Researchers have found a novel assault on the Python Package deal Index (PyPI) repository that employs compiled Python code to sidestep detection by utility safety instruments.
“It could be the primary provide chain assault to reap the benefits of the truth that Python bytecode (PYC) recordsdata may be instantly executed,” ReversingLabs analyst Karlo Zanki mentioned in a report shared with The Hacker Information.
The bundle in query is fshec2, which was faraway from the bundle registry on April 17, 2023, following accountable disclosure on the identical day.
PYC recordsdata are compiled bytecode recordsdata which can be generated by the Python interpreter when a Python program is executed.
“When a module is imported for the primary time (or when the supply file has modified for the reason that present compiled file was created) a .pyc file containing the compiled code must be created in a __pycache__ subdirectory of the listing containing the .py file,” explains the Python documentation.
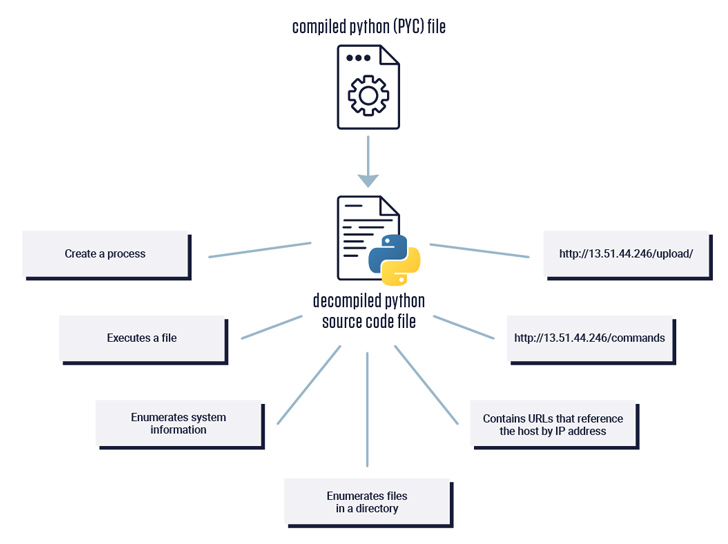
The bundle, per the software program provide chain safety agency, incorporates three recordsdata – _init_.py, major.py, and full.pyc – the final of which harbors malicious performance.
“The entry level of the bundle was discovered within the __init__.py file, which imports a operate from the opposite plaintext file, major.py, which incorporates Python supply code answerable for loading of the Python compiled module situated in one of many different recordsdata, full.pyc,” Zanki identified.
This, in flip, is achieved by making use of the importlib bundle (versus an everyday import) to load and execute the code current within the .pyc file.
An evaluation of the reverse-engineered model of the PYC file reveals that it is configured to gather usernames, hostnames, and listing listings, in addition to fetch instructions to be executed on the host from a hard-coded server (13.51.44[.]246).
🔐 Mastering API Safety: Understanding Your True Assault Floor
Uncover the untapped vulnerabilities in your API ecosystem and take proactive steps in direction of ironclad safety. Be part of our insightful webinar!
ReversingLabs mentioned it additionally noticed the module obtain and run one other Python script that is answerable for fetching new instructions positioned inside a file that may be tweaked at will by the risk actor to concern completely different directions.
Additional examination of the command-and-control server unearthed a misconfiguration that made it doable to obtain recordsdata by their ID, that are numbered in sequential order (ranging from 1), sans any authorization. This means that the assault was more than likely not orchestrated by a classy actor.
The event is a continuation of efforts on the a part of risk actors to undertake completely different obfuscation strategies to be able to evade detection from safety options.
“Loader scripts resembling these found within the fshec2 bundle include a minimal quantity of Python code and carry out a easy motion: loading of a compiled Python module,” Zanki mentioned. “It simply occurs to be a malicious module.”