
The Microsoft personal encryption key stolen by Storm-0558 Chinese language hackers supplied them with entry far past the Trade On-line and Outlook.com accounts that Redmond mentioned have been compromised, based on Wiz safety researchers.
Redmond revealed on July twelfth that the attackers had breached the Trade On-line and Azure Energetic Listing (AD) accounts of round two dozen organizations. This was achieved by exploiting a now-patched zero-day validation challenge within the GetAccessTokenForResourceAPI, permitting them to forge signed entry tokens and impersonate accounts inside the focused organizations.
The affected entities included authorities businesses within the U.S. and Western European areas, with the U.S. State and Commerce Departments amongst them.
On Friday, Wiz safety researcher Shir Tamari mentioned that the affect prolonged to all Azure AD functions working with Microsoft’s OpenID v2.0. This was as a result of stolen key’s capacity to signal any OpenID v2.0 entry token for private accounts (e.g., Xbox, Skype) and multi-tenant AAD apps.
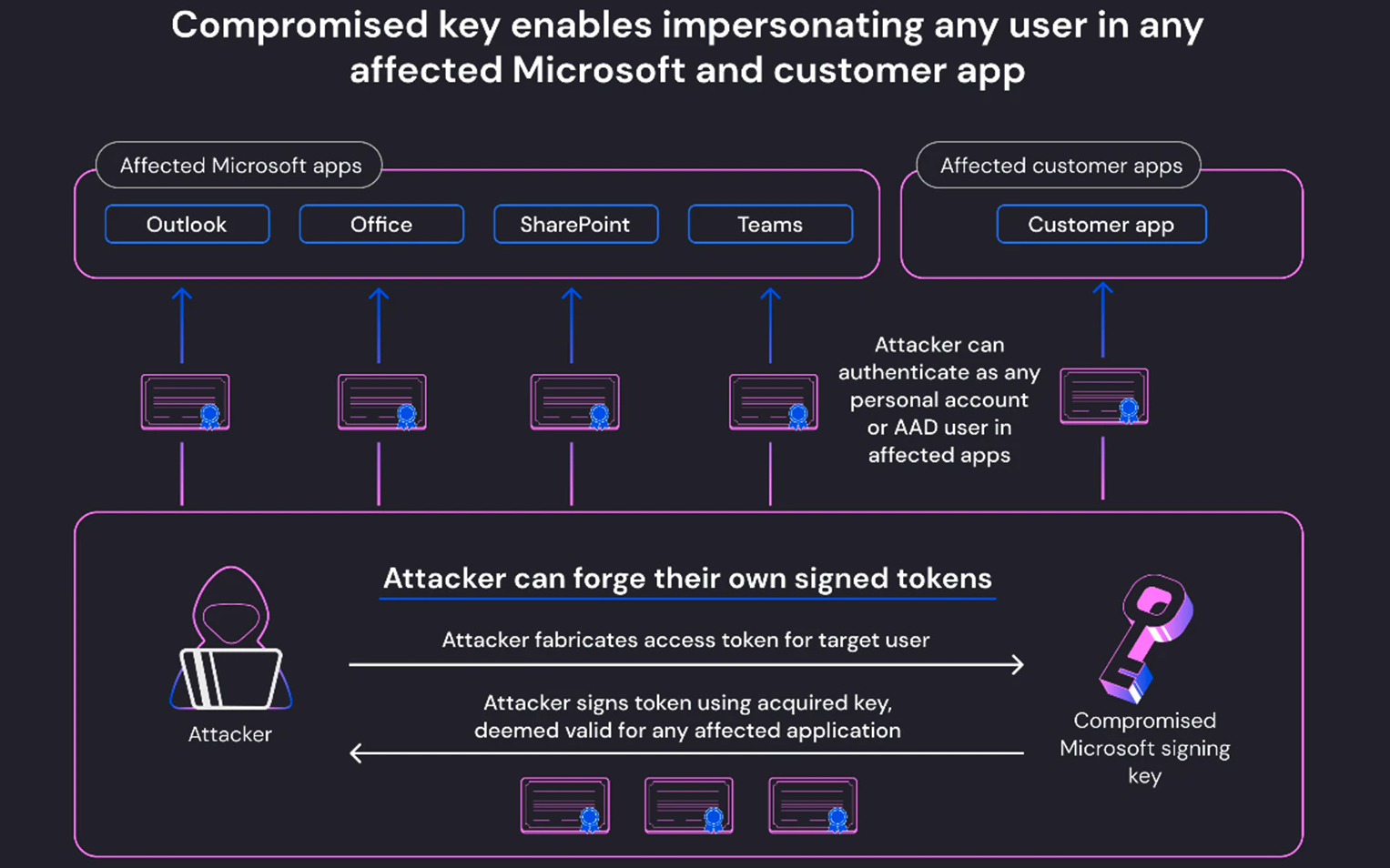
Whereas Microsoft mentioned that solely Trade On-line and Outlook have been impacted, Wiz says the menace actors may use the compromised Azure AD personal key to impersonate any account inside any impacted buyer or cloud-based Microsoft software.
“This consists of managed Microsoft functions, corresponding to Outlook, SharePoint, OneDrive, and Groups, in addition to clients’ functions that assist Microsoft Account authentication, together with those that enable the ‘Login with Microsoft’ performance,” Tamari mentioned.
“All the pieces on the planet of Microsoft leverages Azure Energetic Listing auth tokens for entry,” Wiz CTO and Cofounder Ami Luttwak additionally instructed BleepingComputer.
“An attacker with an AAD signing secret’s essentially the most highly effective attacker you possibly can think about, as a result of they’ll entry nearly any app – as any person. That is the last word cyber intelligence’ form shifter’ superpower.”
In response to the safety breach, Microsoft revoked all legitimate MSA signing keys to make sure that the menace actors did not have entry to different compromised keys.
This measure additionally thwarted any makes an attempt to generate new entry tokens. Additional, Redmond relocated the newly generated entry tokens to the important thing retailer for the corporate’s enterprise techniques.
After invalidating the stolen enterprise signing key, Microsoft discovered no additional proof suggesting further unauthorized entry to its clients’ accounts utilizing the identical auth token forging approach.
Moreover, Microsoft reported observing a shift in Storm-0558 ways, displaying that the menace actors now not had entry to any signing keys.
Final however not least, the corporate revealed final Friday that it nonetheless does not know how the Chinese language hackers stole the Azure AD signing key. Nevertheless, after stress from CISA, they agreed to develop entry to cloud logging knowledge without cost to assist defenders detect comparable breach makes an attempt sooner or later.
Earlier than this, these logging capabilities have been solely accessible to Microsoft clients who paid for Purview Audit (Premium) logging license. Because of this, Microsoft confronted appreciable criticism for impeding organizations from promptly detecting Storm-0558 assaults.
“At this stage, it’s arduous to find out the total extent of the incident as there have been tens of millions of functions that have been probably weak, each Microsoft apps and buyer apps, and the vast majority of them lack the adequate logs to find out in the event that they have been compromised or not,” Tamari concluded right now.
