The content material of this submit is solely the accountability of the creator. AT&T doesn’t undertake or endorse any of the views, positions, or data offered by the creator on this article.
Within the huge realm of digital investigations, there exists a captivating approach often called recycle bin forensics. Delving into the depths of this charming subject unveils a world the place seemingly deleted recordsdata can nonetheless reveal their secrets and techniques, permitting digital detectives to reconstruct person actions and uncover useful data. So, let’s embark on a journey to demystify recycle bin forensics and perceive its function within the realm of cybersecurity.
Recycle bin forensics is a specialised department of digital forensics that focuses on the retrieval and evaluation of deleted recordsdata from the recycle bin or trash folder. This intriguing approach holds the potential to unlock a treasure trove of proof, shedding mild on cybercrimes and aiding within the investigation course of.
To understand the intricacies of recycle bin forensics, it is important to understand how the recycle bin capabilities.
Once you delete a file in your pc, it typically finds its solution to the recycle bin or trash folder. It is a handy function that permits you to recuperate by chance deleted recordsdata with a easy click on. However do you know that even after you empty the recycle bin, traces of these recordsdata should linger in your system?
Welcome to the fascinating realm of recycle bin forensics, the place digital detectives can uncover useful data and make clear a person’s actions.
Location of Deleted recordsdata
C:RECYCLED Win 95/98/Me
C:RECYCLER Win NT/2000/ XP
C:$Recycle.bin Win Vista and later
Metadata file
INFO2(Win 95/98/Me)
C:RECYCLERSID*INFO2 (Win NT/2000/XP) (SID denotes safety identifier)
Home windows Vista and later
C:Recycle.binSID*$I******(Comprises Metadata)
C:Recycle.binSID*$R******(Contents of deleted file)
Each recordsdata will probably be renamed to a random 6-character worth. These directories are hidden by default; nevertheless, you’ll be able to entry them utilizing command immediate with elevated privileges (Run as administrator) in your home windows system utilizing command dir /a.
Recycle bin forensics assumes a essential function in digital investigations, enabling legislation enforcement businesses, cybersecurity specialists, and forensic analysts to piece collectively the puzzle. By analyzing deleted recordsdata, forensic professionals can reconstruct a timeline of occasions, unearth very important proof, and recuperate seemingly misplaced information, aiding within the pursuit of justice.
Unveiling the secrets and techniques hidden throughout the recycle bin requires specialised instruments and strategies. Forensic software program empowers investigators to extract deleted recordsdata, even after the recycle bin has been emptied. By way of cautious evaluation of file metadata, paths, and content material, digital detectives can acquire insights into file origins, modifications, and deletions, portray a clearer image of the person’s actions.
One such utility we will probably be utilizing is $IPARSE which could be downloaded right here.
Steps to search out metadata associated to a deleted file ($I****** file)
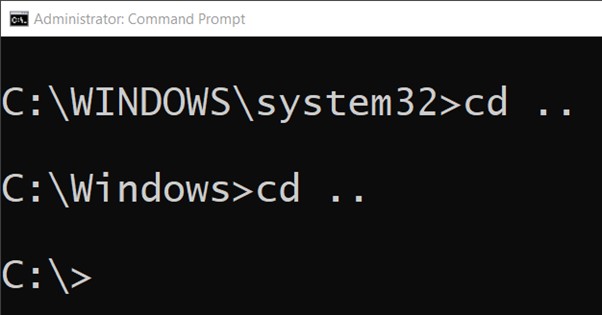
- Run command immediate as administrator
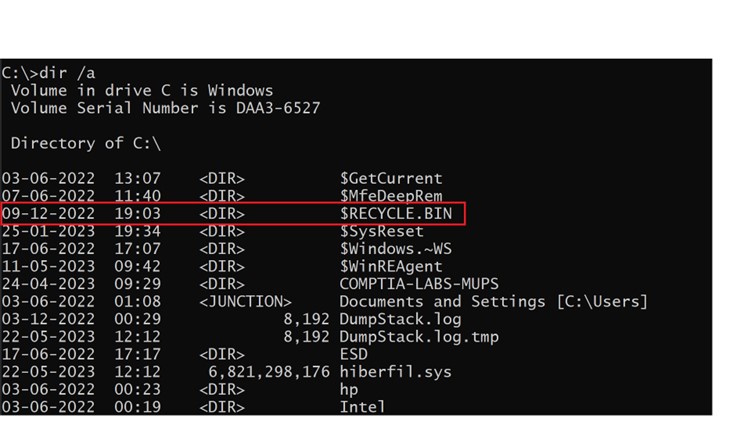
- after that use command dir /a and verify if you’ll be able to see $RECYCLE.BIN listing
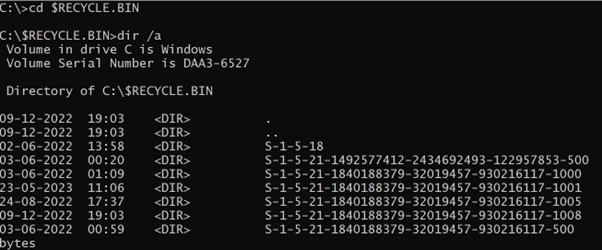
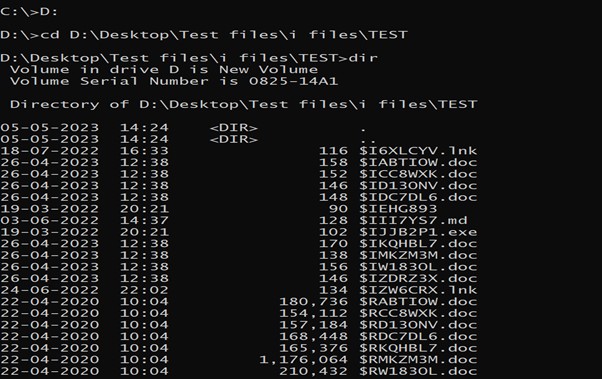
- cd $RECYCLE.BIN to go contained in the listing and use command dir /a
now you will note a number of entries beginning with S within the listing of directories.
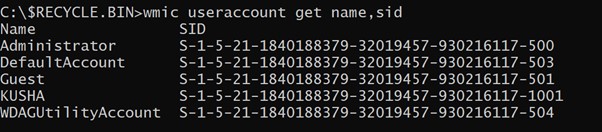
To verify customers related to the SID directories you should utilize command wmic useraccount get identify,sid
It can listing all of the customers related to SID’s. After that replicate any SID by deciding on and utilizing ctrl C (as effectively you should utilize tab key to autocomplete the SID after typing first few characters of SID).
Now, to maneuver into the SID listing:
cd SID (paste the copied worth)
for instance, if the SID listing identify was S-1-5-32
after that use command dir /a to listing the elements of that listing you shall see $I and $R recordsdata. In sure instances, solely $I****** file will probably be out there.
For illustration functions, we’re utilizing recordsdata acquired from different programs.
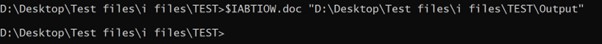
- Now, create a folder and provides a path to repeat the file. Syntax could be file identify “path” ($IABTIOW.doc “D:DesktopTest filesi filesTESTOutput”), you’ll be able to alternatively use the copy command.
- Copy the file/folder identify (whereas contained in the mentioned listing) and duplicate to path (the place you want to copy the mentioned file or folder). The trail could be copied by stepping into folder and clicking the deal with bar – your file will probably be copied and the related software program will attempt to open it, however will not have the ability to open (like photographs app for png/jpeg recordsdata)
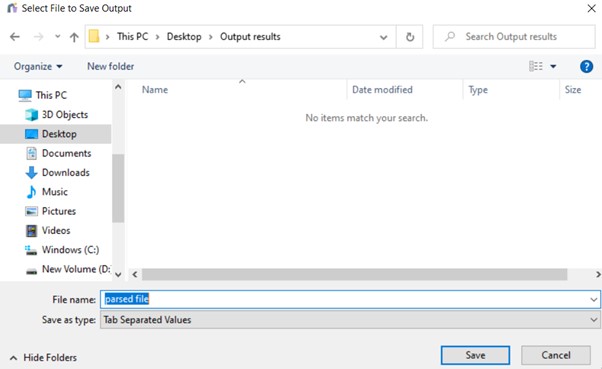
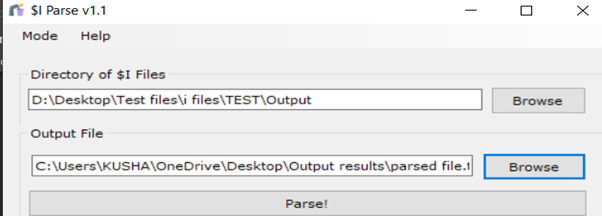
- Extract and run the $Iparse utility you downloaded. Browse the listing/folder you copied $I recordsdata in. Now, browse to the listing the place you wish to put the end result file at and supply a file identify.
Click on on save. After that, it’s best to have the ability to see an interface like beneath:
Then click on parse. It can show the file for you if it has efficiently parsed it – the output file will probably be in .tsv format. You’ll be able to open the .tsv file with notepad or notepad++. Now, it is possible for you to to see particulars pertaining to the mentioned $I file.
Whereas recycle bin forensics is a robust instrument, it’s not with out its challenges and limitations. As time progresses and new recordsdata are created and deleted, older remnants within the recycle bin could also be overwritten, making the restoration of sure deleted recordsdata more difficult and even not possible. Moreover, the effectiveness of recycle bin forensics can differ based mostly on the working system and file system in use, presenting distinctive obstacles.
To guard delicate data and thwart potential restoration by way of recycle bin forensics, implementing safe information deletion practices is significant. Merely emptying the recycle bin gives no assure of everlasting erasure. As a substitute, using specialised file shredding or disk wiping instruments can be sure that deleted information is securely overwritten, rendering it irretrievable.
In conclusion, recycle bin forensics is a outstanding subject that uncovers the hidden remnants of deleted recordsdata, holding the potential to remodel investigations. As we navigate the digital panorama, understanding the ability of recycle bin forensics reminds us of the significance of safeguarding our digital footprint. By way of information, diligence, and safe practices, we will defend our delicate data and fortify the realm of cybersecurity for the advantage of all.