Govt abstract
On April twenty first, 2023, AT&T Managed Prolonged Detection and Response (MXDR) investigated an tried ransomware assault on one in every of our shoppers, a house enchancment enterprise. The investigation revealed the attacker used AuKill malware on the shopper’s print server to disable the server’s put in EDR answer, SentinelOne, by brute forcing an administrator account and downgrading a driver to a susceptible model.
AuKill, first recognized by Sophos X-Ops researchers in June 2021, is a classy malware designed to focus on and neutralize particular EDR options, together with SentinelOne and Sophos. Distributed as a dropper, AuKill drops a susceptible driver named PROCEXP.SYS (from Course of Explorer launch model 16.32) into the system’s C:WindowsSystem32drivers folder. This malware has been noticed within the wild, utilized by ransomware teams to bypass endpoint safety measures and successfully unfold ransomware variants similar to Medusa Locker and Lockbit on susceptible programs.
On this case, SentinelOne managed to isolate a lot of the malicious recordsdata earlier than being disabled, stopping a full-scale ransomware incident. Consequently, AT&T MXDR discovered no proof of information exfiltration or encryption. Regardless of this, the shopper opted to rebuild the print server as a precautionary measure. This research gives an in-depth evaluation of the assault and presents suggestions to mitigate the danger of future assaults.
Investigating the primary part of the assault
Preliminary intrusion
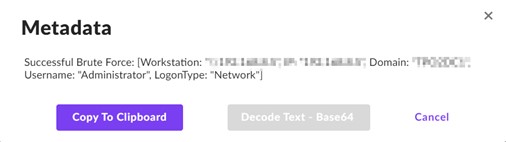
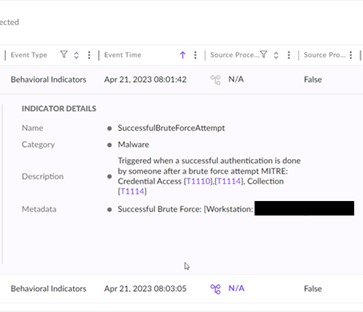
The focused asset was the print server, which we discovered uncommon. Nevertheless, upon additional investigation we concluded the attacker misidentified the asset as a Area Controller (DC), because it had just lately been repurposed from a DC to a print server. The attacker wanted each native administrator credentials and kernel-level entry to efficiently run AuKill and disable SentinelOne on the asset. To achieve these native administrator credentials, the attacker efficiently brute-forced an administrator account. Shortly after the compromise, this account was noticed making unauthorized registry adjustments.
Establishing a beachhead
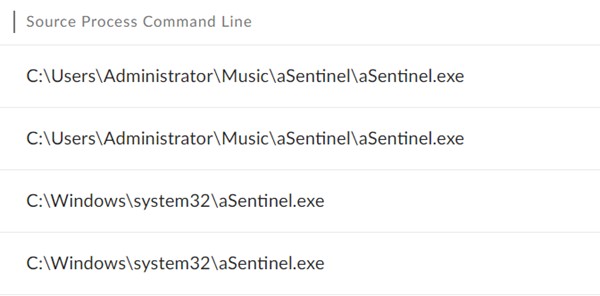
After compromising the native administrator account, the attackers used the “UsersAdministratorMusicaSentinel” folder as a staging space for subsequent phases of their assault. All AuKill-related binaries and scripts had been executed from this path, with the innocuous “Music” folder identify serving to to hide their malicious actions.
AuKill malware has been discovered to function utilizing two Home windows providers named “aSentinel.exe” and “aSentinelX.exe” in its SentinelOne variant. In different variants, it targets completely different EDRs, similar to Sophos, by using corresponding Home windows providers like “aSophos.exe” and “aSophosX.exe”.
Establishing persistence
We additionally found “aSentinel.exe” operating from “C:Windowssystem32”, indicating that the attackers tried to determine a foothold on the compromised server. Malware authors ceaselessly goal the system32 folder as a result of it’s a trusted location, and safety software program might not scrutinize recordsdata inside it as intently as these in different areas. This might help malware bypass safety measures and stay hidden. It’s doubtless that the malware was initially positioned within the “UsersAdministratorMusicaSentinel” listing and later copied to the system32 listing for persistence.
Community reconnaissance
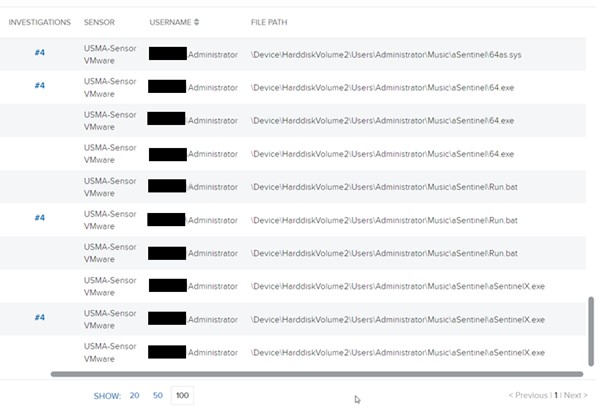
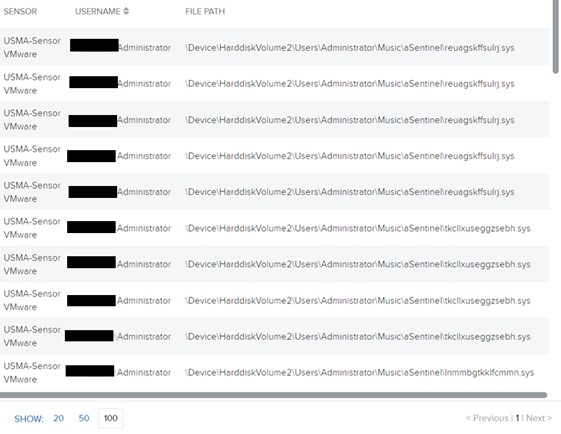
Our investigation additionally revealed that PCHunter, a publicly accessible utility beforehand exploited in ransomware incidents like Dharma, was operating from the “UsersAdministratorMusicaSentinel” listing. This implies that the attackers used PCHunter as a reconnaissance software to survey the shopper’s community earlier than deploying the EDR killer malware. Moreover, PCHunter allows risk actors to terminate applications and interface instantly with the Home windows kernel, which aligns with the wants of the attacker. We noticed PCHunter producing a number of randomly named .sys recordsdata, as illustrated under:
Stopping knowledge restoration
We discovered that the attacker deleted shadow quantity copies from the print server. Home windows creates these copies to revive recordsdata and folders to earlier variations in case of information loss. By eradicating the shadow copies, the attacker was trying to make it tougher for our shopper to recuperate their recordsdata in the event that they had been efficiently encrypted. Though no ransomware was deployed, the deletion of shadow copies reveals the attackers’ intentions. This info, along with the utilization of PCHunter and the staging of the EDR killer malware, paints a extra full image of the attacker’s goals and ways.
Bypassing native Home windows safety
With all these items in place, the attacker final wanted to amass kernel-level entry. Regardless of gaining administrator rights early on, the attacker didn’t have sufficient management over the system to kill SentinelOne at the moment. EDR options are categorized as important by Home windows and are shielded from being turned off by attackers after they escalate privileges. To efficiently circumvent these safeguards, the attacker would want to journey one stage deeper into the working system and acquire kernel-level entry to the machine.
Investigating the second part of the assault
Dropping the susceptible driver
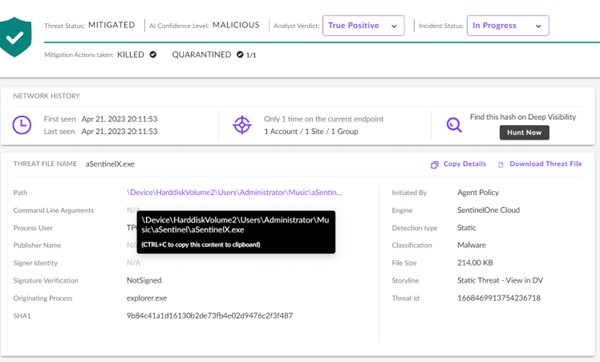
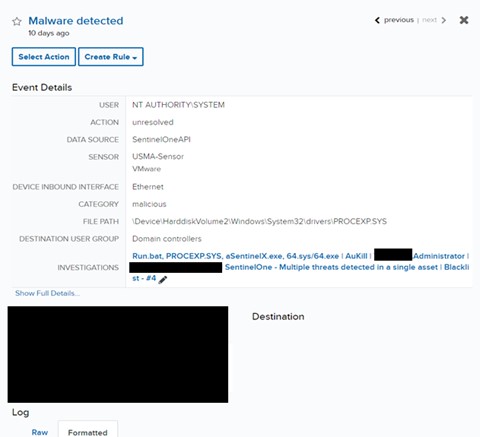
Our group found that AuKill had changed the present Course of Explorer driver, PROCEXP152.sys, with an outdated and susceptible model named PROCEXP.SYS (from Course of Explorer launch model 16.32), situated within the C:WindowsSystem32drivers listing. The alarm screenshot under demonstrates how AuKill swapped the present driver with this older model, making the system inclined to additional exploitation.
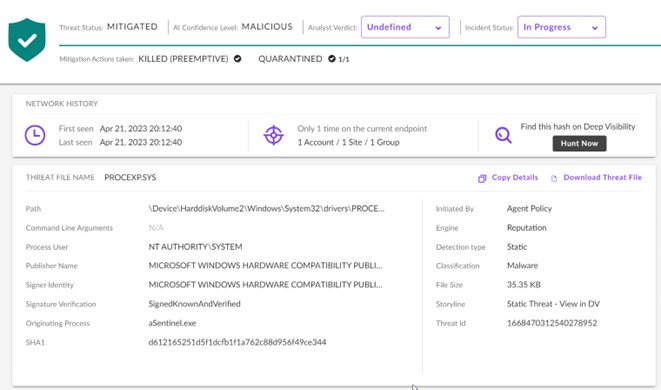
Home windows incorporates a safety function referred to as Driver Signature Enforcement, which ensures that kernel-mode drivers are signed by a legitimate code signing authority earlier than they’ll run. To bypass this safety measure, the attackers exploited the insecure PROCEXP.SYS driver, which was produced and signed by Microsoft at an earlier date. As demonstrated within the SentinelOne screenshot under, the motive force is signed and verified by Microsoft. Moreover, the originating course of was aSentinel.exe, an executable created to disable SentinelOne.
Buying kernel-level entry
Course of Explorer, a official system monitoring software developed by Microsoft’s Sysinternals group, allows directors to look at and handle functions’ ongoing processes, in addition to their related threads, handles, and DLLs.
Upon startup, Course of Explorer hundreds a signed kernel-mode driver, facilitating interplay with the system’s kernel, which is chargeable for managing {hardware} and sources. Usually, that driver is PROCEXP152.sys. The attacker changed the PROCEXP152.sys driver on the print server with the exploitable PROCEXP.SYS, using what is called a BYOVD (Carry Your Personal Weak Driver) assault. The attacker used this methodology to take advantage of the now susceptible kernel mode driver to realize the kernel-level entry they wanted to efficiently kill SentinelOne.
Killing SentinelOne
The kernel-mode driver utilized by Course of Explorer has the distinctive potential to terminate handles which can be inaccessible even to directors. A deal with is an identifier that corresponds to a selected useful resource opened by a course of, similar to a file or a registry key. At this level, AuKill hijacked Course of Explorer’s kernel driver to particularly goal protected handles related to SentinelOne processes operating on the print server. The SentinelOne processes had been killed when the protected course of handles had been closed, rendering the EDR powerless. AuKill then generated a number of threads to make sure that these EDR processes remained disabled and didn’t resume. Every thread focused on a sure SentinelOne part and usually checked to see if the focused processes had been energetic. In the event that they had been, AuKill would terminate them. SentinelOne was out of the way in which and now not an impediment to the attacker.
Response
Buyer interplay
At this level, the attacker had gained privileged entry to the asset, deployed their malware, and efficiently killed the endpoint safety answer, SentinelOne. Based mostly on the Cyber Kill Chain methodology developed by Lockheed Martin, we are able to conclude that the attacker had now efficiently reached the “Command and Management” stage. Nevertheless, the attacker didn’t attain the “Actions on Targets” stage, as SentinelOne managed to disrupt ransomware deployment sufficient earlier than it was killed to forestall any extra injury.
Any makes an attempt to re-deploy malware or transfer laterally following the disablement of the EDR had been thwarted by our group, who swiftly alerted the shopper to the exercise and suggested that the asset be taken offline and remoted from the remainder of the community. Our group knowledgeable the shopper that the shadow copies had been deleted and SentinelOne had been turned off on their print server. After having our risk hunters totally evaluate their setting, w e reassured the shopper that no delicate info was exfiltrated or encrypted. In response to the assault, the shopper moved to rebuild their print server and reinstall SentinelOne.
Suggestions
As BYOVD assaults to bypass EDR software program change into extra widespread, we strongly advise blacklisting outdated drivers with a recognized historical past of exploitation. Moreover, we encourage our shoppers to take care of a list of the drivers put in on their programs, making certain they continue to be present and safe. Lastly, we advocate bolstering the safety of administrator accounts to defend towards brute drive assaults, because the incident detailed on this weblog submit couldn’t have transpired with out the preliminary privileged consumer compromise.