The content material of this put up is solely the duty of the creator. AT&T doesn’t undertake or endorse any of the views, positions, or data offered by the creator on this article.
The place do vulnerabilities match with respect to safety requirements and tips? Was it a protection situation or an interpretation and implementation situation? The place does a product, surroundings, group, or enterprise vertical fail probably the most by way of requirements necessities? These questions are often left unanswered due to the hole between requirements or rules on the one hand, and necessities interpretation and implementation, on the opposite. Licensed merchandise and environments usually endure from safety points that have been imagined to be coated by the necessities of the usual.
In [1], as an illustration, the authors give examples of susceptible merchandise that have been IEC 62443 licensed. In [2], SANS discusses the case of PCI-certified corporations and why they’re nonetheless being breached. This “interpretation hole,” whether or not it manifests within the implementation of necessities or within the evaluation course of, hinders safety and results in the truth that being compliant is just not essentially the identical as being safe.
Admittedly, the interpretation of tips and necessities in requirements, which have a descriptive strategy typically, is just not a straightforward job. Necessities could be moderately generic and vast open to interpretation relying on the context, sources, the present menace panorama, the underlying applied sciences, and so forth. Particular necessities may additionally result in conflicting interpretations relying on the kind of stakeholder, which can inevitably have an effect on the implementation facet.
Risk modeling is one method to keep away from shortcomings (and even doable shortcuts) within the implementation of requirements, and the group’s personal safety insurance policies. Consider menace modeling as an enforcement mechanism for the correct implementation of necessities. The rationale that is the case is easy; menace modeling thinks of the necessities by way of related threats to the system, and determines mitigations to cut back or fully keep away from the related dangers. Consequently, every requirement is mapped to a set of threats and mitigations that covers related use circumstances below particular situations or context, e.g., what are the belief boundaries, protocols and applied sciences below use or consideration, third-party interactions, dataflows, knowledge storage, and so forth.
That is turning into vital these days since, in terms of technical necessities, the priority about their interpretation nonetheless persists even when corporations have been audited towards them. Within the following, the offered knowledge evaluation makes the hyperlink between disclosed vulnerabilities in Industrial Management Methods (ICS) and the technical necessities reported within the ‘gold normal’ of requirements on this space, specifically the IEC 62443. It reveals the problem of satisfying the necessities in broad phrases and the necessity for extra particular context and processes.
CISA ICS advisories’ mapping
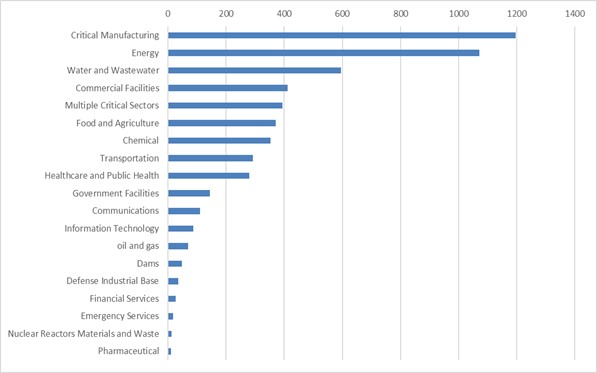
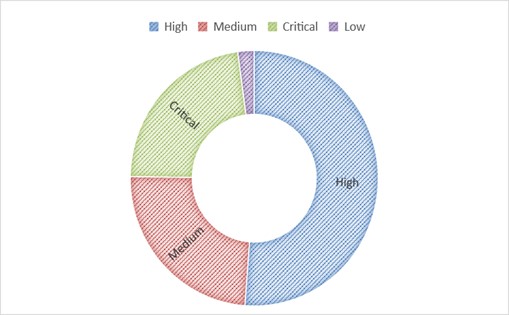
The evaluation of CISA ICS advisories knowledge, representing near 2,5K advisories launched between 2010 and mid-2023 [3], reveals the extent of the problem an implementer or an assessor is confronted with. Desk 1 presents the highest weaknesses and the related rely of advisories in addition to IEC 62443 necessities’ mapping. Affected sectors, the CVSS severity distribution, and high weaknesses per sector are additionally reported; in Figures 1 and a pair of, and Desk 2.
Desk 1. High weaknesses in CISA’s ICS advisories and their IEC 62443 mapping.
|
Weak point |
Identify |
Variety of advisories |
IEC 62443 technical requirement |
|
CWE-20 |
Improper Enter Validation |
266 |
SR/CR 3.5 – Enter validation |
|
CWE-121 |
Stack-based Buffer Overflow |
257 |
|
|
CWE-79 |
Improper Neutralization of Enter Throughout Internet Web page Technology (‘Cross-site Scripting’) |
205 |
|
|
CWE-119 |
Improper Restriction of Operations inside the Bounds of a Reminiscence Buffer |
185 |
|
|
CWE-284 |
Improper Entry Management |
159 |
FR1 – Identification and authentication management (IAC)
FR2 – Use management (UC) |
|
CWE-125 |
Out-of-bounds Learn |
158 |
SR/CR 3.5 – Enter validation |
|
CWE-22 |
Improper Limitation of a Pathname to a Restricted Listing (‘Path Traversal’) |
149 |
|
|
CWE-400 |
Uncontrolled Useful resource Consumption |
145 |
SR/CR 7.1 – Denial of service safety
SR/CR 7.2 – Useful resource administration |
|
CWE-787 |
Out-of-bounds Write |
139 |
SR/CR 3.5 – Enter validation |
|
CWE-287 |
Improper Authentication |
137 |
SR/CR 1.1 – Human person identification and authentication
SR/CR 1.2 – Software program course of and machine identification and authentication |
|
CWE-122 |
Heap-based Buffer Overflow |
128 |
SR/CR 3.5 – Enter validation |
|
CWE-200 |
Publicity of Delicate Info to an Unauthorized Actor |
115 |
FR4 – Knowledge confidentiality (DC)
SR/CR 3.7 – Error dealing with |
|
CWE-798 |
Use of Arduous-coded Credentials |
101 |
SR/CR 1.5 – Authenticator administration |
|
CWE-306 |
Lacking Authentication for Crucial Perform |
98 |
SR/CR 1.1 – Human person identification and authentication
SR/CR 1.2 – Software program course of and machine identification and authentication
SR/CR 2.1 – Authorization enforcement |
|
CWE-352 |
Cross-Web site Request Forgery (CSRF) |
84 |
SR/CR 1.4 – Identifier administration |
|
CWE-89 |
Improper Neutralization of Particular Components Utilized in an SQL Command (‘SQL Injection’) |
81 |
SR/CR 3.5 – Enter validation |
|
CWE-319 |
Cleartext Transmission of Delicate Info |
75 |
SR/CR 4.1 – Info confidentiality |
|
CWE-427 |
Uncontrolled Search Path Aspect |
64 |
SR/CR 3.5 – Enter validation
CR 3.4 – Software program and data integrity |
|
CWE-120 |
Buffer Copy with out Checking Dimension of Enter (‘Traditional Buffer Overflow’) |
62 |
SR/CR 3.5 – Enter validation |
|
CWE-522 |
Insufficiently Protected Credentials |
62 |
SR/CR 1.5 – Authenticator administration |
|
Determine 1. Variety of vulnerabilities per sector |
|
Determine 2. CVSS severity distribution. |
Desk 2. High weaknesses per sector.
|
Sector |
High Weak point |
Identify |
Variety of advisories |
|
Crucial Manufacturing |
CWE-121 |
Stack-based Buffer Overflow |
175 |
|
Power
|
CWE-20 |
Improper Enter Validation |
147 |
|
Water and Wastewater |
CWE-20 |
Improper Enter Validation |
87 |
|
Industrial Amenities |
CWE-79 |
Improper Neutralization of Enter Throughout Internet Web page Technology (‘Cross-site Scripting’) |
42 |
|
Meals and Agriculture |
CWE-20 |
Improper Enter Validation |
55 |
|
Chemical |
CWE-20 |
Improper Enter Validation |
54 |
|
Healthcare and Public Well being |
CWE-284 |
Improper Entry Management |
32 |
|
Transportation |
CWE-121 |
Stack-based Buffer Overflow |
31 |
|
Oil and fuel |
CWE-119 |
Improper Restriction of Operations inside the Bounds of a Reminiscence Buffer |
18 |
|
Authorities Amenities |
CWE-121 |
Stack-based Buffer Overflow |
18 |
Guiding necessities’ interpretation
Desk 1 reveals the numerous ranges of abstraction the vulnerabilities map to. This is among the important points resulting in the elevated complexity related to the interpretation of necessities; for each the implementation and the evaluation. Whereas a excessive degree of granularity permits for the definition of wanted safety mechanisms, a low degree of granularity through the interpretation and implementation is important because it permits for a greater understanding of all of the sorts of threats or failures {that a} particular system is perhaps topic to, e.g., given a deployment mannequin or an underlying expertise.
The case of the “Enter validation” requirement is revealing, with eleven of the highest twenty weaknesses in Desk 1 falling below it. On the floor, enter validation is moderately easy; analyze inputs and disallow something that may be thought-about unsuitable. In follow, nevertheless, the variety of properties of the information and enter use circumstances to probably validate could be daunting. It may additionally be arduous, and even unattainable, to flush out all doable nook circumstances. The IEC 62443 “enter validation” requirement is kind of generic and encapsulates two CWE classes; “Validate Inputs” [4] and “Reminiscence Buffer Errors” [5]. It’s then important to have a transparent understanding of the goal software or system to have the ability to determine related threats below every requirement and tips on how to stop them, i.e., obtain the stated requirement.
Then again, the “Improper entry management” weak point [6] can be an attention-grabbing use case. This can be very high-level and maps to 2 foundational necessities of the IEC 62443. This highlights a difficulty in vulnerability experiences, the place high-level abstraction weaknesses are being misused in disclosure experiences. Extra particular weaknesses associated to the type of entry management concerned would have been extra acceptable, e.g., lacking or weak authentication, lacking or incorrect authorization, and so forth. This isn’t helpful for development evaluation, particularly on how real-world vulnerabilities relate to technical necessities in requirements and rules.
Risk modeling is useful in each circumstances. Software program builders, system architects, and safety professionals can perceive the necessities and tackle the predictable safety points that fall below them, given particular assumptions concerning the software or the system setup. As well as, present menace modeling instruments can pace up the method by producing the related threats and their mitigations routinely, together with primarily based on menace intelligence knowledge. The set of mitigations may also be tailor-made to fulfill totally different wants; as an illustration, the energy of a possible adversary, as is the case within the IEC 62443 normal, the place 4 safety ranges are outlined. These safety ranges (1 to 4) outline technical necessities, together with requirement enhancements, with a view to counter totally different ranges of threat.
I imagine that by utilizing menace modeling as a framework, the interpretation and mapping of necessities into implementation and deployment measures turn into extra predictable. It is going to additionally give builders and system architects a greater likelihood of extra full protection and correct description of what the necessities must be, given the goal system context, its dependencies, and the present menace panorama.
The visitor creator of this weblog is a safety researcher at iriusrisk.com.
References
[1] https://arxiv.org/pdf/2303.12340.pdf
[2] https://www.sans.org/white-papers/36497/
[3] https://www.cisa.gov/news-events/cybersecurity-advisories
[4] https://cwe.mitre.org/knowledge/definitions/1019.html