A beforehand undetected assault technique referred to as NoFilter has been discovered to abuse the Home windows Filtering Platform (WFP) to realize privilege escalation within the Home windows working system.
“If an attacker has the power to execute code with admin privilege and the goal is to carry out LSASS Shtinkering, these privileges usually are not sufficient,” Ron Ben Yizhak, a safety researcher at Deep Intuition, advised The Hacker Information.
“Operating as “NT AUTHORITYSYSTEM” is required. The strategies described on this analysis can escalate from admin to SYSTEM.”
The findings had been offered on the DEF CON safety convention over the weekend.

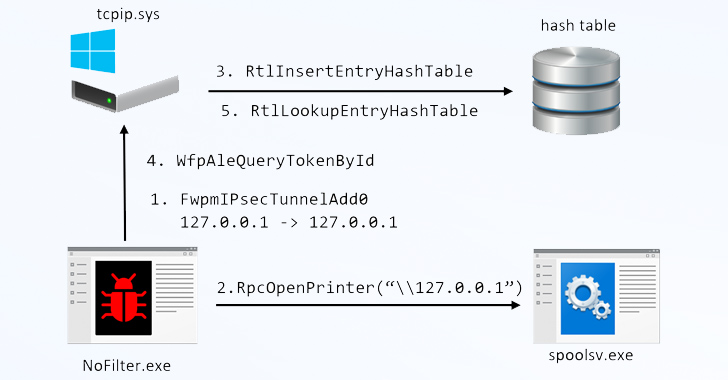
The place to begin of the analysis is an in-house device referred to as RPC Mapper the cybersecurity firm used to map distant process name (RPC) strategies, particularly people who invoke WinAPI, resulting in the invention of a technique named “BfeRpcOpenToken,” which is a part of WFP.
WFP is a set of API and system providers that is used to course of community visitors and permit configuring filters that let or block communications.
“The deal with desk of one other course of will be retrieved by calling NtQueryInformationProcess,” Ben Yizhak stated. “This desk lists the tokens held by the method. The handles to these tokens will be duplicated for one more course of to escalate to SYSTEM.”

Whereas entry tokens serve to establish the person concerned when a privileged activity is executed, a bit of malware operating in person mode can entry tokens of different processes utilizing particular features (e.g., DuplicateToken or DuplicateHandle) after which use that token to launch a baby course of with SYSTEM privileges.
However the aforementioned method, per the cybersecurity agency, will be modified to carry out the duplication within the kernel by way of WFP, making it each evasive and stealthy by leaving barely any proof or logs.
In different phrases, the NoFilter can launch a brand new console as “NT AUTHORITYSYSTEM” or as one other person that’s logged on to the machine.
“The takeaway is that new assault vectors will be discovered by trying into built-in elements of the OS, such because the Home windows Filtering Platform,” Ben Yizhak stated, including the strategies “keep away from WinAPI which might be monitored by safety merchandise.”