A malicious toolset dubbed Spacecolon is being deployed as a part of an ongoing marketing campaign to unfold variants of the Scarab ransomware throughout sufferer organizations globally.
“It in all probability finds its means into sufferer organizations by its operators compromising weak internet servers or through brute forcing RDP credentials,” ESET safety researcher Jakub Souček stated in an in depth technical write-up revealed Tuesday.
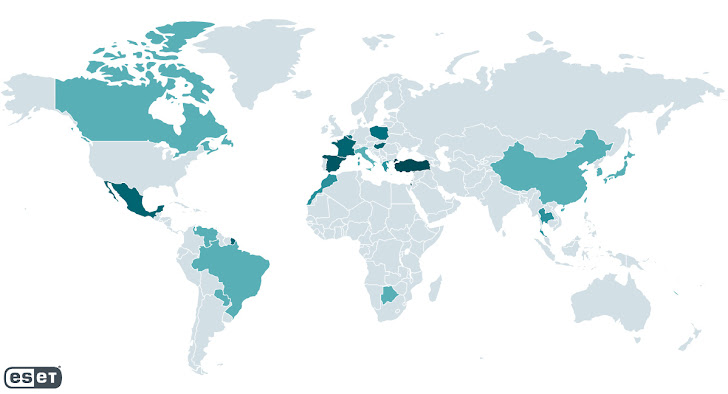
The Slovak cybersecurity agency, which dubbed the menace actor CosmicBeetle, stated the origins of the Spacecolon date again to Might 2020. The very best focus of victims has been detected in France, Mexico, Poland, Slovakia, Spain, and Turkey.
Whereas the precise provenance of the adversary is unclear, a number of Spacecolon variants are stated to comprise Turkish strings, doubtless pointing to the involvement of a Turkish-speaking developer. There isn’t any proof at the moment linking it to every other identified menace actor group.

Among the targets embody a hospital and a vacationer resort in Thailand, an insurance coverage firm in Israel, a neighborhood governmental establishment in Poland, an leisure supplier in Brazil, an environmental firm in Turkey, and a college in Mexico.
“CosmicBeetle doesn’t select its targets; fairly, it finds servers with vital safety updates lacking and exploits that to its benefit,” Souček identified.
It is price noting that Spacecolon was first documented by Polish firm Zaufana Trzecia Strona in early February 2023, doubtless prompting the adversary to tweak its arsenal in response to public disclosures.
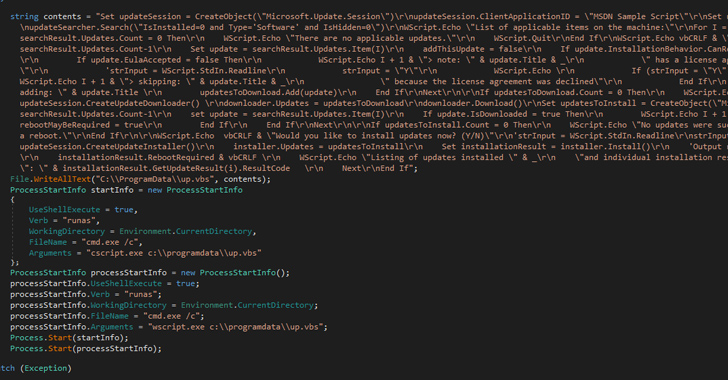
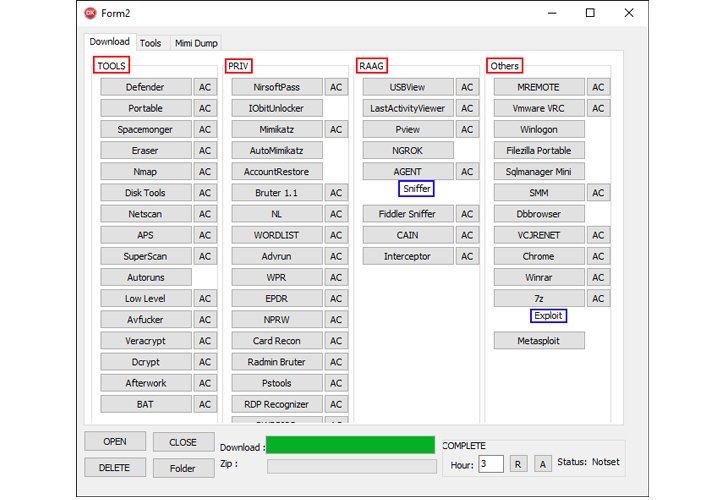
The first element of Spacecolon is ScHackTool, a Delhi-based orchestrator that is used to deploy an installer, which, because the identify implies, installs ScService, a backdoor with options to execute customized instructions, obtain and execute payloads, and retrieve system info from compromised machines.
ScHackTool additionally features as a conduit to arrange a wide selection of third-party instruments fetched from a distant server (193.149.185[.]23). The last word aim of the assaults is to leverage the entry afforded by ScService to ship a variant of the Scarab ransomware.

An alternate model of the an infection chain recognized by ESET entails using Impacket to deploy ScService versus utilizing ScHackTool, indicating that the menace actors are experimenting with completely different strategies.
CosmicBeetle’s monetary motives are additional bolstered by the truth that the ransomware payload additionally drops a clipper malware to maintain tabs on the system clipboard and modify cryptocurrency pockets addresses to these beneath the attacker’s management.
Moreover, there’s proof that the adversary is actively growing a brand new ransomware pressure dubbed ScRansom, which makes an attempt to encrypt all arduous, detachable, and distant drives utilizing the AES-128 algorithm with a key generated from a hard-coded string.
“CosmicBeetle does not make a lot effort to cover its malware and leaves loads of artifacts on compromised techniques,” Souček stated. “Little to no anti-analysis or anti-emulation methods are carried out. ScHackTool depends closely on its GUI, however, on the similar time, accommodates a number of nonfunctional buttons.”
“CosmicBeetle operators use ScHackTool primarily to obtain further instruments of option to compromised machines and run them as they see match.”