The content material of this put up is solely the duty of the writer. AT&T doesn’t undertake or endorse any of the views, positions, or info offered by the writer on this article.
Within the realm of knowledge safety, there exists a fascinating method often called whitespace steganography. In contrast to conventional strategies of encryption, whitespace steganography permits for the hiding of delicate info inside whitespace characters, corresponding to areas, tabs, and line breaks.
This inconspicuous strategy to information concealment has gained vital consideration in recent times as a way of safe communication. On this weblog, we are going to delve into the world of whitespace steganography, exploring its strategies, purposes, instruments, and moral issues for academic functions.
Whitespace steganography is a technique of concealing information inside whitespace characters which can be usually neglected or deemed insignificant. By strategically modifying the frequency or association of whitespace characters, hidden messages could be embedded inside a textual content doc. To the bare eye, the doc seems regular, however these conscious of the encoding method can retrieve the hid info.
In whitespace steganography, a number of strategies are employed to hide info successfully. These strategies embrace altering the frequency of whitespace characters, corresponding to including or eradicating areas, tabs, or line breaks. One other strategy includes manipulating the association of whitespace characters to characterize encoded information. Varied algorithms, such because the Least Important Bit (LSB) method, could be utilized to embed and extract hidden messages from whitespace.
Whitespace steganography finds purposes in a spread of eventualities the place safe communication and information safety are paramount. Some frequent use circumstances embrace:
- Covert communication: Whitespace steganography permits people to alternate delicate info discreetly, evading detection and interception.
- Doc safety: Concealing vital info inside whitespace characters may also help shield delicate paperwork from unauthorized entry or tampering.
- Digital watermarking: Hidden inside whitespace, digital watermarks could be embedded in photographs or paperwork to guard mental property or confirm authenticity.
Quite a few open-source instruments can be found that facilitate whitespace steganography. These instruments present options and functionalities for encoding and decoding hidden messages inside whitespace characters. Notable examples embrace Snow, Steghide, OpenStego, and Whitespace. There are additionally closed supply or business whitespace steganography instruments that provide superior capabilities and extra security measures. These instruments usually present user-friendly interfaces, encryption algorithms, and integration with different safety applied sciences. Some in style closed-source instruments embrace SilentEye, OutGuess, and Masker.
On this weblog, we are going to use Snow (Steganographic Nature of Whitespace) to see a working instance of whitespace steganography -the instrument could be downloaded from right here.
As per the documentation, The Snow program runs in two modes – message concealment, and message extraction. Throughout concealment, the next steps are taken.
Message -> non-compulsory compression -> non-compulsory encryption -> concealment in textual content
Extraction reverses the method.
Extract information from textual content -> non-compulsory decryption -> non-compulsory uncompression -> message
Now, let’s look on a working instance.
We’ve downloaded the 32-bit model of Snow, and we’ve ensured that Java runtime surroundings (JRE) is put in on our system. As soon as every part is in place extract Snow to the specified listing. To run Snow, you have to to run command immediate as administrator and transfer to the listing the place you could have extracted Snow.
As soon as you’re within the listing, you have to an enter file (we’re utilizing a textual content file for demonstration)
Now, allow us to attempt to conceal a message “Hiya There.” utilizing Snow.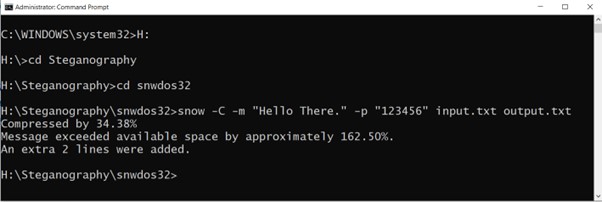
Within the above instance we hid a message within the enter file and created an output file utilizing Snow (to keep away from any contradiction we saved the enter file in identical listing as Snow)
Within the above instance we used -C for compression, -p for password and -m for message.
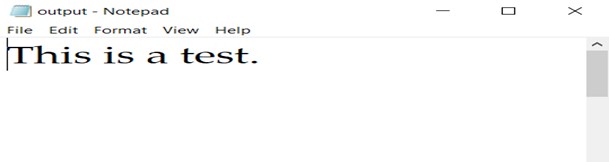
Now allow us to check out the output file.
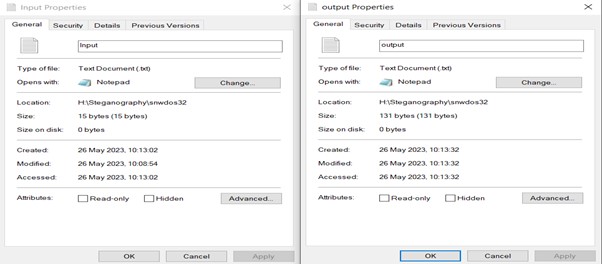
Now let’s see if there are any variations in measurement of enter and output information.
We are able to observe that there’s a distinction in measurement – nonetheless, after we open the output file it seems the identical because the enter file.
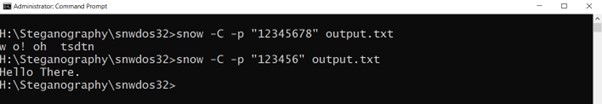
Now, let’s attempt to learn the hidden message. Let’s run the command immediate as administrator and transfer to the listing of Snow the place the output file is situated.
So, I attempted with fallacious password as soon as after which with the proper password as you may see under:
This was an illustration of whitespace steganography utilizing Snow and is solely for academic and analysis functions to know the way it works in actual life eventualities.
Steganalysis: Detecting steganography
Steganalysis refers back to the detection and evaluation of hidden messages inside digital content material. Whereas whitespace steganography could be troublesome to detect, specialised strategies and instruments can be found to determine potential cases of concealment. Steganalysis performs an important function in figuring out potential misuse and guaranteeing accountable use of steganography. We’ll dive deep into steganalysis in coming blogs.
Moral utilization and disclosure are essential relating to steganography. You will need to adhere to authorized laws and privateness legal guidelines governing information safety and communication. Whitespace steganography ought to be used responsibly for academic functions solely, emphasizing the significance of acquiring correct consent and guaranteeing moral practices.
Whitespace steganography gives a outstanding strategy to safe communication and information safety. By harnessing the facility of seemingly innocuous whitespace characters, delicate info could be hid inside plain sight. Understanding the strategies, purposes, and instruments related to whitespace steganography permits people to navigate the sphere responsibly. As expertise continues to advance, the way forward for whitespace steganography holds the potential for additional improvements in safe communication and information privateness.