A malicious actor has been linked to a cloud credential stealing marketing campaign in June 2023 that is centered on Azure and Google Cloud Platform (GCP) providers, marking the adversary’s growth in focusing on past Amazon Internet Providers (AWS).
The findings come from SentinelOne and Permiso, which mentioned the “campaigns share similarity with instruments attributed to the infamous TeamTNT cryptojacking crew,” though it emphasised that “attribution stays difficult with script-based instruments.”
In addition they overlap with an ongoing TeamTNT marketing campaign disclosed by Aqua known as Silentbob that leverages misconfigured cloud providers to drop malware as a part of what’s mentioned to be a testing effort, whereas additionally linking SCARLETEEL assaults to the menace actor, citing infrastructure commonalities.
“TeamTNT is scanning for credentials throughout a number of cloud environments, together with AWS, Azure, and GCP,” Aqua famous.
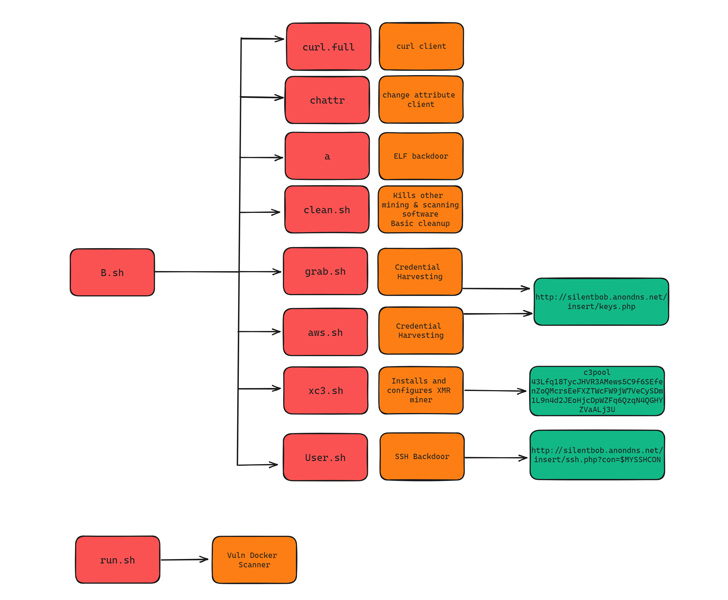
The assaults, which single out public-facing Docker cases to deploy a worm-like propagation module, are a continuation of an intrusion set that beforehand focused Jupyter Notebooks in December 2022.
As many as eight incremental variations of the credential harvesting script have been found between June 15, 2023, and July 11, 2023, indicating an actively evolving marketing campaign.
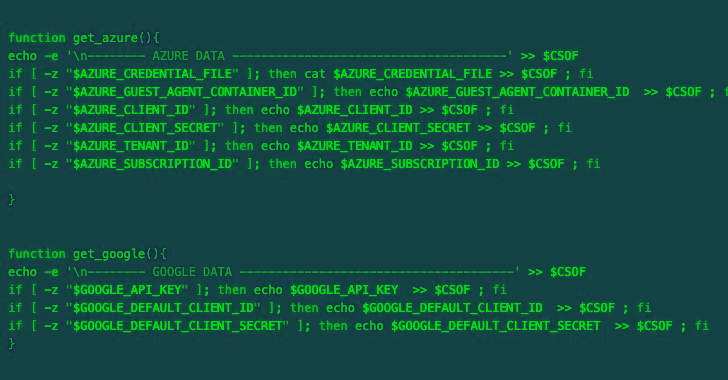
The newer variations of the malware are designed to collect credentials from AWS, Azure, Google Cloud Platform, Censys, Docker, Filezilla, Git, Grafana, Kubernetes, Linux, Ngrok, PostgreSQL, Redis, S3QL, and SMB. The harvested credentials are then exfiltrated to a distant server underneath the menace actor’s management.
SentinelOne mentioned the credentials assortment logic and the recordsdata focused bears similarities to a Kubelet-targeting marketing campaign undertaken by TeamTNT in September 2022.
Alongside the shell script malware, the menace actor has additionally been noticed distributing a Golang-based ELF binary that acts as a scanner to propagate the malware to weak targets. The binary additional drops a Golang community scanning utility known as Zgrab.
“This marketing campaign demonstrates the evolution of a seasoned cloud actor with familiarity throughout many applied sciences,” safety researchers Alex Delamotte, Ian Ahl, and Daniel Bohannon mentioned. “The meticulous consideration to element signifies the actor has clearly skilled loads of trial and error.”
“This actor is actively tuning and bettering their instruments. Based mostly on the tweaks noticed throughout the previous a number of weeks, the actor is probably going making ready for bigger scale campaigns.”
Extra connections between SCARLETEEL and TeamTNT emerge
Defend Towards Insider Threats: Grasp SaaS Safety Posture Administration
Fearful about insider threats? We have got you coated! Be part of this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Safety Posture Administration.
“From what we learn about SCARLETEEL, there’s demonstrable overlap in strategies between these TeamTNT-like campaigns,” Delamotte instructed The Hacker Information. “The SilentBob marketing campaign usually achieves entry, steals credentials, conducts reconnaissance on related providers and methods. SCARLETEEL obtained credentials from a Terraform configuration file, which is analogous to the SilentBob exercise.”
“Essentially the most dependable hyperlink is the callout from Avigayil Mechtinger at Sysdig: Avi famous the SCARLETEEL 2.0 marketing campaign used a crypto miner with the identical Monero pockets tackle. That is pretty conclusive proof the campaigns are associated.” The pockets tackle in query is 43Lfq18TycJHVR3AMews5C9f6SEfenZoQMcrsEeFXZTWcFW9jW7VeCySDm1L9n4d2JEoHjcDpWZFq6QzqN4QGHYZVaALj3U.
Sysdig nevertheless mentioned that using a standard infrastructure however, a clear-cut attribution to TeamTNT is tough resulting from sure variations in techniques, strategies, and procedures (TTPs).
“There positively is overlap with among the infrastructure utilized by threats resembling SCARLETEEL and TeamTNT,” Michael Clark, director of menace analysis at Sysdig, instructed the publication. “Nevertheless, there are additionally variations with the remainder of the TTPs noticed (i.e. Utilizing a customized AWS endpoint) which makes it tough to do correct attribution to a single menace actor.”