and the negotiation is initiated at any time when a Neanderthal reaches a sure threshold of stolen cash from efficiently pulled off scams (e.g., 500 RUB). The method of the handbook payout request is illustrated in Determine 7 and the related a part of the Telekopye supply code in Determine 8.
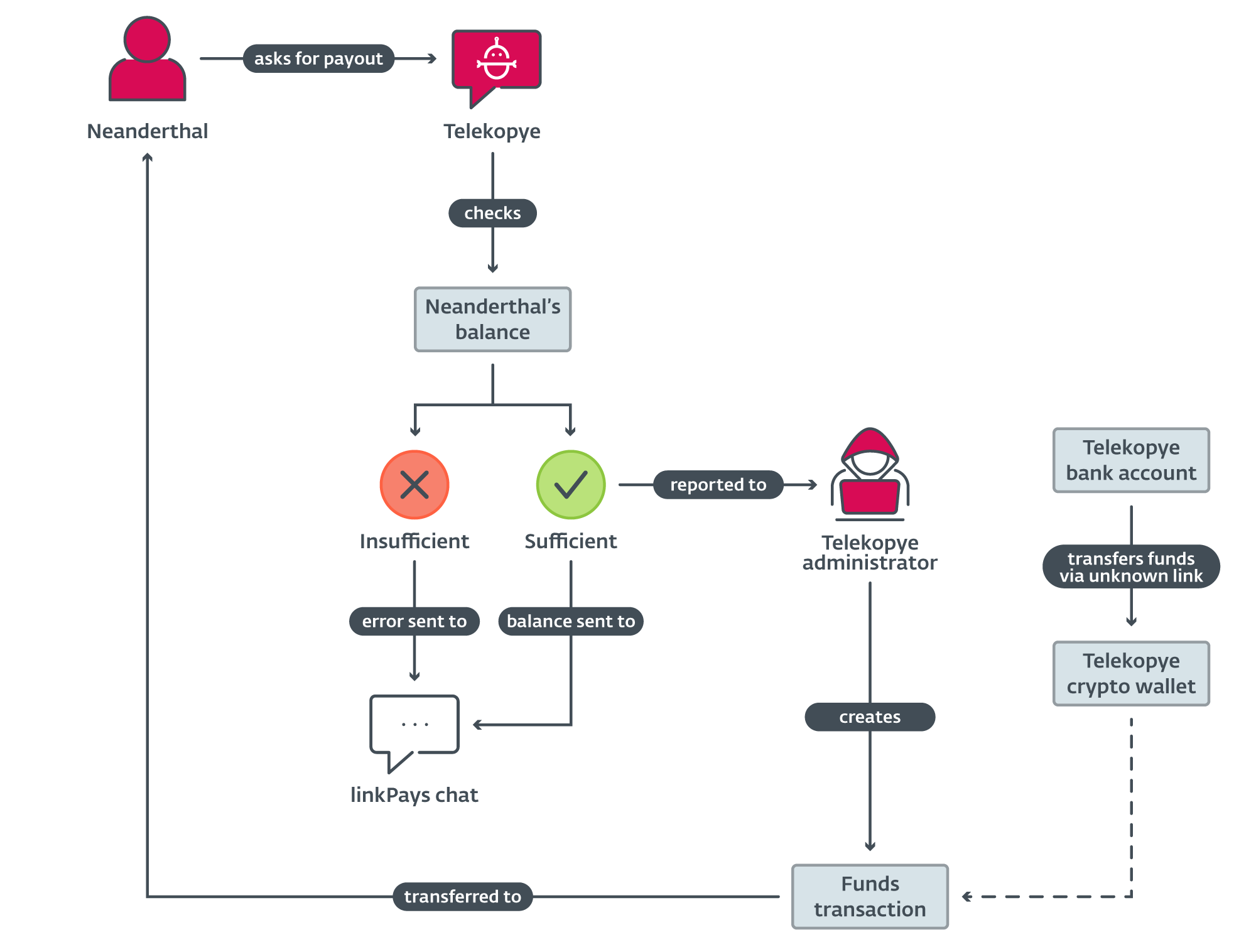

Determine 8. Code that’s executed at any time when a Neanderthal needs to withdraw funds
Telekopye retains logs of processed payouts in a separate Telegram channel. A Neanderthal who’s paid additionally receives a hyperlink to this channel, most likely to have the ability to confirm that the transaction is logged. Determine 9 exhibits an instance of such a logs channel.
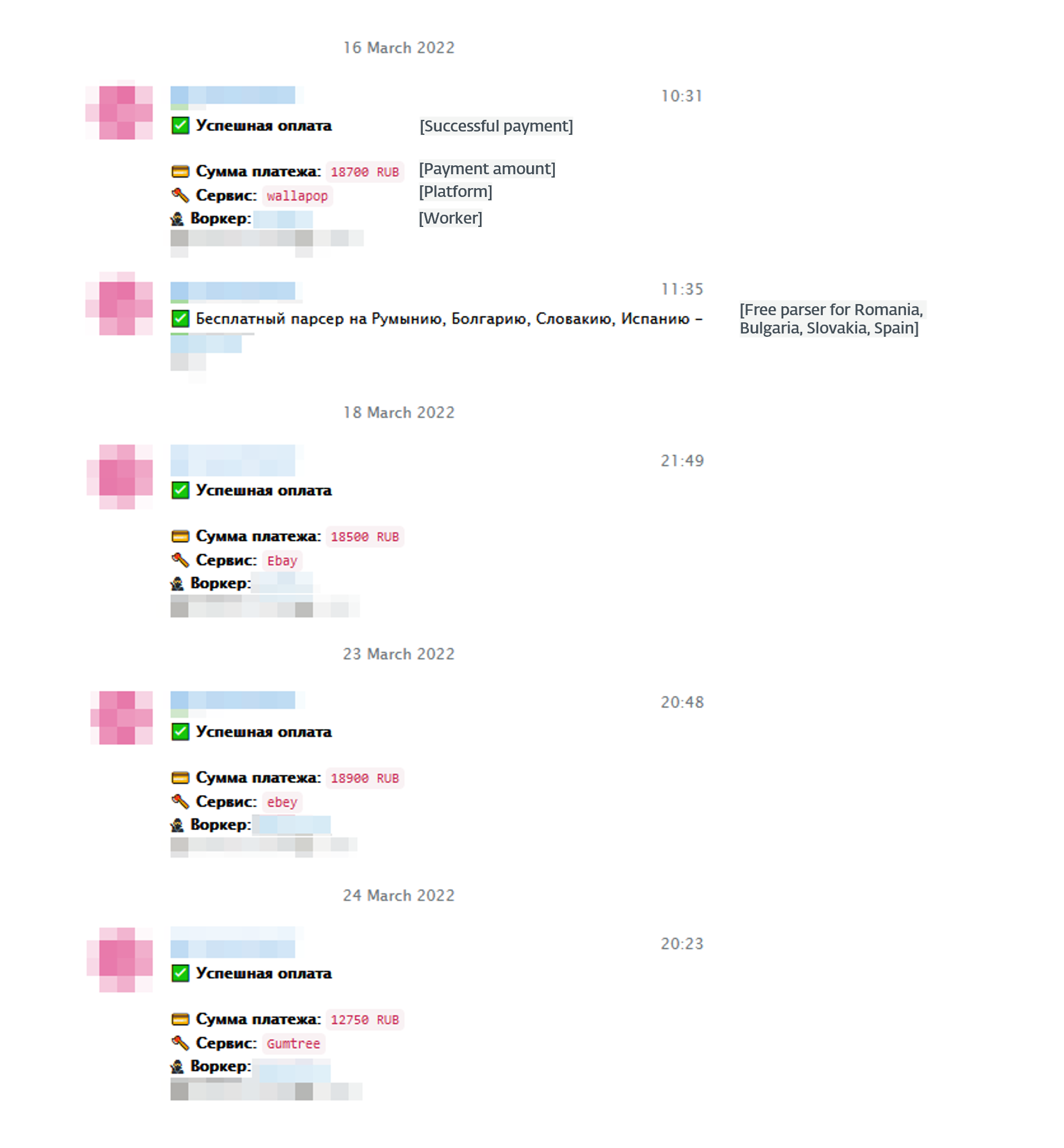
The Telekopye administrator doesn’t switch the cash via Telekopye itself. As a substitute, the admin makes use of both a software referred to as “BTC Alternate bot”, probably an unbiased Telegram bot, or transfers the cash manually. Nonetheless, we’ve got noticed rising integration of payout-related options into Telekopye, so this will likely change sooner or later.
Sending phishing e mail
Neanderthals can instruct Telekopye to create and ship e mail messages. The sender is a predefined e mail account shared between all of the Neanderthals. These e mail accounts are usually related to the phishing domains arrange by Neanderthals. Determine 10 exhibits the code to spoof the e-mail headers From and Reply-To in order that the e-mail messages seem extra legit.
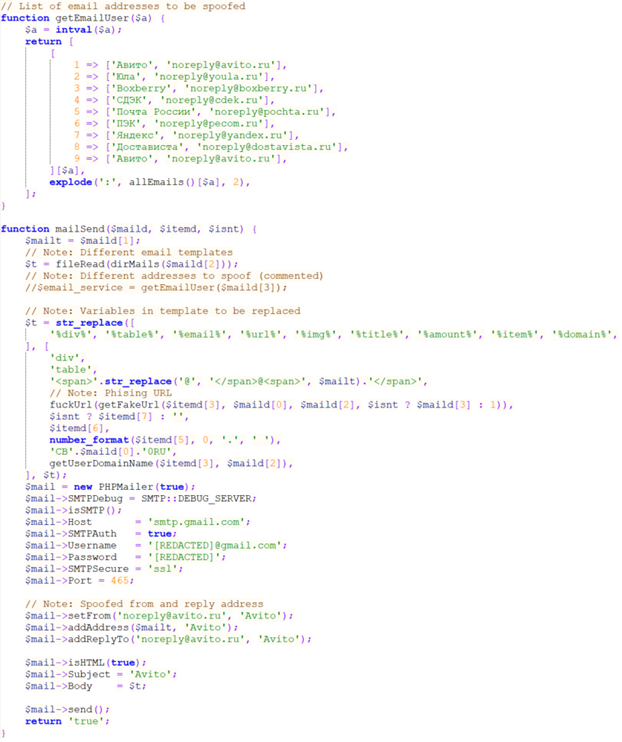
Determine 10. Code to craft phishing emails with a faux URL and spoofed sender deal with
Determine 11 exhibits one in every of many templates used to create phishing e mail our bodies. No extra info has been given, so default values are proven, as an alternative of user-defined textual content, for %title% and %quantity%. A malicious URL is hidden behind the “Go to cost” button.
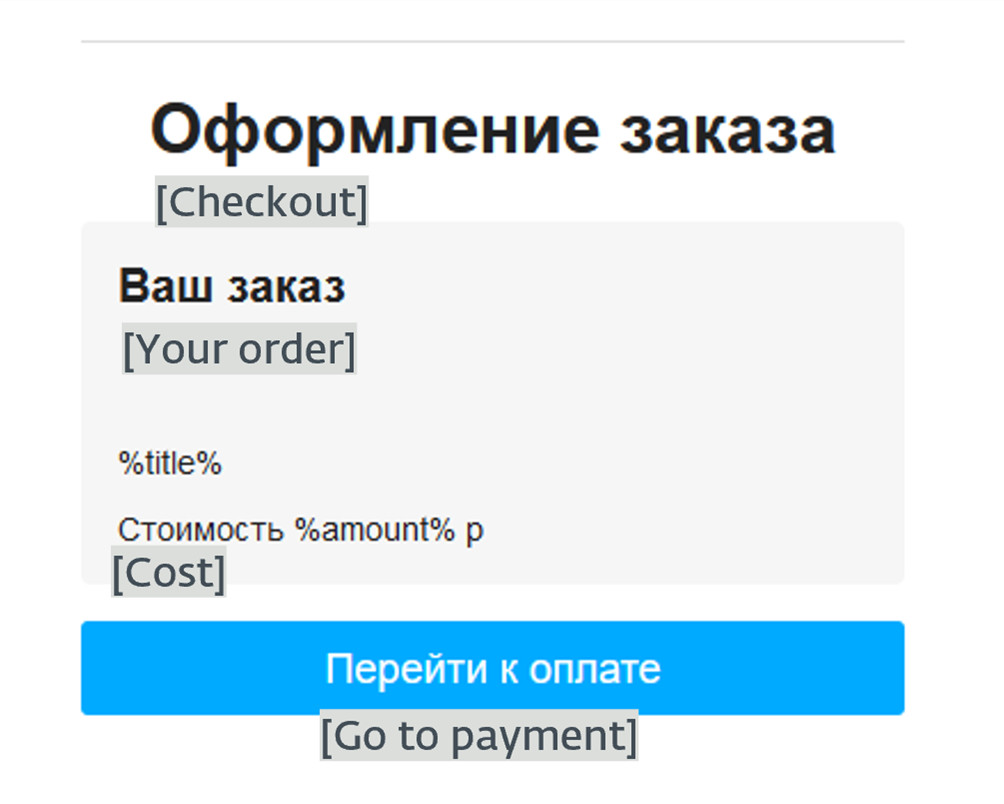
Determine 11. Electronic mail template that imitates a easy checkout e mail
SMS help
In addition to phishing emails, Telekopye permits Neanderthals to create and ship SMS messages in an analogous method. Determine 12 illustrates the piece of code accountable for creating and sending such messages.

Determine 12. A part of the code to create SMS messages utilizing the net service [legitimate] smscab.ru
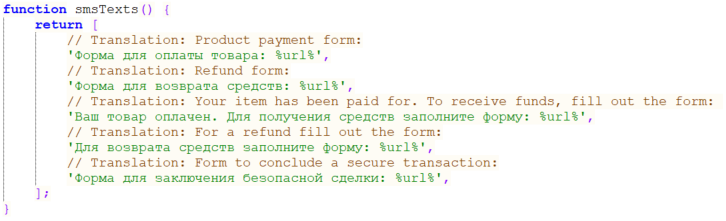
Some implementations of Telekopye even have predefined SMS texts in several languages. All SMS templates say kind of the identical factor, for instance, “Your merchandise has been paid for. To obtain funds, fill out the shape: <malicious_link>”. Examples of a number of SMS templates are proven in Determine 13, the place unique Russian templates are proven.How this SMS seems to be when a Mammoth receives it may be seen in Determine 14.
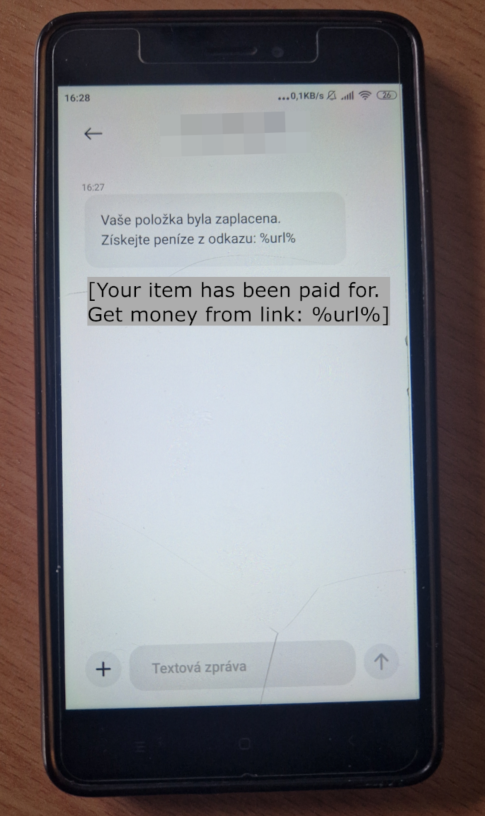
Determine 14. Instance of an SMS created with a template textual content in Czech and acquired with out a malicious hyperlink
Telekopye depends closely on on-line companies akin to smscab.ru or smshub.org to ship SMS messages. We’ve analyzed an older variant, the place Telekopye used one hardcoded telephone quantity shared amongst all Neanderthals. Nonetheless, probably as a result of blocking one telephone quantity would end in blocking all Neanderthals’ messages, this function was discontinued.
Picture manipulation
On this part, we describe how easy it’s for Neanderthals utilizing Telekopye to create convincing pictures and screenshots. Some variations of Telekopye have a part referred to as Render bot. Though Render bot could possibly be categorised as a standalone bot, we’ll deal with it as a part of Telekopye.
When Render bot is added to a Telegram chat, we’re greeted with the preliminary message seen in Determine 15.
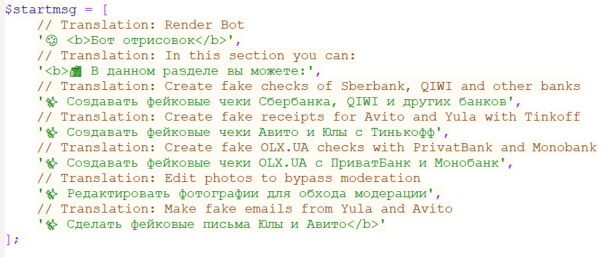
This provides us good perception into how this a part of Telekopye works. We will classify the makes use of of Render bot into two classes. First, it may be used to mangle pictures in order that they aren’t simple to cross-reference. Second, it could create faux pictures that are supposed to seem like legit screenshots. On this part, we’ll focus first on the creation of those faux screenshots, a function just like creating phishing web sites.
In contrast to faux net pages which are generated from HTML templates, the bottom for faux screenshots is a JPG picture with some key elements eliminated. These elements embrace the supposed paid worth, debit/bank card quantity, title, identify, and many others. This transformation is proven in Determine 16, the place there’s a side-by-side comparability of a plain template and a stuffed template. As a result of these are pictures, there are not any interactive buttons, not like the e-mail and phishing net web page counterparts.
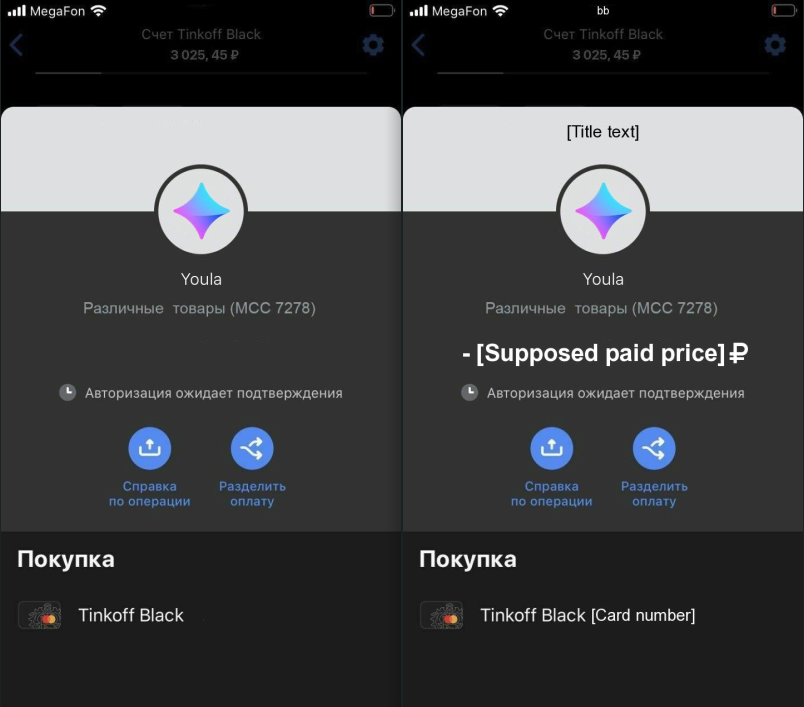
Determine 16. Generated faux screenshot (template on the left, template crammed with pattern textual content on the precise)
There’s a excessive emphasis on making the inserted textual content match in addition to potential, so Telekopye helps a number of completely different fonts. Simply as beforehand, all habits is hardcoded and no AI is used. We discovered 9 templates for Sberbank, Avito, Youla, Qiwi, and some different companies.
From the Neanderthals’ perspective, creating these screenshots is not any completely different from creating phishing net pages. A Neanderthal solely wants to produce a couple of bits of knowledge, and Telekopye creates a faux screenshot/picture from them.
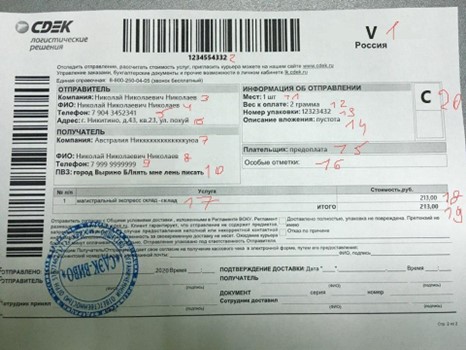
In Render bot folders it is usually potential to see one in every of these templates within the strategy of creation. Determine 17 exhibits a photograph of an bill for a parcel, with numbered fields. Builders of Telekopye erase all fields with numbers subsequent to them and attempt to match their very own font model and font measurement in them. When they’re glad with how the ultimate product seems to be, they add it to the bot for different Neanderthals to make use of as a brand new template.
One other no much less essential performance of this a part of Telekopye is picture manipulation. From the code and its feedback, it’s potential to assemble that it is ready to change pictures of marketed items in order that engines like google can not cross-reference them. We assume that if the picture was discovered on an internet market, AI antispam safety would flag it as malicious. This transformation may be very easy and consists of a vertical flip of the picture and a small change in distinction.
Experimental options
Due to content material from Telekopye supply information, we assess that the builders try to experiment with differing types/variations of the rip-off. For instance, within the code, we see QR code era performance (Determine 18). This would possibly imply one in every of two issues. Both it’s a part of the payout course of or they’re making an attempt to make it a brand new trick for scamming. A possible purpose is that Mammoths don’t assume twice when paying by way of a QR code. So we estimate that there’s going to be a small enhance in scams utilizing these sorts of methods.
From Determine 15 it seems to be as if Render bot can create faux checks for Sberbank. However in actuality, it could solely create cost confirmations (Determine 19).

Roles
Teams of scammers utilizing Telekopye are organized right into a hierarchy with least to most privileges so as as follows:
1. Directors
2. Moderators
3. Good staff / Help bots
4. Staff
5. Blocked
We’ve noticed some variants enriching this checklist with a couple of additions, however these 5 roles stay the idea. We give attention to every function in additional element within the sections beneath.
Telekopye additionally employs a referral system. When a brand new Neanderthal needs to affix the group, he must fill in an utility (how a lot “business” expertise he has, who invited him, and many others.). This utility then must be accepted by Moderators or Directors to ensure that the brand new Neanderthal to affix.
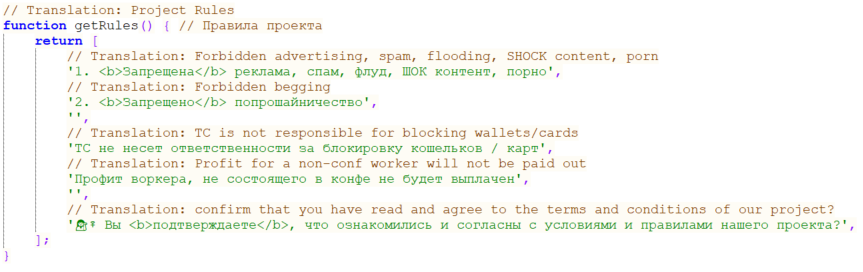
Blocked
A consumer with this function just isn’t ready to make use of any a part of the Telekopye toolkit. Guidelines which are a part of Telekopye supply code recommend that is some kind of punishment for breaking them (Determine 20).
Staff
That is the most typical function that the majority new Neanderthals begin with. With this function, Neanderthals are ready to make use of each Telekopye function, excluding moderation of the group. Throughout payout, this function has the worst fee charges, as seen in Desk 2.
Desk 2. Instance of payout charges
|
Position |
Fee to |
Fee to recommender |
Precise payout |
|
Staff |
33% |
2% |
65% |
|
Good staff/Help bots |
23% |
2% |
75% |
Good staff/Help bots
This function is a direct improve of the Employee function. The one distinction is that Neanderthals with this function don’t have to offer such a big proportion of their payout to the platform proprietor.
To get this function, Neanderthals should show their usefulness – pull off a variety of scams or obtain a certain quantity of stolen funds.
Typically it’s potential to see that this function is reserved for help bots. We’re not sure what these bots are.
Moderators
Moderators can promote and demote different members and approve new members. They can’t modify Telekopye settings.
Directors
Directors are the very best function within the group. They will use Telekopye to its full extent. On high of moderators’ capabilities, they’ll modify Telekopye settings – add phishing net web page templates, change/add e mail addresses that the bot makes use of, and alter payout charges, payout kind, and many others.
Easy methods to keep away from being scammed
The simplest strategy to inform whether or not you’re being focused by a Neanderthal making an attempt to steal your cash is by trying on the language used. It may be the language utilized in dialog, e mail, or on the net web page itself. Sadly, this isn’t foolproof, and it has been noticed that a few of these rip-off makes an attempt have ironed out grammar and vocabulary errors.
Insist on in-person cash and items alternate at any time when potential when coping with secondhand items on on-line marketplaces. Such trades will not be protected by well-known establishments or companies. These scams are solely potential as a result of Neanderthals fake they already paid on-line/despatched an merchandise. Sadly, generally in-person supply just isn’t potential and in that case you could be additional cautious.
Keep away from sending cash except you’re sure the place it’s going to go. When you could ship cash someplace, examine the net web page for grammatical errors and graphical disproportions. In case you are fortunate, a template can have some inaccuracies. Additionally examine the web site certificates and look intently on the URL, which could be made to seem like an actual hyperlink.
Be careful for strong-arm arguments like “I’ll ship cash via service XYZ. Are you aware the way it works?”. Ask if one other cost kind is feasible and particularly if they’re keen to just accept cost from a service you’re acquainted with. This isn’t foolproof as a result of scammers have a number of templates, however you would possibly be capable of acknowledge a faux template extra simply while you use a cost methodology recognized to you.
Be additional cautious when clicking on hyperlinks in SMS messages or emails, even when they appear as if they arrive from a good supply. Neanderthals are not any strangers to e mail spoofing. A great rule of thumb is to ask your self whether or not you got one thing that may make respected sources ship you emails like that. In case you are not sure, go to the supposed service’s web site straight (not utilizing the hyperlink within the e mail/SMS) and ask. Most of those pages have buyer help and they’re going to fortunately provide you with a hand.
Conclusion
We found and analyzed Telekopye, a toolkit that helps much less technical individuals pull off on-line scams extra simply. We estimate that Telekopye was in use since at the very least 2015. We targeted on one model, analyzing its major capabilities and uncovering how Telekopye works internally. These capabilities embrace creating phishing web sites, sending phishing SMS and emails, and creating faux screenshots. We additionally described the hierarchy of teams utilizing Telekopye. Due to our telemetry, we additionally came upon that this software remains to be in use and in lively improvement. The second Telekopye weblog submit, which can be launched later, uncovers the interior working of the rip-off teams.
Acknowledgement
The writer want to thank Ondřej Novotný for the preliminary discovery.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis provides non-public APT intelligence experiences and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
A complete checklist of Indicators of Compromise and samples can be found in our GitHub repository.
Information
|
SHA-1 |
Filename |
Detection |
Description |
|
26727D5FCEEF79DE2401CA0C9B2974CD99226DCB |
rip-off.php |
PHP/HackTool.Telekopye.A |
Telekopye rip-off toolkit |
|
285E0573EF667C6FB7AEB1608BA1AF9E2C86B452 |
tinkoff.php |
PHP/HackTool.Telekopye.A |
Telekopye rip-off toolkit |
|
8A3CA9EFA2631435016A4F38FF153E52C647146E |
600be5ab7f0513833336bec705ca9bcfd1150a2931e61a4752b8de4c0af7b03a.php |
PHP/HackTool.Telekopye.A |
Telekopye rip-off toolkit |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
N/A |
id23352352.ru |
Cloudflare |
2023-07-04 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
id8092.ru |
Cloudflare |
2023-06-26 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
id2770.ru |
Cloudflare |
2023-06-28 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
id83792.ru |
Cloudflare |
2023-06-17 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
id39103.ru |
Cloudflare |
2023-06-19 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
2cdx.website |
Cloudflare |
2021-03-21 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
3inf.website |
Cloudflare |
2021-03-12 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
pay-sacure4ds.ru |
Jino |
2021-12-27 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
id7423.ru |
Cloudflare |
2021-03-27 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
id2918.website |
Jino |
2021-03-08 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
formaa.ga |
Zomro |
2021-05-30 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
id0391.ru |
Cloudflare |
2023-06-23 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
id66410.ru |
Cloudflare |
2023-06-17 |
Area that’s used to check toolkit or rip-off sufferer. |
|
N/A |
id82567.ru |
Cloudflare |
2023-06-07 |
Area that’s used to check toolkit or rip-off sufferer. |
MITRE ATT&CK methods
This desk was constructed utilizing model 13 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Identify |
Description |
|
Reconnaissance |
Collect Sufferer Id Info |
Telekopye is used to assemble debit/bank card particulars, telephone numbers, emails, and many others. by way of phishing net pages. |
|
|
Useful resource Improvement |
Purchase Infrastructure: Domains |
Telekopye operators register their very own domains. |
|
|
Set up Accounts |
Telekopye operators set up accounts on on-line marketplaces. |
||
|
Set up Accounts: Electronic mail Accounts |
Telekopye operators arrange e mail addresses related to the domains they register. |
||
|
Compromise Accounts: Electronic mail Accounts |
Telekopye operators use compromised e mail accounts to extend their stealthiness. |
||
|
Develop Capabilities: Malware |
Telekopye is customized malware. |
||
|
Preliminary Entry |
Phishing: Spearphishing Hyperlink |
Telekopye sends hyperlinks to phishing web sites in emails or SMS messages. |
|
|
Assortment |
Enter Seize: Net Portal Seize |
Net pages created by Telekopye seize delicate info and report it to operators. |

