An ongoing Magecart marketing campaign has attracted the eye of cybersecurity researchers for leveraging realistic-looking pretend fee screens to seize delicate knowledge entered by unsuspecting customers.
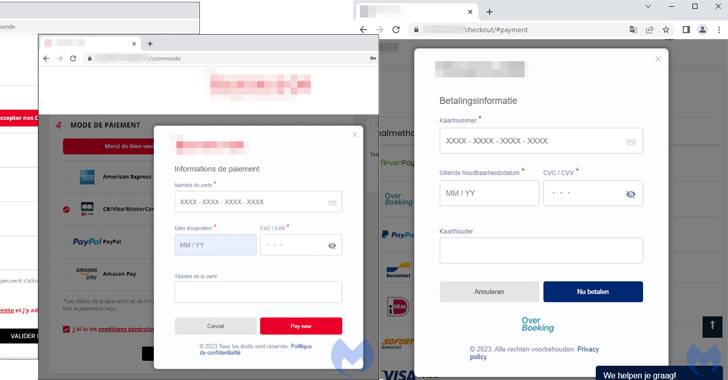
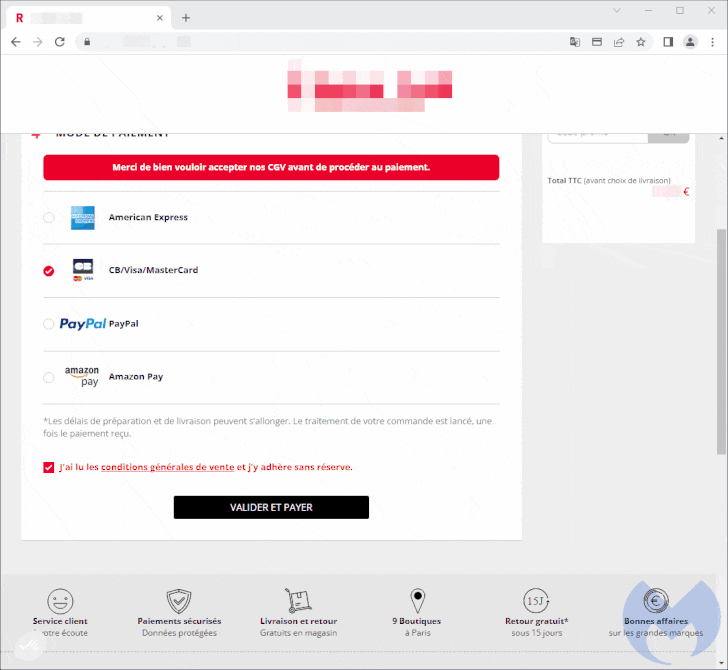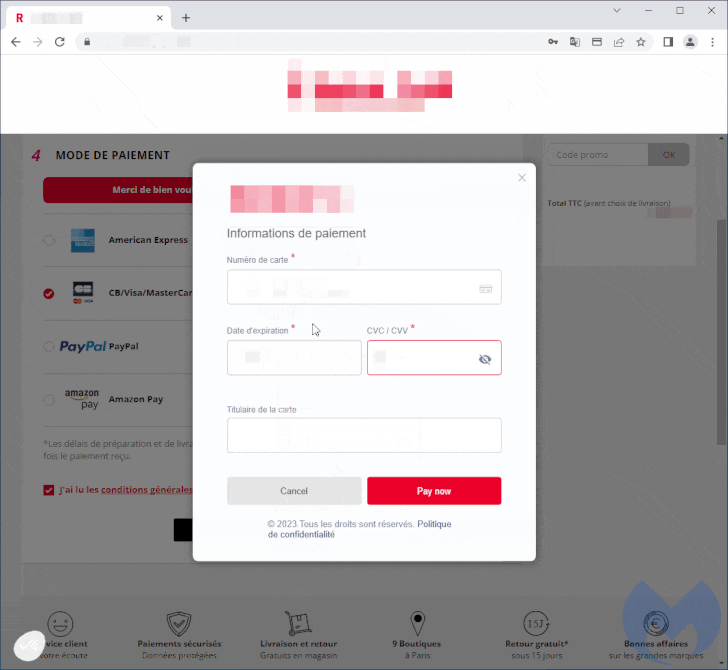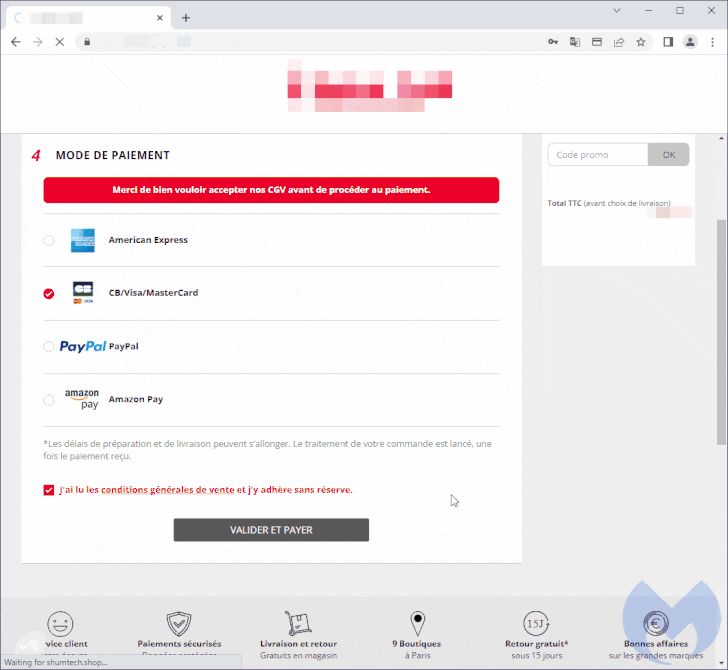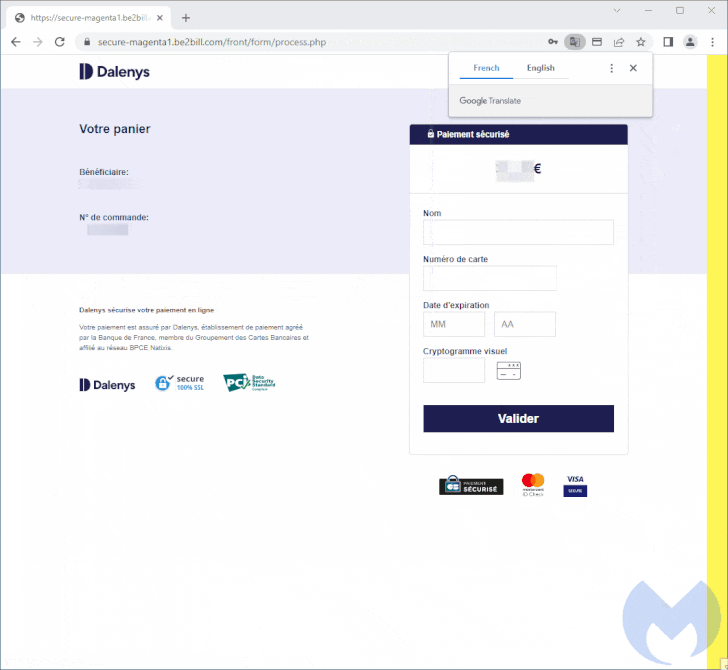
“The menace actor used authentic logos from the compromised retailer and customised an internet aspect often known as a modal to completely hijack the checkout web page,” Jérôme Segura, director of menace intelligence at Malwarebytes, mentioned. “The exceptional factor right here is that the skimmer appears extra genuine than the unique fee web page.”
The time period Magecart is a catch-all that refers to a number of cybercrime teams which make use of on-line skimming methods to steal private knowledge from web sites – mostly, buyer particulars and fee info on e-commerce web sites.
The identify originates from the teams’ preliminary focusing on of the Magento platform. In line with knowledge shared by Sansec, the primary Magecart-like assaults had been noticed as early as 2010. As of 2022, greater than 70,000 shops are estimated to have been compromised with an internet skimmer.
These digital skimming assaults, additionally referred to as formjacking, historically leverage varied sorts of JavaScript trickery to siphon delicate info from web site customers.
The most recent iteration, as noticed by Malwarebytes on an unnamed Parisian journey accent retailer operating on the PrestaShop CMS, concerned the injection of a skimmer referred to as Kritec to intercept the checkout course of and show a pretend fee dialog to victims.
Kritec, beforehand detailed by Akamai and Malwarebytes in February 2023, has been discovered to impersonate reliable third-party distributors like Google Tag Supervisor as an evasion method.
The cybersecurity agency mentioned the skimmer is each advanced and closely obfuscated, with the malicious modal loaded upon deciding on a bank card because the fee choice from the compromised web site.
As soon as the fee card particulars are harvested, a pretend error message about fee cancellation is briefly exhibited to the sufferer earlier than redirecting to the precise fee web page, at which level the fee will undergo.
“The skimmer will drop a cookie which can function a sign that the present session is now marked as accomplished,” Segura defined. “If the person was to return and try the fee once more, the malicious modal would not be displayed.”
Be taught to Cease Ransomware with Actual-Time Safety
Be part of our webinar and discover ways to cease ransomware assaults of their tracks with real-time MFA and repair account safety.
The menace actors behind the operation are mentioned to be utilizing completely different domains to host the skimmer, that are given related names: “[name of store]-loader.js,” suggesting that the assaults are focusing on completely different on-line shops with customized modals.
“Discerning whether or not a web based retailer is reliable has develop into very tough and this case is an efficient instance of a skimmer that will not elevate any suspicion,” Segura mentioned.
The findings come somewhat over two months after Malwarebytes unearthed one other net skimmer that collects browser fingerprint knowledge, equivalent to IP addresses and Consumer-Agent strings, together with bank card info, possible in an try to observe invalid customers equivalent to bots and safety researchers.