The protection sector in Ukraine and Jap Europe has been focused by a novel .NET-based backdoor referred to as DeliveryCheck (aka CAPIBAR or GAMEDAY) that is able to delivering next-stage payloads.
The Microsoft menace intelligence crew, in collaboration with the Laptop Emergency Response Crew of Ukraine (CERT-UA), attributed the assaults to a Russian nation-state actor referred to as Turla, which can be tracked below the names Iron Hunter, Secret Blizzard (previously Krypton), Uroburos, Venomous Bear, and Waterbug. It is linked to Russia’s Federal Safety Service (FSB).
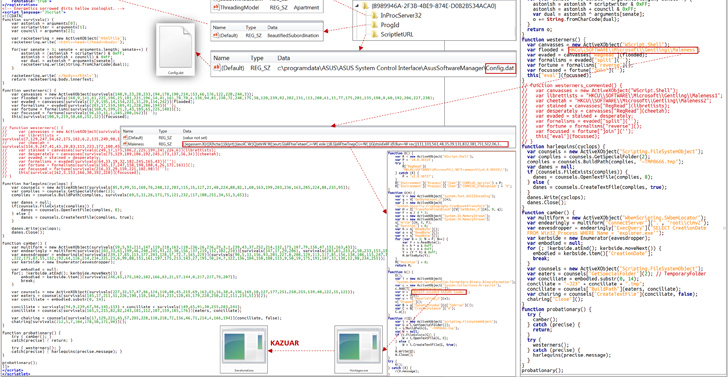
“DeliveryCheck is distributed through e-mail as paperwork with malicious macros,” the corporate stated in a sequence of tweets. “It persists through a scheduled activity that downloads and launches it in reminiscence. It additionally contacts a C2 server to retrieve duties, which might embrace the launch of arbitrary payloads embedded in XSLT stylesheets.”
Profitable preliminary entry can be accompanied in some circumstances by the distribution of a identified Turla implant dubbed Kazuar, which is provided to steal utility configuration recordsdata, occasion logs, and a variety of information from net browsers.
The last word aim of the assaults is to exfiltrate messages from the Sign messaging app for Home windows, enabling the adversary to entry delicate conversations, paperwork, and pictures on focused programs.
A noteworthy side of DeliveryCheck is its capability to breach Microsoft Alternate servers to put in a server-side element utilizing PowerShell Desired State Configuration (DSC), a PowerShell administration platform that helps directors to automate the configuration of Home windows programs.
“DSC generates a Managed Object Format (MOF) file containing a PowerShell script that masses the embedded .NET payload into reminiscence, successfully turning a authentic server right into a malware C2 middle,” Microsoft defined.
Protect In opposition to Insider Threats: Grasp SaaS Safety Posture Administration
Anxious about insider threats? We have got you lined! Be a part of this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Safety Posture Administration.
The disclosure comes because the Cyber Police of Ukraine dismantled an enormous bot farm with greater than 100 people allegedly spreading hostile propaganda justifying the Russian invasion, leaking private info belonging to Ukrainian residents, and interesting in numerous fraud schemes.
As a part of the operation, searches had been carried out in 21 places, resulting in the seizure of laptop tools, cell phones, greater than 250 GSM gateways, and about 150,000 SIM playing cards belonging to completely different cellular operators.