Cybersecurity researchers have found a case of privilege escalation related to a Microsoft Entra ID (previously Azure Energetic Listing) utility by benefiting from an deserted reply URL.
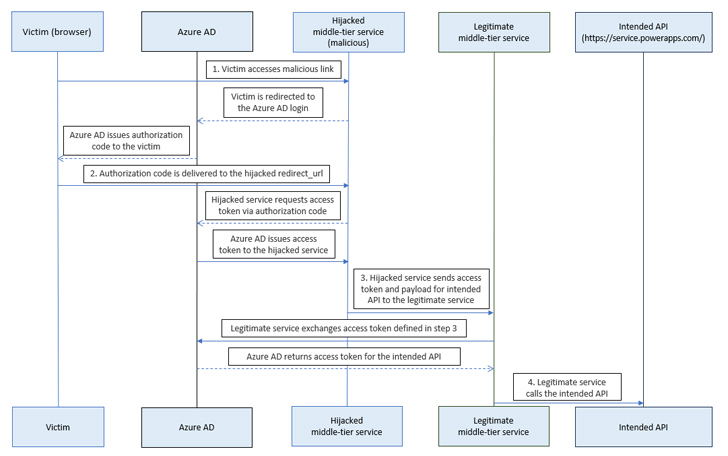
“An attacker may leverage this deserted URL to redirect authorization codes to themselves, exchanging the ill-gotten authorization codes for entry tokens,” Secureworks Counter Risk Unit (CTU) stated in a technical report printed final week.
“The menace actor may then name Energy Platform API through a middle-tier service and acquire elevated privileges.”
Following accountable disclosure on April 5, 2023, the problem was addressed by Microsoft through an replace launched a day later. Secureworks has additionally made obtainable an open-source device that different organizations can use to scan for deserted reply URLs.

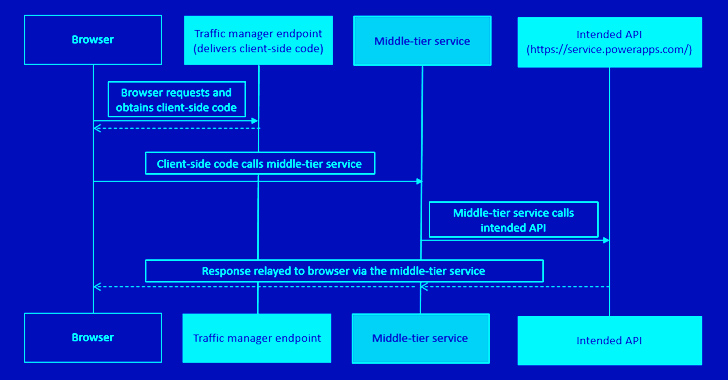
Reply URL, additionally referred to as redirect URI, refers back to the location the place the authorization server sends the person as soon as the app has been efficiently licensed and granted an authorization code or entry token.
“The authorization server sends the code or token to the redirect URI, so it is vital you register the proper location as a part of the app registration course of,” Microsoft notes in its documentation.
Secureworks CTU stated it recognized an deserted Dynamics Knowledge Integration app reply URL related to the Azure Visitors Supervisor profile that made it doable to invoke the Energy Platform API through a middle-tier service and tamper with the setting configurations.
In a hypothetical assault state of affairs, this might have been used to amass the system administrator position for an present service principal and ship requests to delete an setting, in addition to abuse the Azure AD Graph API to collect details about the goal with a purpose to stage follow-on actions.
This, nonetheless, banks on the chance {that a} sufferer clicks on a malicious hyperlink, because of which the authorization code issued by Microsoft Entra ID upon logging is delivered to a redirect URL hijacked by the menace actor.

The disclosure comes as Kroll revealed an uptick in DocuSign-themed phishing campaigns using open redirects, enabling adversaries to propagate specifically crafted URLs that, when clicked, redirect potential victims to a malicious web site.
“By crafting a misleading URL that leverages a reliable web site, malicious actors can extra simply manipulate customers into clicking the hyperlink, in addition to deceiving/bypassing community know-how that scans hyperlinks for malicious content material,” Kroll’s George Glass stated.
“This ends in a sufferer being redirected to a malicious web site designed to steal delicate info, resembling login credentials, bank card particulars or private knowledge.”